The yara rules used to apply this method require the name of the observed file. Yara allows the file name to be passed via an external variable like in the following listing.
yara32.exe -d filename=iexplore.exe inverse-matching.yar iexplore.exe
But we have to define and pass this “filename” variable for every file we analyse while walking the directory tree.
So – what do we do?
First – we need a powershell script that walks a directory tree and feeds each file with an “.exe” extension together with the rule set and the file name as external variable to a yara32.exe. You could copy the script and paste it directly to the command line but I would recommend the following:
Prepare a folder with the following content:
- The powershell script as listed below – name it “inverse-scan.ps1”
- The ruleset listed below as “inverse-matching.yar”
- A version of Yara for Windows
- A batch script that invokes the powershell script with some parameters named “runit.bat”
The final result looks like this:
Inverse Yara Matching Script Set
You can copy that folder to the target system, take it with you on a USB drive or provide a network share with its contents.
inverse-scan.ps1
Get-ChildItem -Recurse -filter *.exe C:\Windows 2> $null |
ForEach-Object { Write-Host -foregroundcolor "green" "Scanning"$_.FullName $_.Name; ./yara32.exe -d filename=$_.Name inverse-matching.yar $_.FullName 2> $null }
runit.bat
@ECHO OFF powershell -ExecutionPolicy ByPass -File ./inverse-scan.ps1
inverse-matching.yar
rule iexplore_ANOMALY {
meta:
author = "Florian Roth"
description = "Abnormal iexplore.exe - typical strings not found in file"
date = "23/04/2014"
score = 55
strings:
$upd_magic = { 44 43 }
$win2003_win7_u1 = "IEXPLORE.EXE" wide nocase
$win2003_win7_u2 = "Internet Explorer" wide fullword
$win2003_win7_u3 = "translation" wide fullword nocase
$win2003_win7_u4 = "varfileinfo" wide fullword nocase
condition:
not ( $upd_magic at 0 ) and not 1 of ($win*) and filename matches /iexplore\.exe/is
}
rule svchost_ANOMALY {
meta:
author = "Florian Roth"
description = "Abnormal svchost.exe - typical strings not found in file"
date = "23/04/2014"
score = 55
strings:
$upd_magic = { 44 43 }
$win2003_win7_u1 = "svchost.exe" wide nocase
$win2003_win7_u3 = "coinitializesecurityparam" wide fullword nocase
$win2003_win7_u4 = "servicedllunloadonstop" wide fullword nocase
$win2000 = "Generic Host Process for Win32 Services" wide fullword
$win2012 = "Host Process for Windows Services" wide fullword
condition:
filename matches /svchost\.exe/is and not 1 of ($win*) and not ( $upd_magic at 0 )
}
rule explorer_ANOMALY {
meta:
author = "Florian Roth"
description = "Abnormal explorer.exe - typical strings not found in file"
date = "27/05/2014"
score = 55
strings:
$upd_magic = { 44 43 }
$s1 = "EXPLORER.EXE" wide fullword
$s2 = "Windows Explorer" wide fullword
condition:
filename matches /explorer\.exe/is and not 1 of ($s*) and not ( $upd_magic at 0 )
}
rule sethc_ANOMALY {
meta:
description = "Sethc.exe has been replaced - Indicates Remote Access Hack RDP"
author = "F. Roth"
reference = "http://www.emc.com/collateral/white-papers/h12756-wp-shell-crew.pdf"
date = "2014/01/23"
score = 70
strings:
$upd_magic = { 44 43 }
$s1 = "stickykeys" fullword nocase
$s2 = "stickykeys" wide nocase
$s3 = "Control_RunDLL access.cpl" wide fullword
$s4 = "SETHC.EXE" wide fullword
condition:
filename matches /sethc\.exe/ and not 1 of ($s*) and not ( $upd_magic at 0 )
}
rule Utilman_ANOMALY {
meta:
author = "Florian Roth"
description = "Abnormal utilman.exe - typical strings not found in file"
date = "01/06/2014"
score = 55
strings:
$upd_magic = { 44 43 }
$win7 = "utilman.exe" wide fullword
$win2000 = "Start with Utility Manager" fullword wide
$win2012 = "utilman2.exe" fullword wide
condition:
filename matches /utilman\.exe/is and not 1 of ($win*) and not ( $upd_magic at 0 )
}
rule osk_ANOMALY {
meta:
author = "Florian Roth"
description = "Abnormal osk.exe (On Screen Keyboard) - typical strings not found in file"
date = "01/06/2014"
score = 55
strings:
$upd_magic = { 44 43 }
$s1 = "Accessibility On-Screen Keyboard" wide fullword
$s2 = "\\oskmenu" wide fullword
$s3 = "&About On-Screen Keyboard..." wide fullword
$s4 = "Software\\Microsoft\\Osk" wide
condition:
filename matches /osk\.exe/is and not 1 of ($s*) and not ( $upd_magic at 0 )
}
rule magnify_ANOMALY {
meta:
author = "Florian Roth"
description = "Abnormal magnify.exe (Magnifier) - typical strings not found in file"
date = "01/06/2014"
score = 55
strings:
$upd_magic = { 44 43 }
$win7 = "Microsoft Screen Magnifier" wide fullword
$win2000 = "Microsoft Magnifier" wide fullword
$winxp = "Software\\Microsoft\\Magnify" wide
condition:
filename matches /magnify\.exe/is and not 1 of ($win*) and not ( $upd_magic at 0 )
}
rule narrator_ANOMALY {
meta:
author = "Florian Roth"
description = "Abnormal narrator.exe - typical strings not found in file"
date = "01/06/2014"
score = 55
strings:
$upd_magic = { 44 43 }
$win7 = "Microsoft-Windows-Narrator" wide fullword
$win2000 = "&About Narrator..." wide fullword
$win2012 = "Screen Reader" wide fullword
$winxp = "Software\\Microsoft\\Narrator"
$winxp_en = "SOFTWARE\\Microsoft\\Speech\\Voices" wide
condition:
filename matches /narrator\.exe/is and not 1 of ($win*) and not ( $upd_magic at 0 )
}
rule notepad_ANOMALY {
meta:
author = "Florian Roth"
description = "Abnormal notepad.exe - typical strings not found in file"
date = "01/06/2014"
score = 55
strings:
$upd_magic = { 44 43 }
$win7 = "HELP_ENTRY_ID_NOTEPAD_HELP" wide fullword
$win2000 = "Do you want to create a new file?" wide fullword
$win2003 = "Do you want to save the changes?" wide
$winxp = "Software\\Microsoft\\Notepad" wide
condition:
filename matches /notepad\.exe/is and not 1 of ($win*) and not ( $upd_magic at 0 )
}
Although the string descriptors list only some of the windows versions we’ve tested it against the following versions:
Windows 2000
Windows 2003 Server
Windows 7 (x64)
Windows 2008 R2
Windows 2012
What you get as result is a small anomaly scanner made completely with Windows tools and Yara. An administrator would just have to click the Batch file and run the script with admin rights. The following screenshot shows a scan on the Windows folder with a prepared malicious “iexplore.exe” in the subfolder “C:\Windows\AA_Testing”.
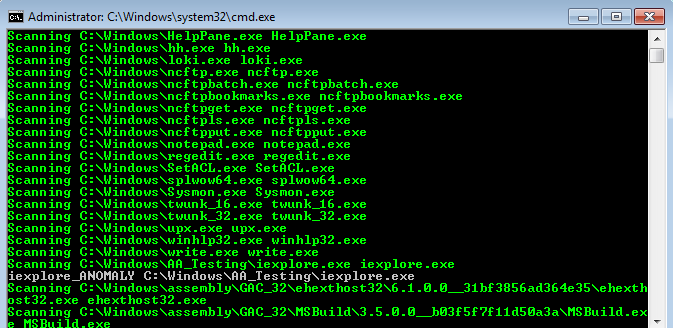
Yara Inverse Matching Anomaly Scanner in Action
You could remove the section “Write-Host -foregroundcolor “green” “Scanning”$_.FullName $_.Name;” to show only the alerts or modify the script that it writes a log file.
We use all of these rules in our APT Scanner THOR and added further rules matching 3rd party tools attackers tend to replace or rename.