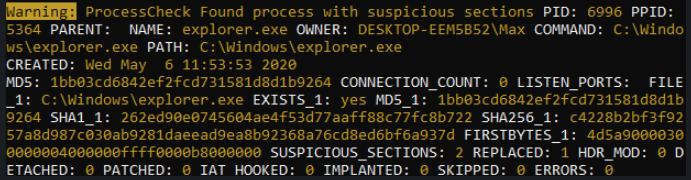
PE Sieve Integration
With the integration of @hasharezade‘s PE Sieve project THOR is able to detect and report a variety of process implants like replaced or injected portable executables (process hollowing), injected shellcodes, hooks and in-memory patches.
Naturally, since @hasharezade’s project is an open source project, this feature will also be available in THOR Lite, the free version of THOR.

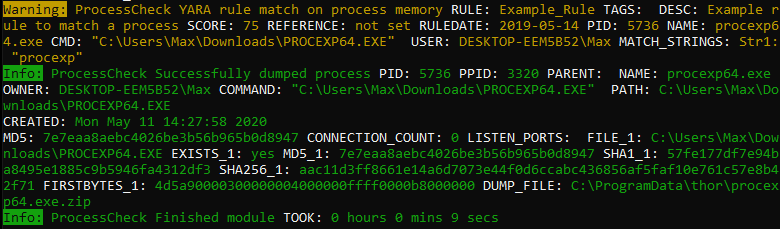
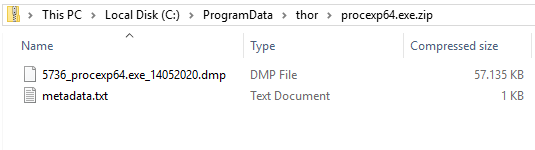
Process Dumps
THOR v10.5 creates a process dump of any process that is considered suspicious or malicious.
This process dump can then be analyzed with standard tools later to examine the findings. Use the flag “–dump-procs” to activate this feature.
To prevent excessive disk space usage, new dumps overwrite old dumps of the same process. Also, THOR stores the dumps in a compressed form and will not generate dumps if less than 5 GB disk space is available.
Global Module Lookback
The current “–lookback” option allows you to restrict the Eventlog and log file scan to a given amount of days. E.g. by using “–lookback 3” you instruct THOR to check only the log entries that have been created in the last 3 days.
We’ve extended this feature to include all applicable modules, including “FileScan”, “Registry”, “Services”, “Registry Hives” and “EVTX Scan”. By setting the flags “–global-lookback –lookback 2” you instruct THOR to scan only elements that have been created or modified during the last 2 days. This reduces the scan duration significantly.
On our test systems, we were able to reduce the scan duration of a full filesystem scan and a lookback of three days to less than 4 minutes.

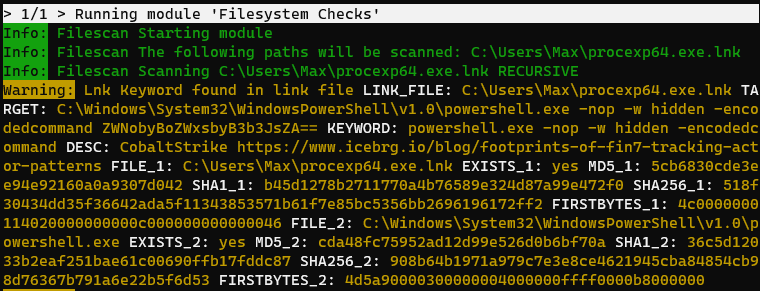
LNK File Parser
The link file parser module processes .lnk files, extracts relevant data and gathers more information on the linked contents. It also applies the anomaly detection methods to its contents to allow the detection of unknown threats.
More Changes
- Default output files include a timestamp and not just the date
- Outputs include non-ASCII characters in a hex encoded form (use –ascii to revert to ASCII only output)
- THOR DBs “–resume” feature is deactivated by default and has to be manually activated using “–resume” due to significant performance implications caused by updating resume states in THOR DB
- New –portal* flags allow the licenses generation at runtime using our Netxron portal API
- New –yara-max-strings-per-rule flag limits the output of matching strings
- New –nofserrors flag suppresses all error messages regarding access permissions
- New –scanid-prefix allows users to set a custom prefix to allow the identification of group of scans
- New –print-signatures flag lists names and meta data of all included YARA and Sigma rules