Working in incident response or malware analysis, you may have come across compromised and sometimes revoked certificates used to sign malware of different types. Often threat groups use stolen certificates to sign their malware.
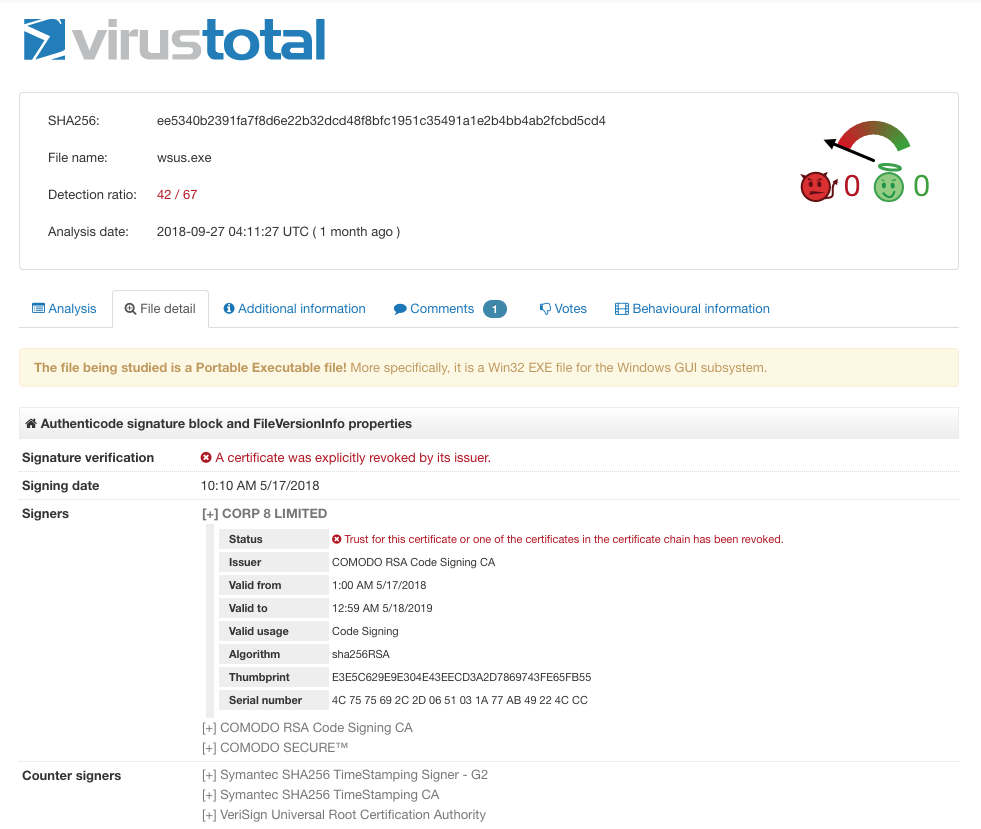
I’d like to show you an easy way to create a YARA rule for such a certificate. We will look at a sample that has been marked as malware by many Antivirus engines on Virustotal and the “Details” tab shows a revoked certificate. That’s a good indicator for a compromised certificate that has been and sometimes is still used by threat groups to sign their binaries.
Sample: ee5340b2391fa7f8d6e22b32dcd48f8bfc1951c35491a1e2b4bb4ab2fcbd5cd4
rule MAL_Compromised_Cert_Nov18_1 {
meta:
description = "Detects a compromised certificate of CORP 8 LIMITED - identified in November 2018"
date = "2018-11-01"
hash = "ee5340b2391fa7f8d6e22b32dcd48f8bfc1951c35491a1e2b4bb4ab2fcbd5cd4"
condition:
uint16(0) == 0x5a4d and
for any i in (0 .. pe.number_of_signatures) : (
pe.signatures[i].issuer contains "COMODO RSA Code Signing CA" and
pe.signatures[i].serial == "4c:75:75:69:2c:2d:06:51:03:1a:77:ab:49:22:4c:cc"
)
}
As you can see, you need to copy two strings from Virustotals web page:

Virustotal Intelligence users can use the following hunting rule to detect new uploaded malicious samples with revoked certificates:
rule Compromised_Certificate {
condition:
// New files, detected by more than 30 engines and revoked certificate
new_file and positives > 30 and tags contains "revoked-cert"
}