In this blog article, we will talk about how you can use THOR to scan Docker images. Consider the following use case: Before using an upstream Docker image, you want to precheck it for known IOCs and backdoors. THOR can help you with this!
Prerequisites
- Docker image with a shell installed (e.g. sh, bash, etc.)
- In this example we will use Alpine Linux
- THOR 🙂
- In this example we will use Thor-Lite. However, for a real-world usecase you should consider using the full Thor version (Thor vs Thor-lite).
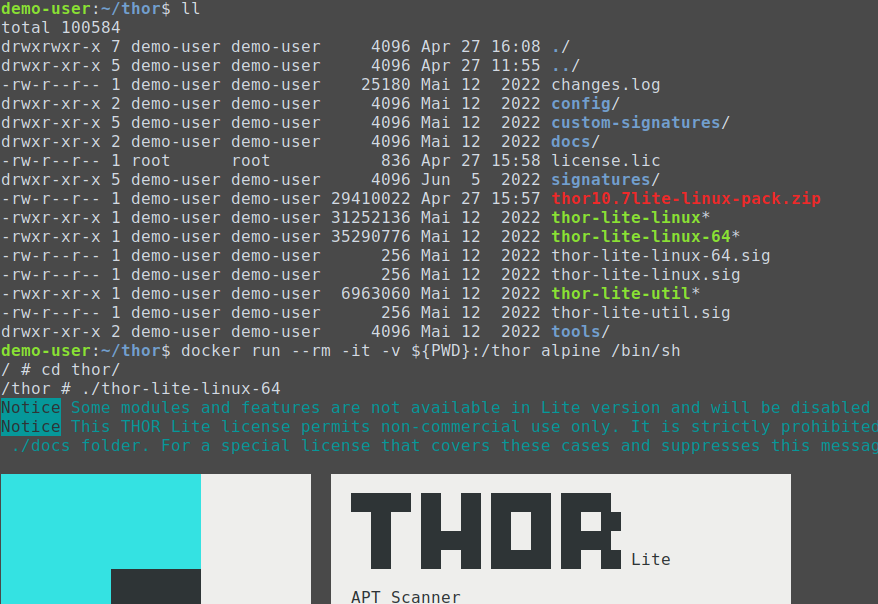
Running THOR in a Docker container
In your THOR folder run: docker run --rm -it -v ${PWD}:/thor alpine /bin/sh. This will create a Docker container based on Alpine Linux, mount your working directory (where THOR is stored) to /thor in the container, and will drop you into the sh shell. Inside the Docker container you can cd /thor and start THOR: ./thor-lite-linux. You can exchange alpine with any Docker image, as long as it includes a shell.
{docker-id}_files_md5s.csv{docker-id}_thor_{date}.html{docker-id}_thor_{date}.txt
These files contain all findings of the THOR scan.
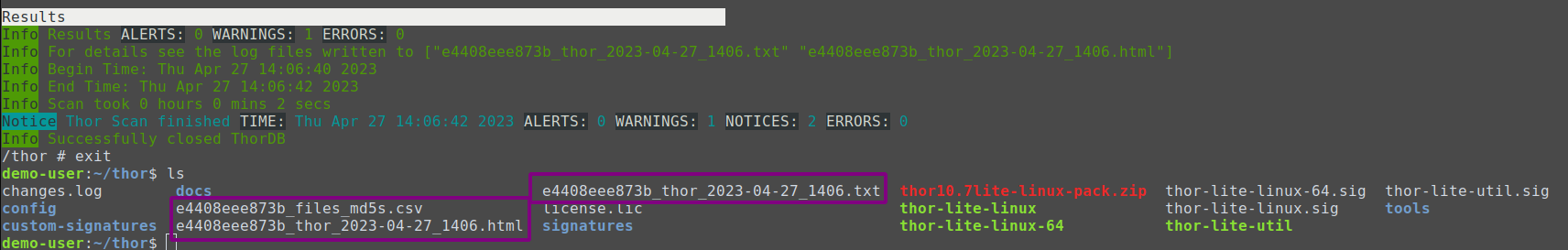
By using THOR to scan Docker images, you do not have to blindly trust the author of an upstream Docker image – you can see for yourself!
In part 2 of this series we explain how to scan Docker containers using THOR.