We are pleased to announce the launch of the Nextron Community Discord Server, a dedicated space for technical dialogue and support for Nextron's range of products. This server aims to facilitate a deeper understanding and more effective use of our solutions.Key...
Supercharging Postfix With THOR Thunderstorm
Have you already heard about THOR Thunderstorm, a self-hosted THOR as a service? In this blog post, we will show how you can leverage THOR Thunderstorm to level up your email infrastructure security.THOR Thunderstorm is a web API wrapped around THOR, which accepts...
Integration of THOR in Velociraptor: Supercharging Digital Forensics and Incident Response
Digital forensics and incident response (DFIR) are critical components in the cybersecurity landscape. Evolving threats and complex cyber-attacks make it vital for organizations to have efficient and powerful tools available. If you are not already enjoying the...
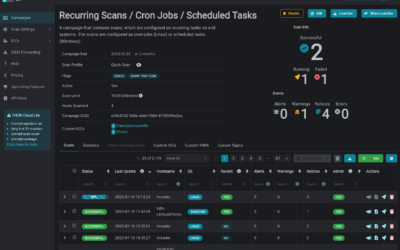
Introducing THOR-Cloud Lite: Seamless On-Demand Forensic Scanning Made Easy
We just launched THOR-Cloud Lite our new free, lightweight and easy to deploy on-demand compromise assessment scanner. Allowing you to access your scans and reports from everywhere at any time. Licensing, scan campaigns and reports everything is conveniently managed...
Mjolnir Security: Incident Response Training – Dive Deep into Cybersecurity
We're thrilled to announce an exciting collaboration with our esteemed partner, Mjolnir Security. Immerse yourself in their renowned “Blue Team Incident Response Training” taking place from the 23rd to the 26th of October. This four-day intensive program promises a...
Detecting JanelaRAT with Yara and THOR
In the last weeks, we observed an increase in .NET based malware using DLL sideloading. A prominent example is JanelaRAT, a recent campaign targeting Latin American FinTech users. Their initial attack involves a phishing email, mainly in Portuguese language. The user...
How to scan Ivanti Endpoint Manager Mobile (EPMM) / MobileIron Core for CVE-2023-35078 Exploitation
In this blog post, we address a critical security concern and explore methods for evaluating potential compromises on devices like Ivanti Endpoint Manager Mobile (EPMM) / MobileIron Core using THOR or the free THOR Lite YARA and IOC scanners. Recently, a severe remote...
How to Perform Compromise Assessments on NetScaler / Citrix ADC Appliances Using THOR
In today's interconnected world, cyber adversaries are increasingly targeting and exploiting Internet-facing appliances and devices with unconventional or restricted operating systems. A pressing concern for users is whether it's possible to perform a compromise...
Hunting Ducks – A Threat Hunters Take on Ducktail Stealer
This post will look into DuckTail Stealer and their current .NET-based payloads. The stealer is well known for targeting marketing companies. Ducktails attacks usually come via email, posing as marketing campaigns or hiring offers. They use legitimate cloud hosts like...
New THOR 10.7.8 TechPreview Features
We are thrilled to unveil THOR 10.7.8, the latest version of our advanced persistent threat (APT) scanner, which brings a host of powerful features to enhance threat detection and analysis. In this blog post, we will highlight some of the notable additions that make...
Scanning for Indications of MOVEit Transfer Exploitation with THOR Lite
On June 1st, the vendor of MOVEit Transfer, previously known as Ipswitch but now called Progress, announced the discovery of a critical security vulnerability that has been exploited. MOVEit is an enterprise software utilized by numerous organizations globally for...
How to scan Docker containers using THOR – Part 2
The first part of this blog series covers how THOR can be used to scan a Docker image. In the second part of this series, we will talk about how you can use THOR to scan running Docker containers. Now, consider this new use case: You want to check if your running...