THOR v10.1 features a mode of operation that is especially helpful in incident response or compromise assessment scenarios – remote scanning.
Imagine that you’re in a firefighting scenario – a breach has been confirmed and management wants to have quick results on the extent of the compromise.
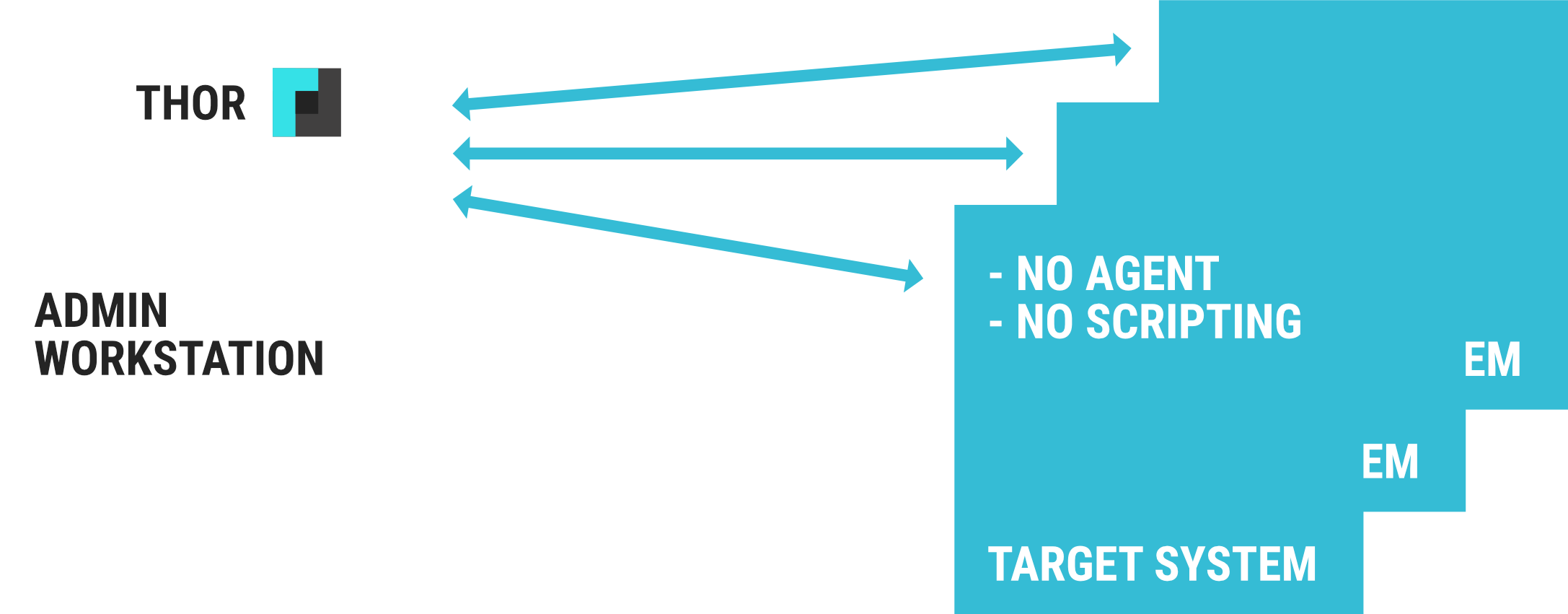
The new remote scanning feature called “THOR Remote” allows you to perform triage scans on hundreds of remote systems from a single admin workstation. You can think of it as an integrated PsExec.
No scripting, no agents, no hustle.
Benefits
- No agent
- No scripting
- Painless scans of many remote systems
Requirements
- Available on Windows only
- Accessible remote ports (135/tcp, 445/tcp)
- Account with local admin rights
All you need is the new version 10.1 of THOR and a command line of an admin user with the required privileges and open Windows ports (135/tcp, 445/tcp) on the remote systems.
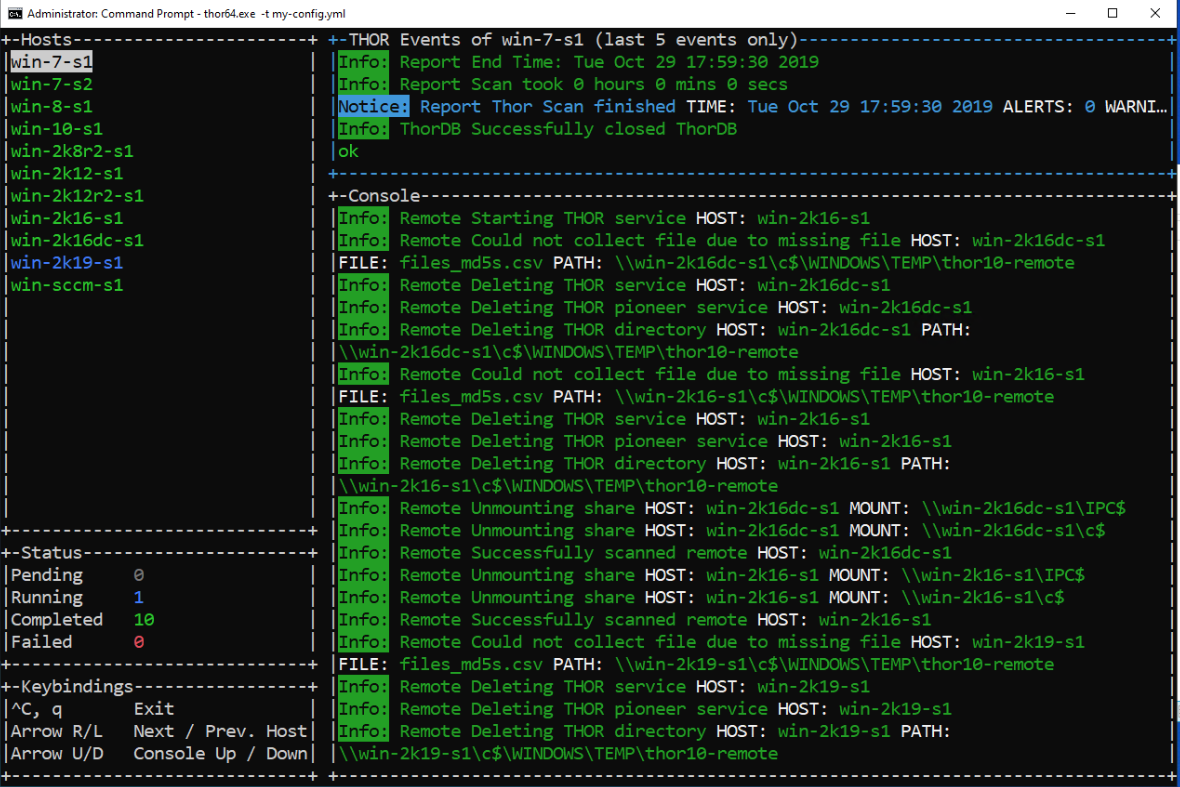
THOR will then switch into a new mode of operation and present a command line interface showing scan information and a scrollable pane for each log file. (see screenshot)
THOR writes the log files to a local folder on the admin workstation or sends them via SYSLOG to your SIEM system.
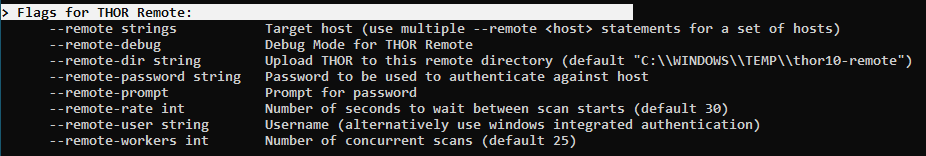
You can also define a number of concurrent scans (workers) and delay the scan starts to distribute the load evenly among the target systems. This is beneficial when you scan numerous virtual machines running on a few host systems.
A complete triage scan of your internal domain can’t be more comfortable.