Last week, we’ve released a blog post on how to detect HAFNIUM activity with the use of THOR Lite. Since our first set of rules, we’ve added several important new rules from fellow researchers and moved even more rules from our commercial set into the open source rule set.
This alone would be reason enough to recommend another scan. But during the last three days, we’ve added a special group of rules (see below) and fixed some bugs in the code base of THOR that could have lead to false negative on some of the relevant log files (exclusion under certain conditions).
We therefore recommend a signature update, an upgrade to THOR v10.5.12 (THOR TechPreview v10.6.4) and a new scan run to uncover traces of hacking activity using the newest detection rules.
The following sections explain the extended coverage.
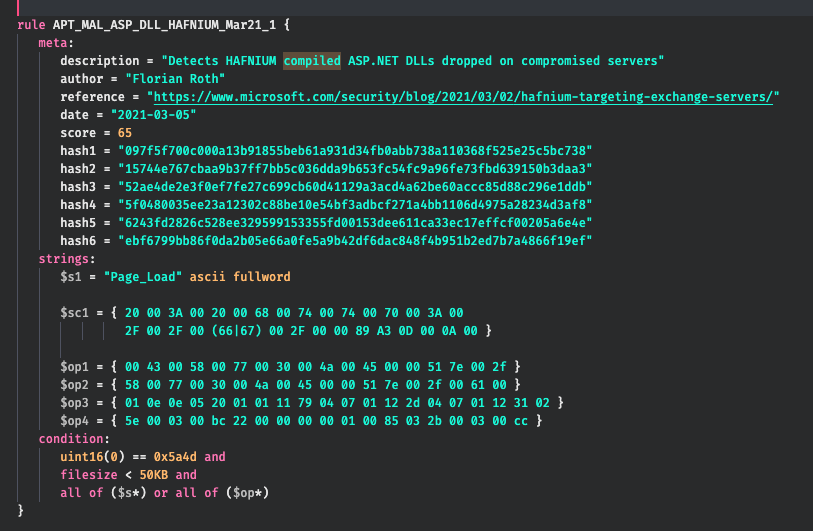
Compiled ASPX Files
We’ve added rules for the compiled ASPX files that often remain on a system even in cases in which an attacker has removed the original web shell.
These are perfect rules to uncover actual post-exploitation attacker activity and not “just an exploitation” and a webshell drop.
You can find more information on the creation and meaning of these forensic artefacts in this Trustwave blog post.
(Source: Trustwave)

Improved Generic Webshell Coverage
Arnim Rupp provided many improvements to its public rule set that detect all kinds of webshells based on generic characteristcs.
Frequent updates improved these rules and extended the coverage to include the newest unknown webshells mentioned in the most recent reports.
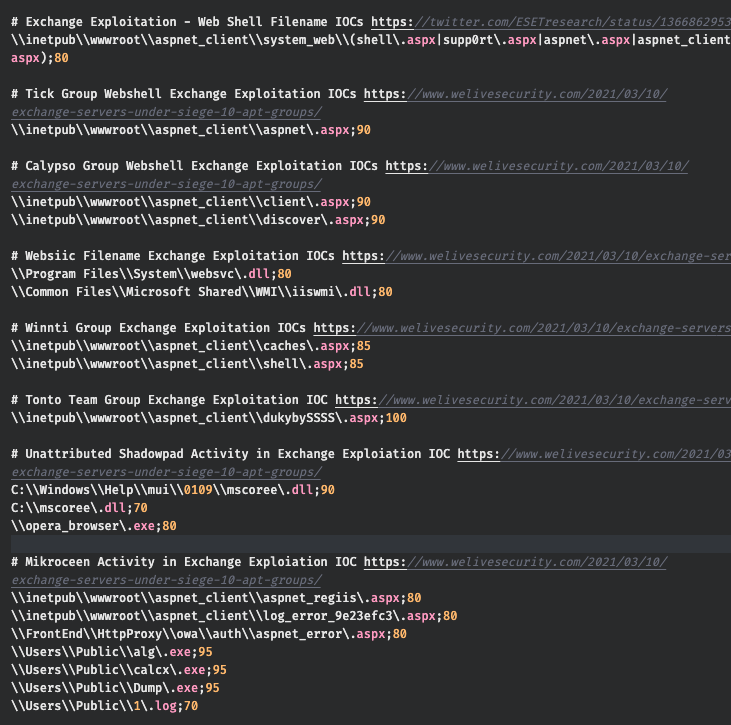
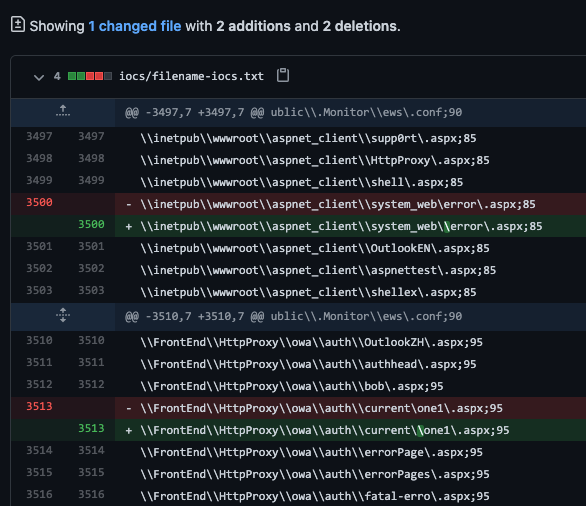
More Filename IOCs
Over the last few days we’ve added many new filename IOCs mentioned in reports by ESET and others.
The ESET report mentions and lists IOCs of 10 different APT groups exploiting the Exchange vulnerbility and leaving traces on compromised systems.

Rule Improvements
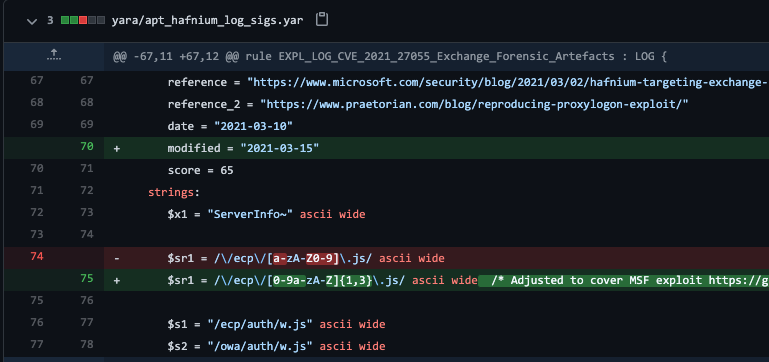
We’ve improved several rules to extend their coverage.
E.g. the rule that looked for POST requests to a single letter JavaScript file now looks for a certain pattern that includes exploitation attempts with the new Metasploit module.
THOR
thor-util.exe upgrade
THOR Lite
thor-lite-util.exe upgrade
Remember these recommendations from the initial blog post:
- If you’ve installed Exchange on a drive other than C: use `–allhds`
- Use `–sigma` feature when scanning with THOR (not available in THOR Lite)
- Add the following exclusion to the file `./config/directory-excludes.cfg` to skip all mailbox directories:
\\(MDBDATA|Mailbox|Mailbox Database)\\