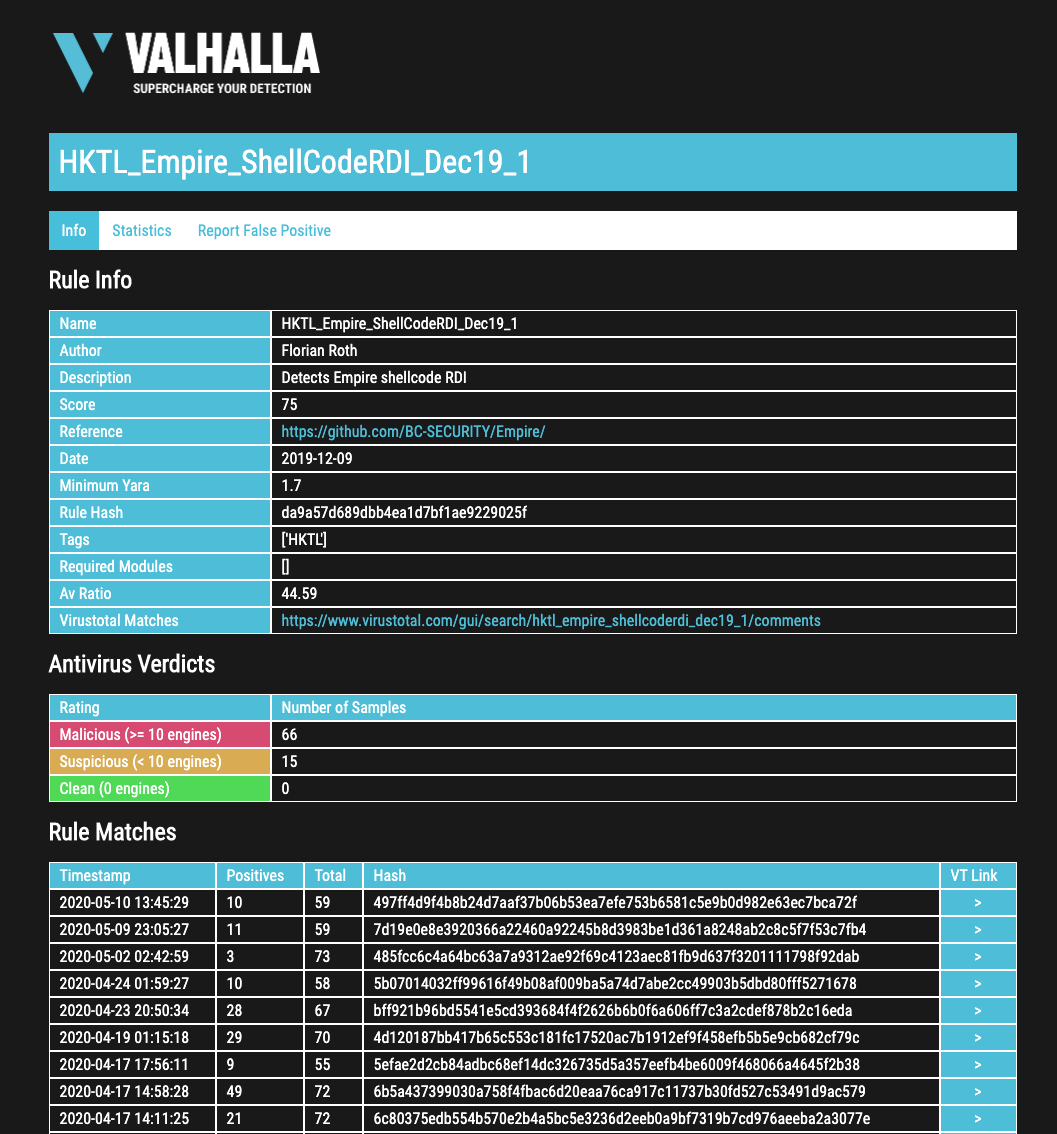
Rule Info Pages
The new rule info pages allow you to get more information on a certain rule. You can find all the meta data, as well as past rule matches and previous antivirus verdicts.
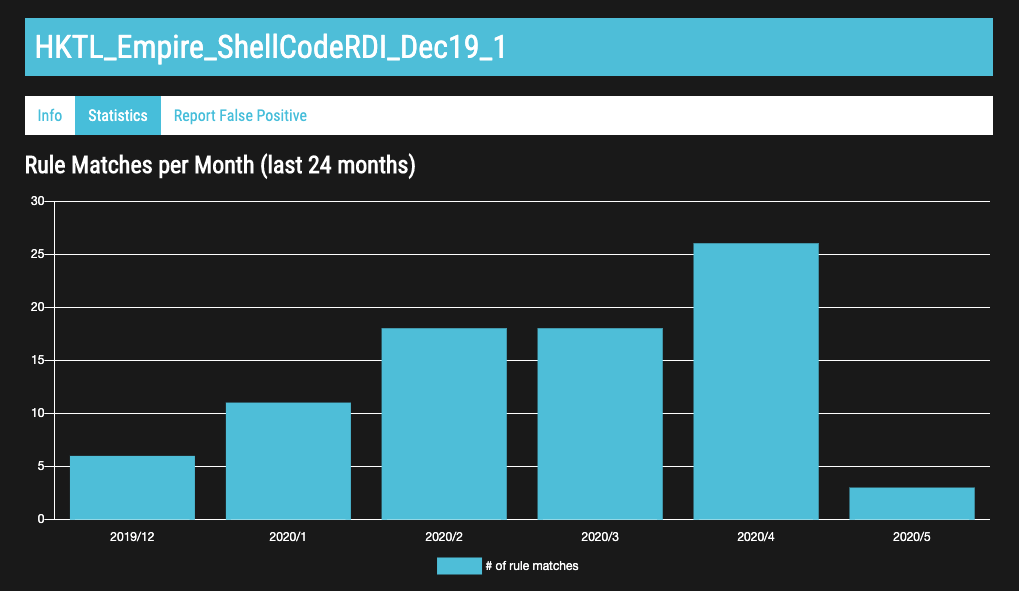
A second tab contains statistics.
You can also report false positives that you’ve encountered with that rule using the button in the tab bar.
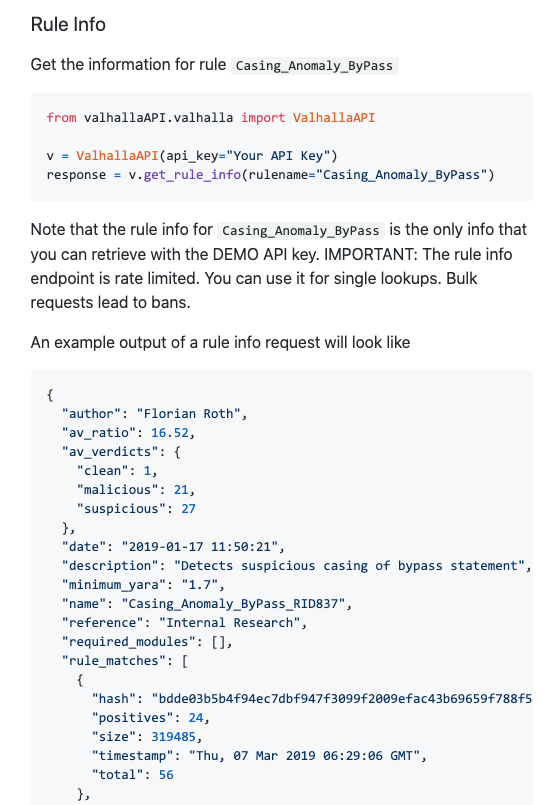
Note that the rule info lookups in the web GUI are rate limited. If you query rule infos too often, you get blocked.
The rule info pages can be access using this URL scheme:
https://valhalla.nextron-systems.com/info/rule/RULE_NAME
For example:
https://valhalla.nextron-systems.com/info/rule/HKTL_Empire_ShellCodeRDI_Dec19_1
Automated Tagging
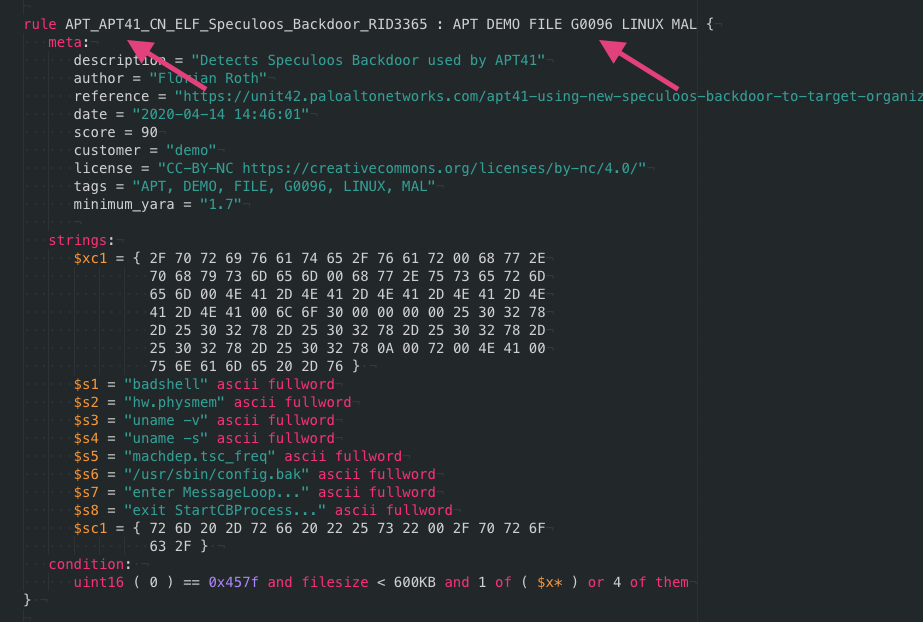
The automated tagging has been extended to included MITRE ATT&CK threat actor group IDs.
Status Includes Version
The status endpoint now includes a version number.
The version number is an integer value generated from the last update timestamp using a format string “%Y%m%d%H”. This way it is not just a version number that you can compare with you local last change (e.g. “>=”) but also an implicit timestamp.
You can access that endpoint via POST request (/api/v1/status) or Python API’s “get_status()” function.

You can find more information on Valhalla on our web page.