The new version of “thor-util” (used with THOR/SPARK) / “spark-core-util” (used with SPARK Core) support a feature that allows a user to convert any scanner log file into a convenient report.
- Convert THOR / SPARK / SPARK Core scan logs into HTML reports
- Convert a single text log file into an HTML report
- Convert multiple log files (50 max.) in a directory into a single HTML report
- Provide a file with filters to suppress false positives in the reports
- Even LOKI logs can be converted (no support)
- Hash values linked to Virustotal searches
- IP values linked to VirusTotal searches
- Header sections linked to elements via ankers
You can access this feature in the upcoming enterprise products (THOR 8.47.2 and SPARK 1.13) and the free product SPARK Core (SPARK Core 1.13).

The following screenshot shows a typical text log file. It can be processed in log analysis solutions but it is difficult to read for an analyst. Most analysts search these log files for “(Alert|Warning):” or use grep to get the most relevant messages.
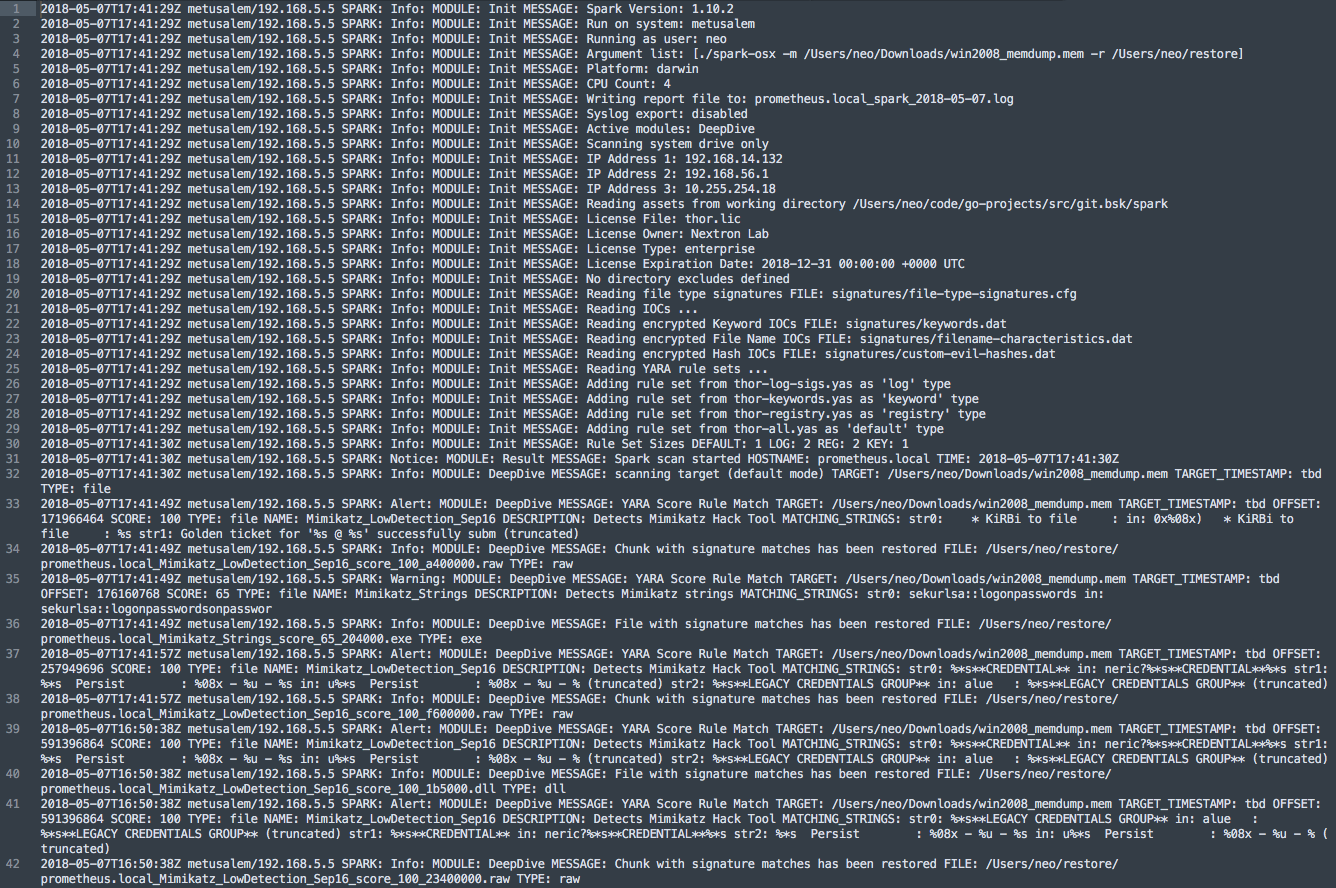
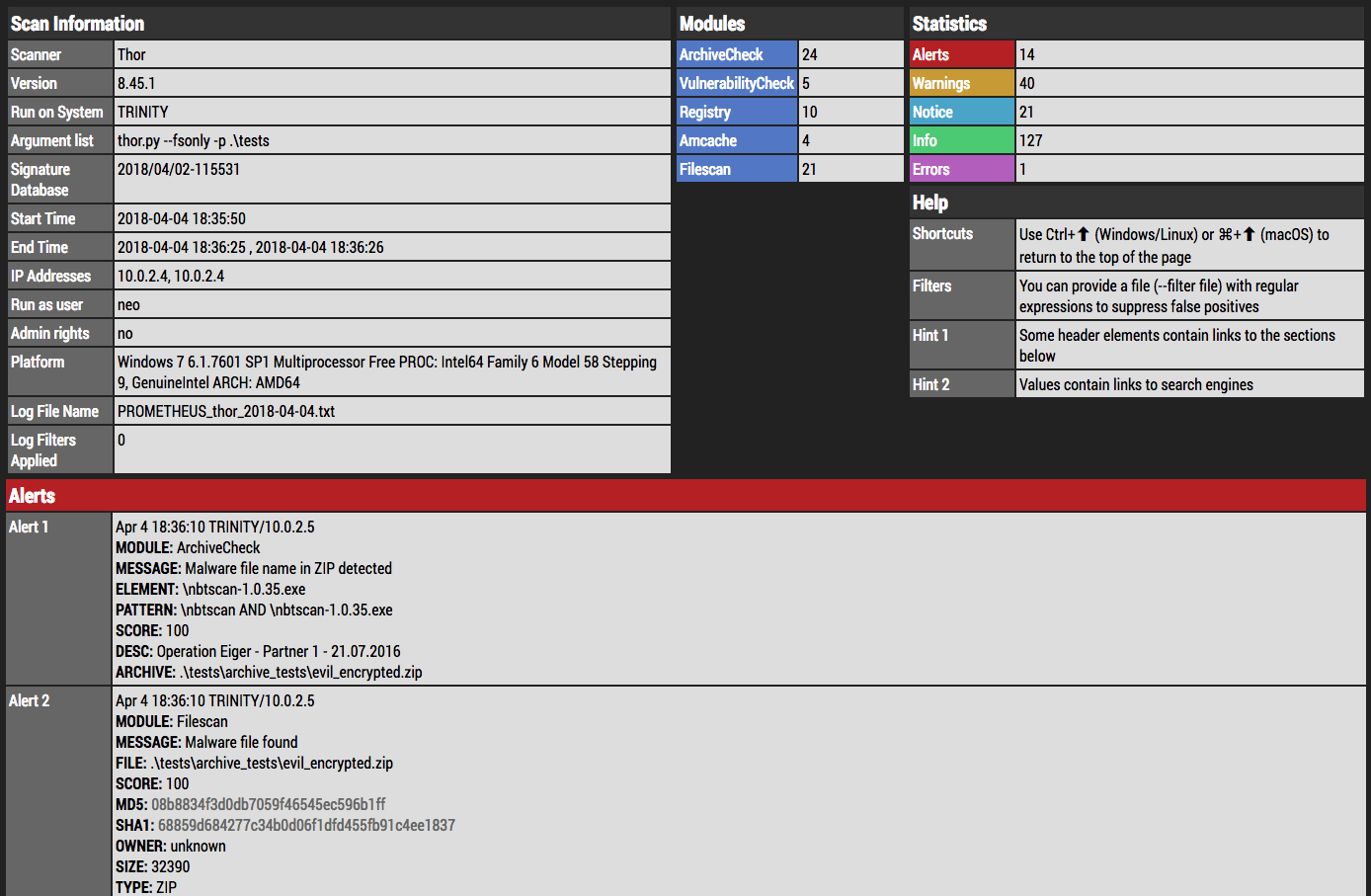
Generate an HTML report for a single log file
thor-util report --logfile PROMETHEUS_thor.log
thor-util report --logdir ./logs
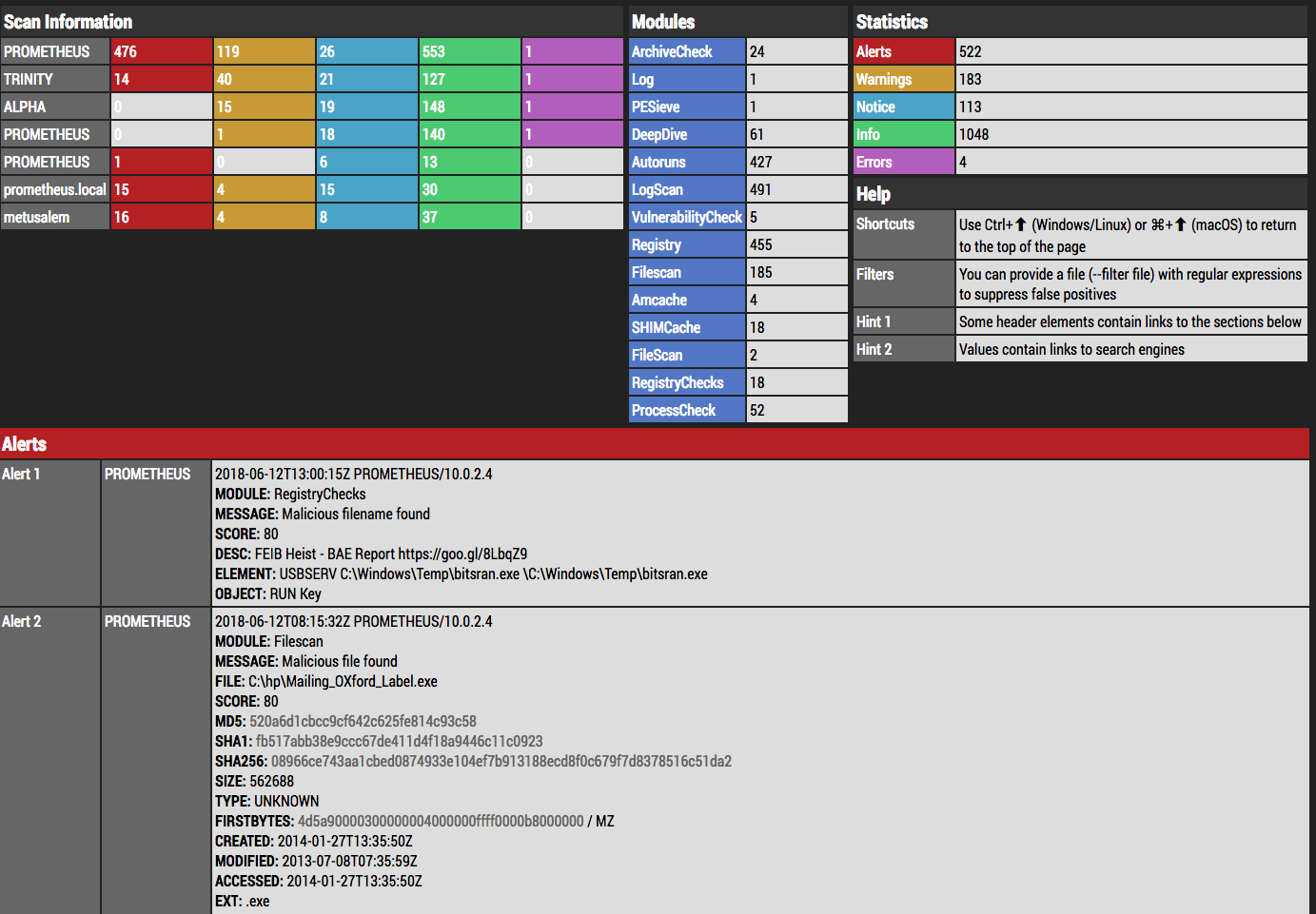
You can also provide a file with regular expressions that are applied during log parsing as filters to suppress false positives in the reports.
The new tools will be in all productive packages at the end of this week.