Exploitation
All four vulnerabilities and related exploitation techniques have been unknown to the public and were used by the attackers at least since the beginning of January this year. We wrote YARA signatures to detect the exploitation attempts in Exchange web service logs and published Sigma rule that looks for more indicators in Exchange server logs.
The new rules will be available on 4th of March.
We recommend scanning with the “–sigma” command line flag to apply Sigma rules during Logscan and Eventlog scanning.
Web Shells
The mentioned web shells are already covered by existing rules.
Look for the following keywords in THOR log data
- Webshell_ASP_cmd_3
- Webshell_lowcov_Nov17_2
- WEBSHELL_SharPyShell_ASPX
- Chopper
- reGeorg
- Webshell + Tiny
The web shells samples mentioned by Microsoft as a hash cannot be found in public databases (e.g. Virustotal). We can only guess the current coverage and add a new rule to the rule set of tomorrow:
WEBSHELL_TINY_ASP_Chopper_Mar21_1
Detection rate of some of the web shells on Virustotal:
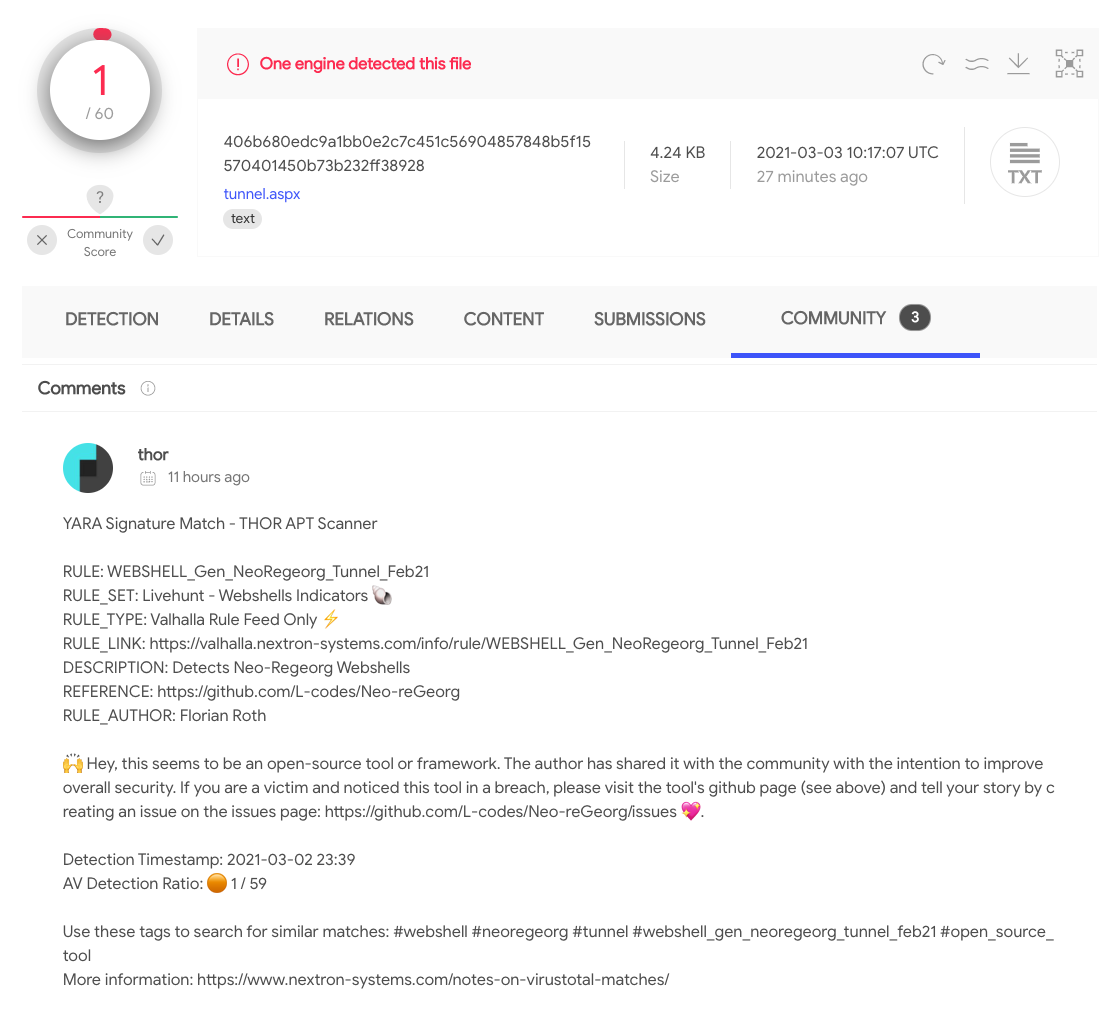
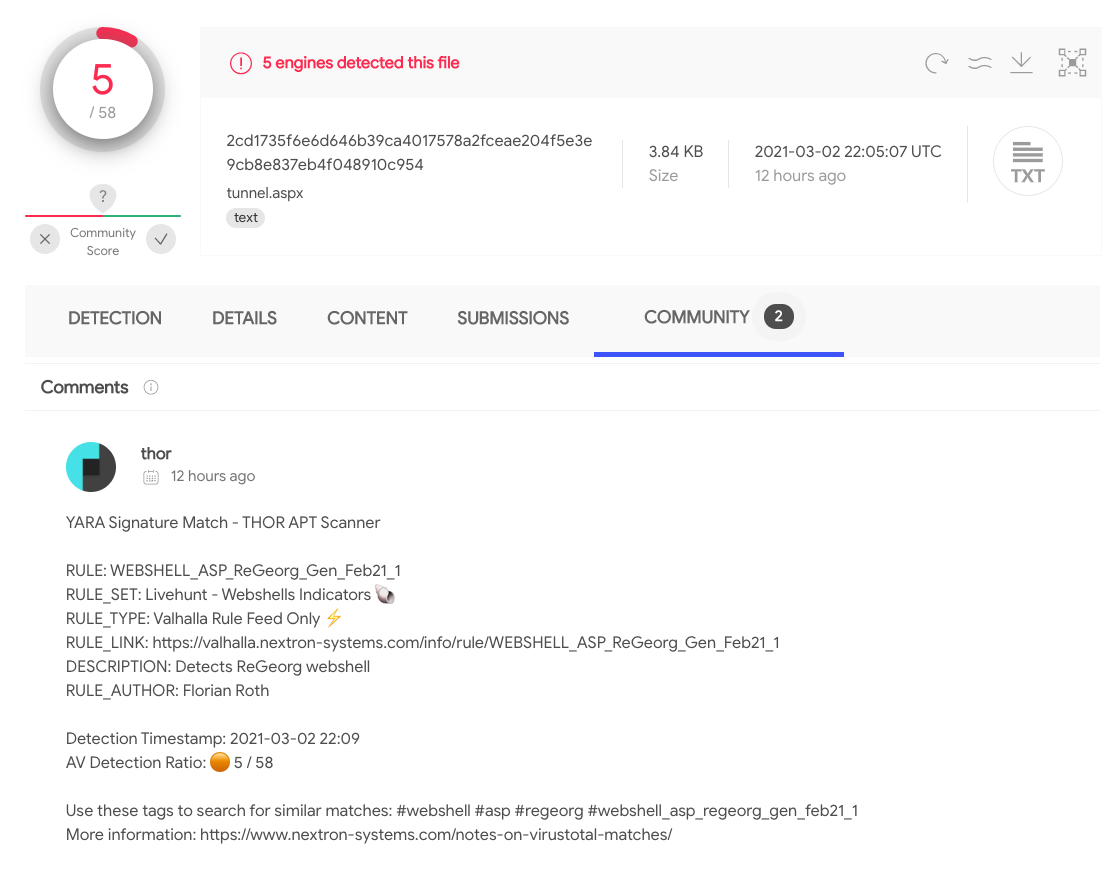
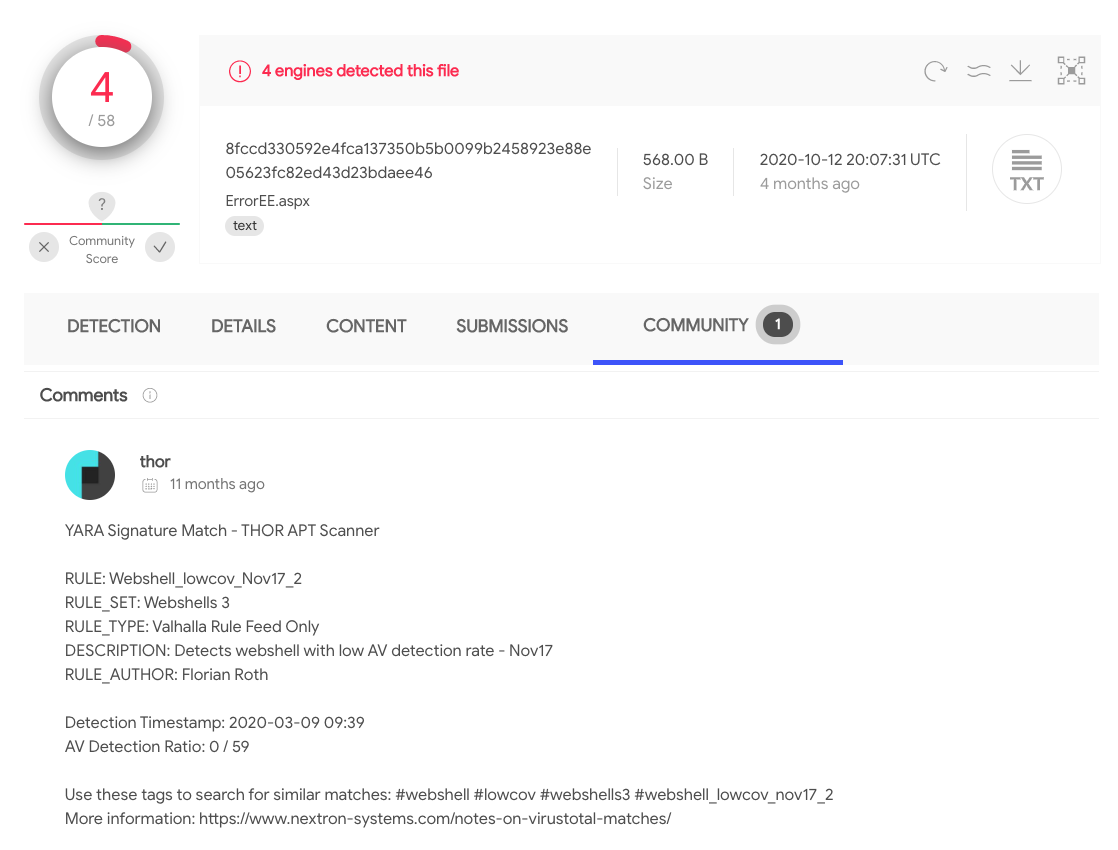
LSASS Process Memory Dumping
Looks for the following keywords in your THOR Logs:
- SUSP_LSASS_Dump
- HKTL_PUA_Procdump
- HKTL_MiniDump_WriteDump
- HKTL_AQUARMOURY_Brownie_Jan21_1
- ‘Suspicious Use of Procdump’ (Sigma)
- ‘Process Dump via Rundll32 and Comsvcs.dll’ (Sigma)
- ‘LSASS process memory dump’ (Filename IOC)
PowerShell Tools
Look for the following keywords:
-
p0wnedPowerCat
-
Nishang
- ‘Malicious Nishang PowerShell Commandlets’ (Sigma)
We wrote a new rule for PowerCat and Nishangs PowerShell tool to achieve a better coverage:
-
HKTL_PS1_PowerCat_Mar21
-
HKTL_Nishang_PS1_Invoke_PowerShellTcpOneLine
Both new rules will be available on 4th of March.