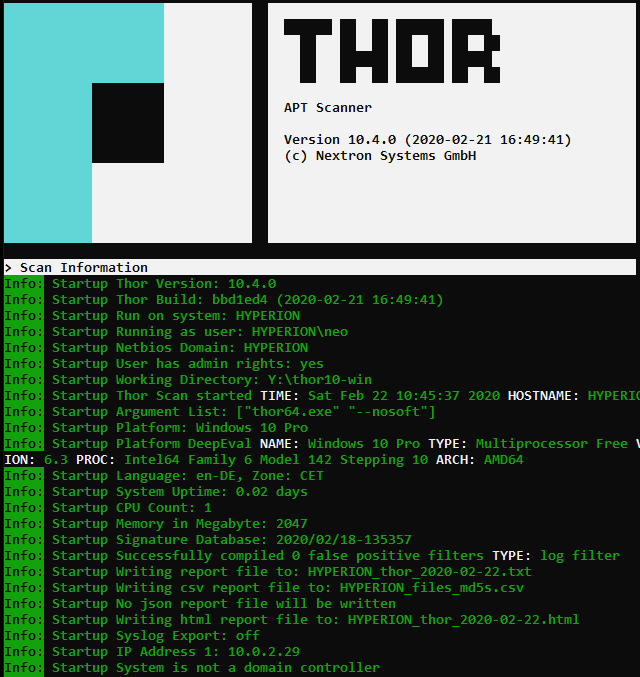
Incident response engagements often begin with a group of compromised systems and an even bigger group of systems that are possibly affected. The manual analysis of many forensic images can be challenging.
THOR speeds up your forensic analysis with more than 30,000 handcrafted YARA signatures, 2,000 Sigma rules, numerous anomaly detection rules and thousands of IOCs.
THOR is the perfect tool to highlight suspicious elements, reduce the workload and speed up forensic analysis in moments in which getting quick results is crucial.

Focus is Hacking Activity
THOR focuses on everything the Antivirus misses. With its huge signature set of thousands of YARA and Sigma rules, IOCs, rootkit and anomaly checks, THOR covers all kinds of threats. THOR does not only detect the backdoors and tools attackers use but also outputs, temporary files, system configuration changes and other traces of malicious activity.

Impressive Detection Rate
THOR’s impressive detection rate is well-known in the industry and fits the needs of threat hunters around the globe.
Thousands of generic signatures detect anomalies, obfuscation techniques and suspicious properties to rapidly accelerate compromise assessments.

Multiple Output Options
THOR supports various ways to report findings. It writes a text log or sends SYSLOG messages to a remote system (TCP, UDP, CEF, JSON, optional TLS). An HTML report is generated at the end of the scan. You can use the free Splunk App or ASGARD Analysis Cockpit to analyze THOR’s reports of thousands of systems.

Custom IOCs and YARA Rules
You can easily add your own indicators and signatures from threat feeds, your own investigations or threat reports.

System Stability has High Priority
THOR monitors the systems’ resources during the scan. If the available free main memory drops below a certain threshold, THOR stops the scan and exits with a warning. It automatically applies throttling if it detects low hardware resources and disables features that could affect the systems’ stability.
Detection Examples

Credential Dumper
Credential dumpers have long been considered as so-called dual-use tools. Only recently antivirus engines started to consequently report them but not all antivirus vendors followed that practice.
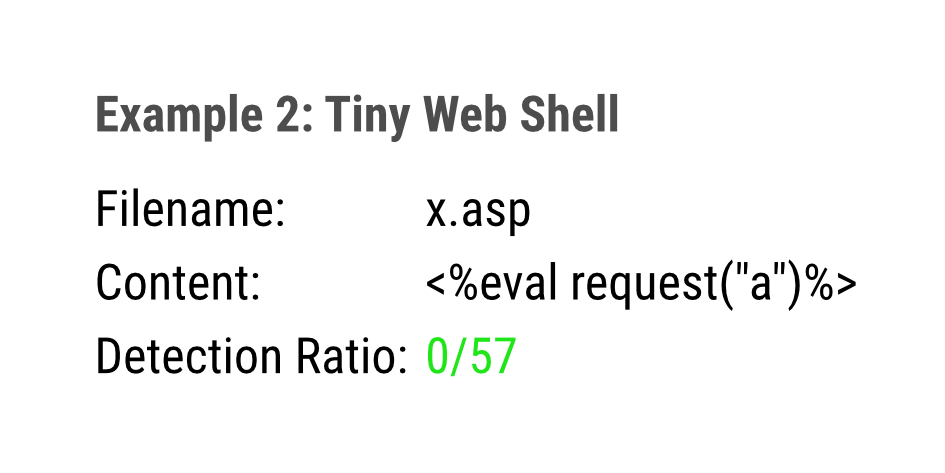
Tiny Web Shell
Many antivirus engines have problems detecting web shells. This may be due to the fact that their contents can be altered easily and in many ways. THOR has many web shell rules and threat hunting rules that detect special characteristics typically found in web shells.

Renamed PsExec
Administrators usually don’t rename well-known tools – whereas attackers do it frequently. THOR detects many renamed tools that can used for reconnaissance, lateral movement or data exfiltration.

Hacktool Output
Attackers don’t just drop tools on an end system. They also use them. The execution of these tools leaves traces in caches and on disk. THOR detects many output files generated by hack tools and indicates their use even if the executable has been removed by the adversary.
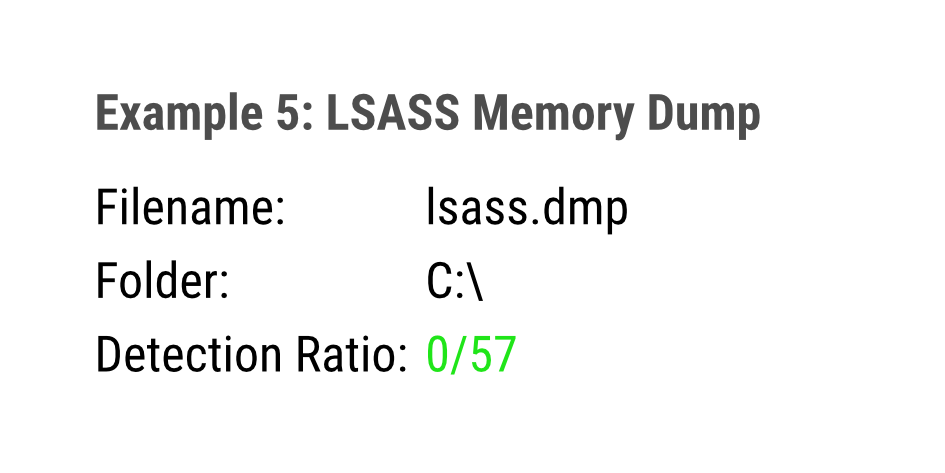
LSASS Memory Dump
While working on compromised systems, attackers leave traces of their work, even if no hack tool oder malware is involved. THOR detects temporary files like the process memory dump of the LSASS process, which contains credentials and can be used attackers to extract these credentials on a remote system.
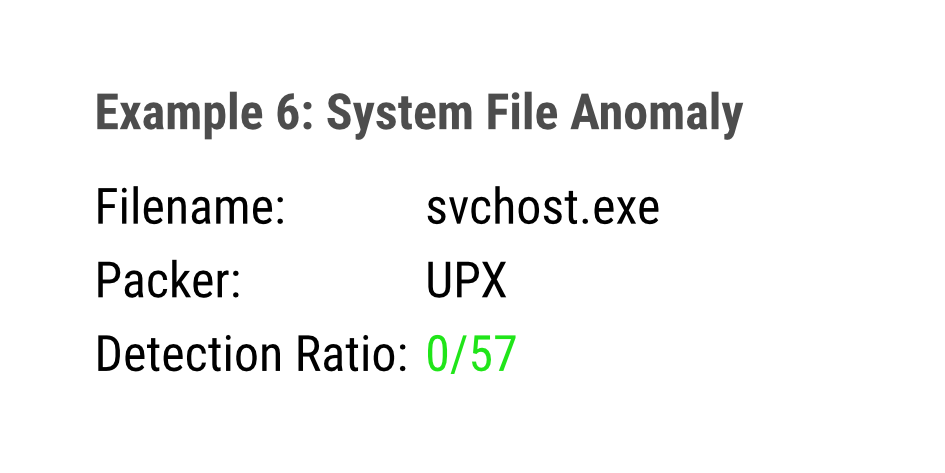
System File Anomaly
System files have specific characteristics. THOR features many detection rules that looks for suspicious combinations in these characteristics. Suspicious executable packers, PE copyright information, file sizes and PE signature issuers are just some examples of what THOR detects in system files.
Use Cases
THOR flexibility is outstanding. It can be used stand-alone for triage, live forensics or image scans in a lab environment.
THOR is the perfect tool to highlight suspicious elements, reduce the workload and speed up DFIR investigations in moments in which getting quick results is crucial.

Environment Triage Sweep
Complete Overview
- Scheduled run
- All systems
- Syslog to SIEM or Analysis Cockpit

Single System Live Forensics
Intense System Analysis
- Manual run
- Single suspicious system
- HTML report, text log

Image Scan in Lab
Lab Analysis
- Scan mounted system images
- No live data / filesystem only
- HTML report, text log
DropZone Mode
Lab Integration
- Scans samples dropped to a certain folder
- Syslog, text log
THOR’s Signature Set
THOR ships with more than 30,000 YARA signatures (VALHALLA’s big encrypted signature database and undisclosed IOC sets). These signatures includes web shell rules, anomaly rules, malware rules, hack tool and tool output rules, malicious script and macro rules, exploit code rules and rules for registry and log file matching.
Check VALHALLA’s statistics page to get some examples of THOR’s findings with low Antivirus detection rates.

Custom Indicators and YARA Rules
THOR uses YARA as its main signature format. The way how THOR integrates YARA is fully compatible with normal Yara signatures although THOR extends the standard matching in order to allow certain additional checks.
It is easy to extend the integrated database with your own rules and IOCs. You can add them to the signature database simply by placing these rules in the standard signature folder.
The documentation gives you guidance in cases in which you’d like to utilize the special extensions or encrypt your signatures before the deployment.
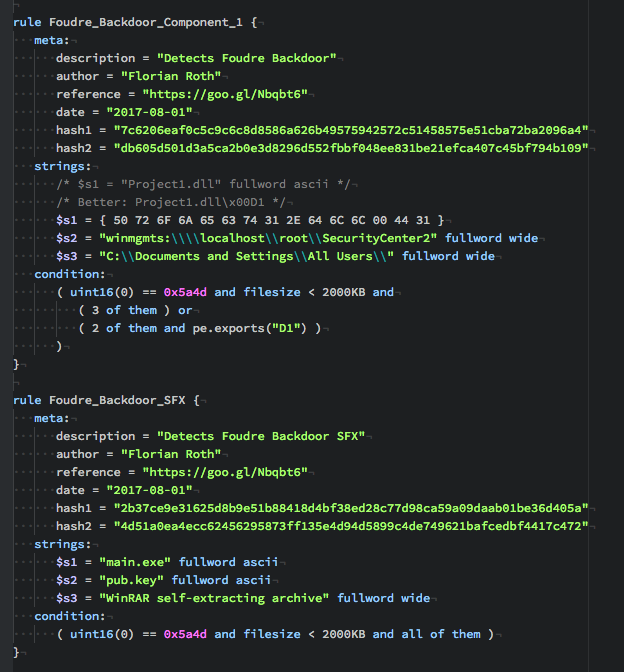
More Features
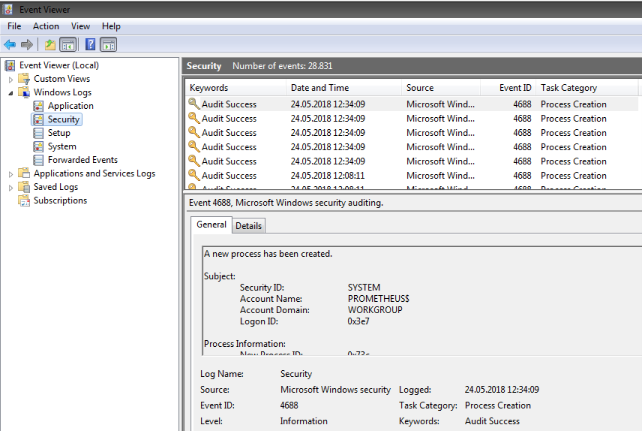
Sigma Scanning
The Eventlog analysis parses local Windows Eventlogs, checks for IOCs (e.g. filename IOCs) in the entries and applies Sigma rules to each log entry.
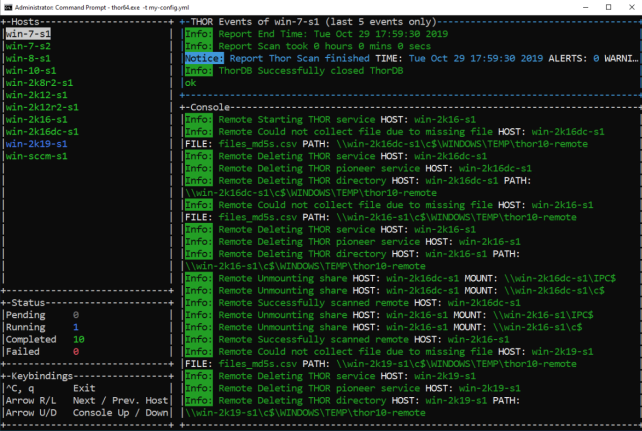
Remote Scanning
A feature named THOR Remote allows you to scan multiple Windows endsystems from a single privileged workstation. Think of it as a PsExec combined with the power of THOR.

Multi-Platform
THOR runs on all current and many older versions of Windows, Linux, macOS and AIX.
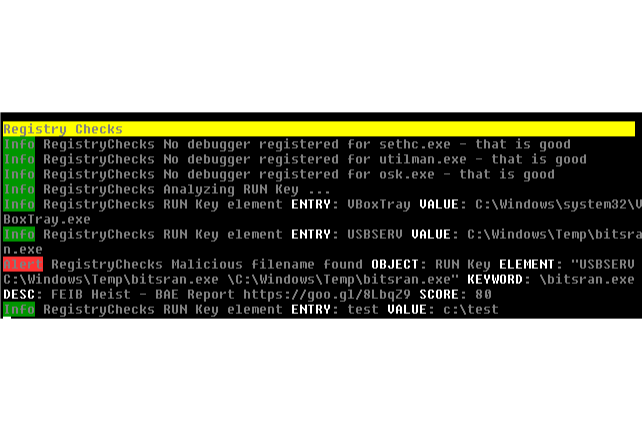
Registry Analysis
The Registry module applies the filename IOCs and THOR’s YARA rules for Registry detection to the loaded Registry and Registry Hives.
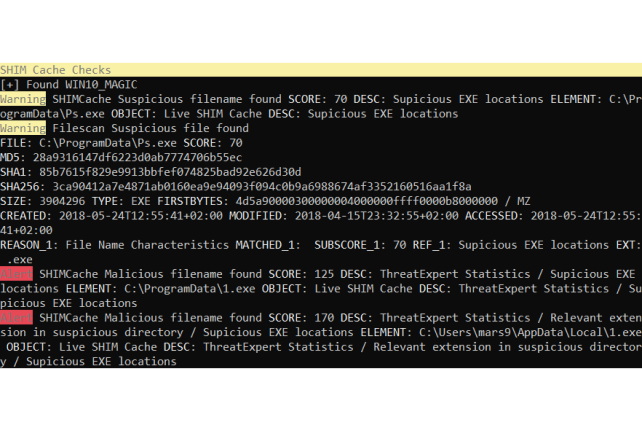
SHIM Cache Analysis
The SHIM Cache module analyses contents of the AppCompatCache on Windows systems, applies all filename IOCs, anomaly regex rules or just prints out all entries for your review. This module allows you to detect malicious or suspicious entries of programs that have been removed by adversaries long ago.
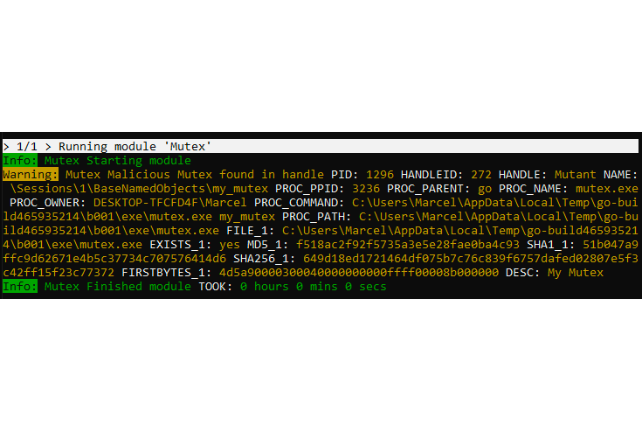
Mutex, Named Pipe, Event Analysis
Implants used by advanced threat actors are more challenging to detect using conventional methods and require more sophisticated inspection techniques.
THOR has a comprehensive set of malicious Mutex, Named Pipe and Event values and enriches each match with relevant metadata to facilitate the further analysis.
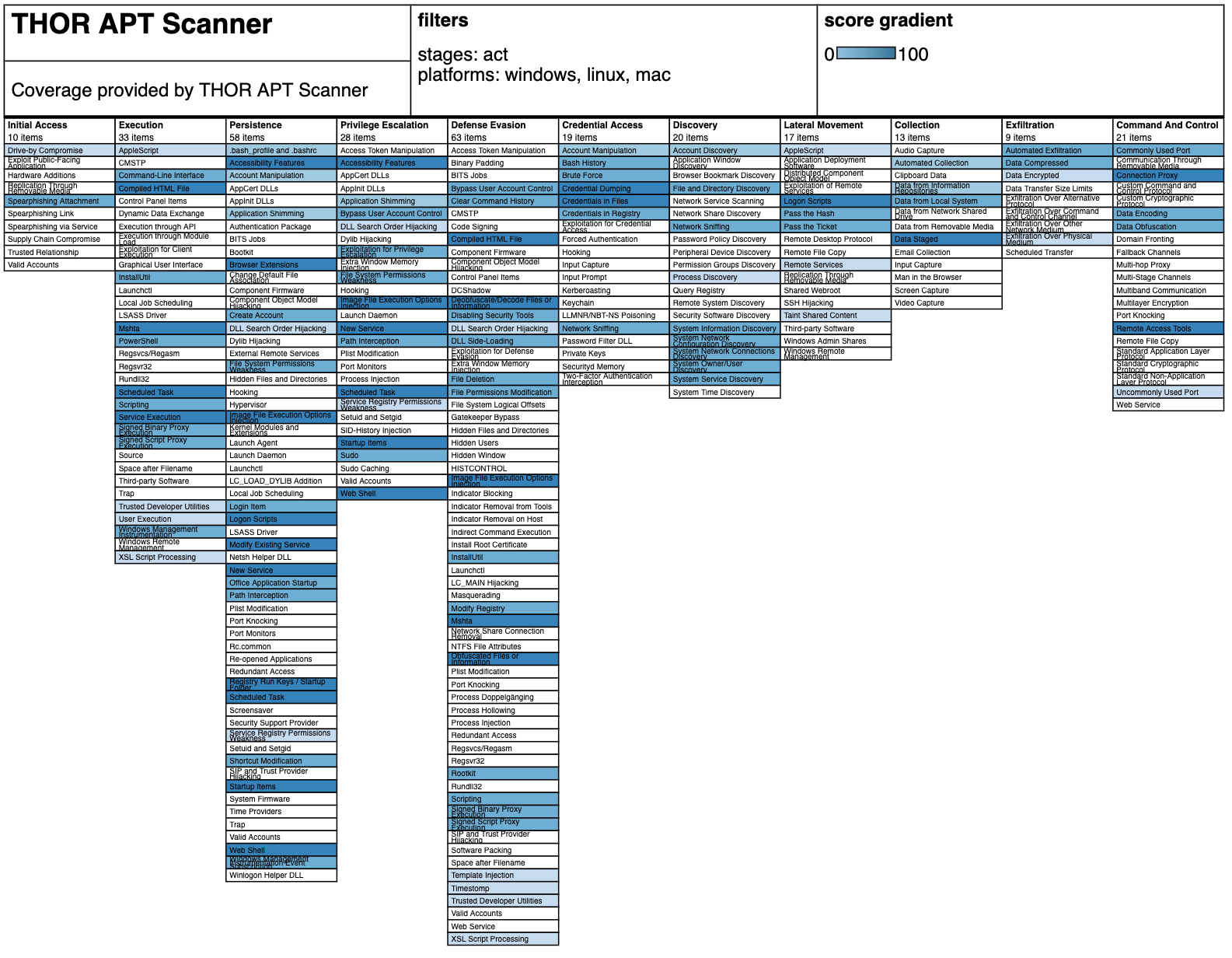
MITRE ATT&CK Coverage
With the ATT&CK Navigator and our JSON file, you can check THOR’s coverage of the respective attack methods.