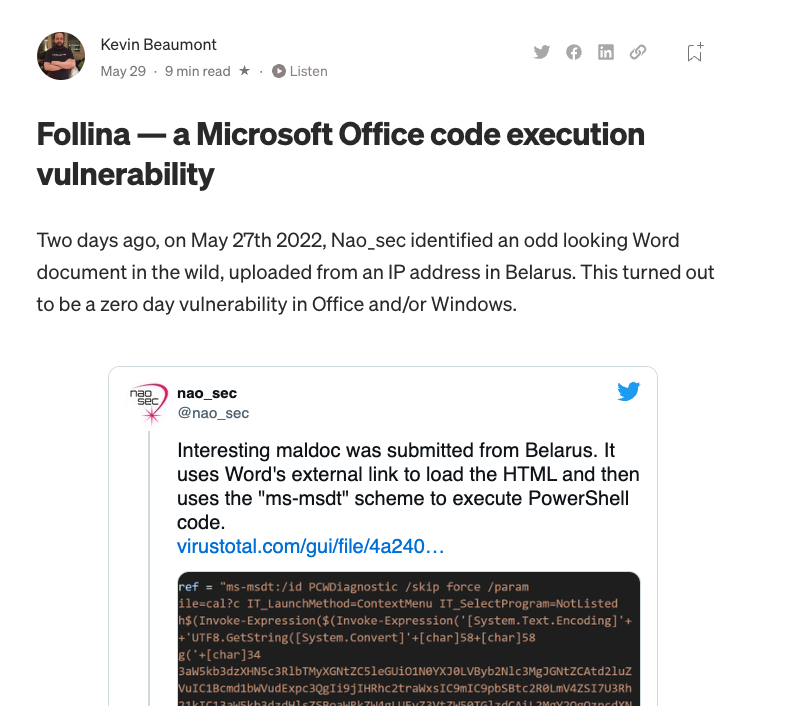
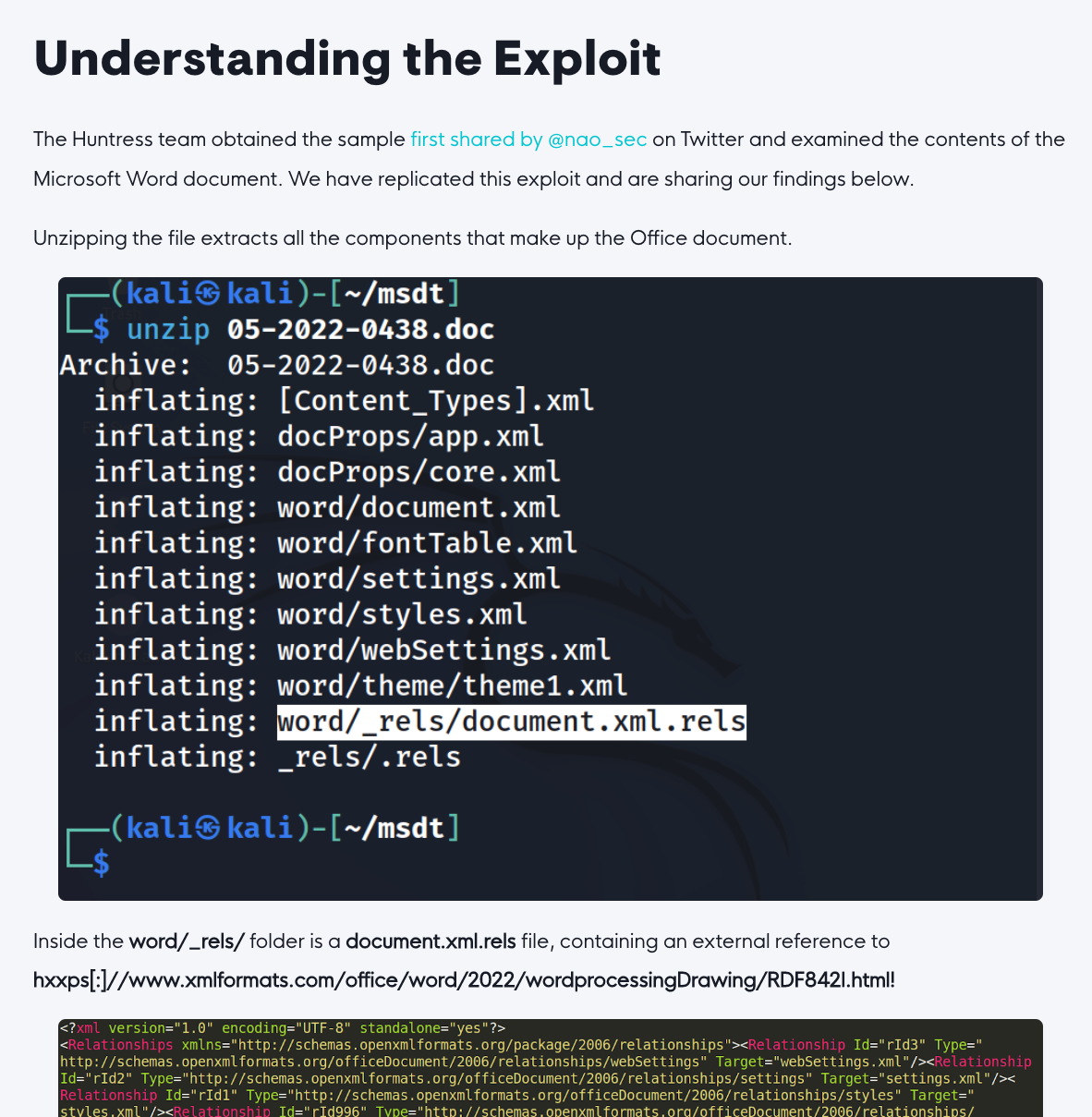
The Follina 0day vulnerability (CVE-2022-30190) in Microsoft Windows is actively exploited in-the-wild and highly critical. This blog posts lists some important web resources and the signatures that detect exploitation attempts.
Kevin Beaumont's Blog Post
Kevin’s post contains links to tweets of researchers that discovered the 0day exploit, information on the timeline, and mitigations
Huntress Labs Blog Post
Explains the exploit in more detail
Counter Measures
Recommended counter measures by Benjamin Deplhy
Signatures Detecting Follina / CVE-2022-30190 Attacks
Check for matches with the following rules:
YARA
Rules shared in the public signature-base and used in THOR and THOR Lite
- SUSP_Doc_RTF_OLE2Link_Jun22
- SUSP_Doc_RTF_OLE2Link_EMAIL_Jun22
- SUSP_DOC_RTF_ExternalResource_EMAIL_Jun22
- SUSP_Msdt_Artefact_Jun22_2
- SUSP_LNK_Follina_Jun22
- SUSP_PS1_Msdt_Execution_May22
- SUSP_Doc_WordXMLRels_May22
- SUSP_Doc_RTF_ExternalResource_May22
- EXPL_Follina_CVE_2022_30190_Msdt_MSProtocolURI_May22 (previously: MAL_Msdt_MSProtocolURI_May22)
Only available in THOR
- SUSP_PS1_Obfusc_Combo_Base64_CharacterConcatenation_May22
- SUSP_PS1_Nested_InvokeExpression_May22
- SUSP_Office_Cloaked_MHT_Moniker_Jun22 (uses external vars; not in Valhalla)
- EXPL_MAL_MalDoc_TemplateInjection_Jun22
- SUSP_Encoded_Follina_CVE_2022_30190_Payloads_Jun22
- SUSP_EXPL_Follina_CVE_2022_30190_Jun22_1
- SUSP_EXPL_Follina_CVE_2022_30190_Jun22_2
- EXPL_Encoded_CVE_2022_30190_Payloads_Jun22_1
Sigma
Public Sigma rules used in Aurora, THOR and Aurora Lite
- Sdiagnhost Calling Suspicious Child Process – f3d39c45-de1a-4486-a687-ab126124f744
- New Lolbin Process by Office Applications – 23daeb52-e6eb-493c-8607-c4f0246cb7d8
- MSDT Executed with Suspicious Parent – 7a74da6b-ea76-47db-92cc-874ad90df734
- Execute Arbitrary Commands Using MSDT.EXE – 258fc8ce-8352-443a-9120-8a11e4857fa5
- Microsoft Outlook Product Spawning Windows Shell – 208748f7-881d-47ac-a29c-07ea84bf691d
Private Sigma rules only available in Aurora
- Sdiagnhost Loading System.Management.Automation.dll – 1a4a0e9c-e47d-492c-800f-545f83fac88a
- Sdiagnhost Calling Suspicious Descendant Process – 8655fa4b-e956-4ed4-b20d-151dfd8c802d