Think of it as your ultra-fast on-premise scan service, which is bundled with more than 30,000 hand-crafted YARA rules focusing on persistent threats and forensic artefacts.
Collect files and submit them for analysis from any operating system and any hardware platform. The possibilities are limitless.

Low CPU and RAM Usage
A collection task requires 0.75-2% of the CPU and 20MB memory.

Any OS, Any Arch
Our collectors run on any operating system and processor architecture.

High Speed
It allows ultra fast collection runs. (Our tests: Win 10, collect last 3 days, any type, full disk = 3 minutes run).

Completely On Premise
THOR Thunderstorm can be installed on any internal system and runs as a service within your network.

Sample Storage
Store suspicious or all transmitted samples with a reference to the source system to facilitate the deeper analysis.

Forensic Modules
THOR Thunderstorm supports the analysis of different file types that get collected for forensic analysis purposes (e.g. EVTX files, Registry Hives).

Custom Signatures and IOCs
Add you own YARA signatures, Sigma rules, hash and filename IOCs and apply them to incoming samples.

Flexible Deployment
In addition to the server installer script we provide a set of simple collection tools, a Python-based API library with command line client and a set of helper scripts.

SIEM Integration
THOR Thunderstorm offers many ways to output information (Text, JSON, Syslog), which makes it easy to integrate the findings into your favorite SIEM system.
What is THOR Thunderstorm?
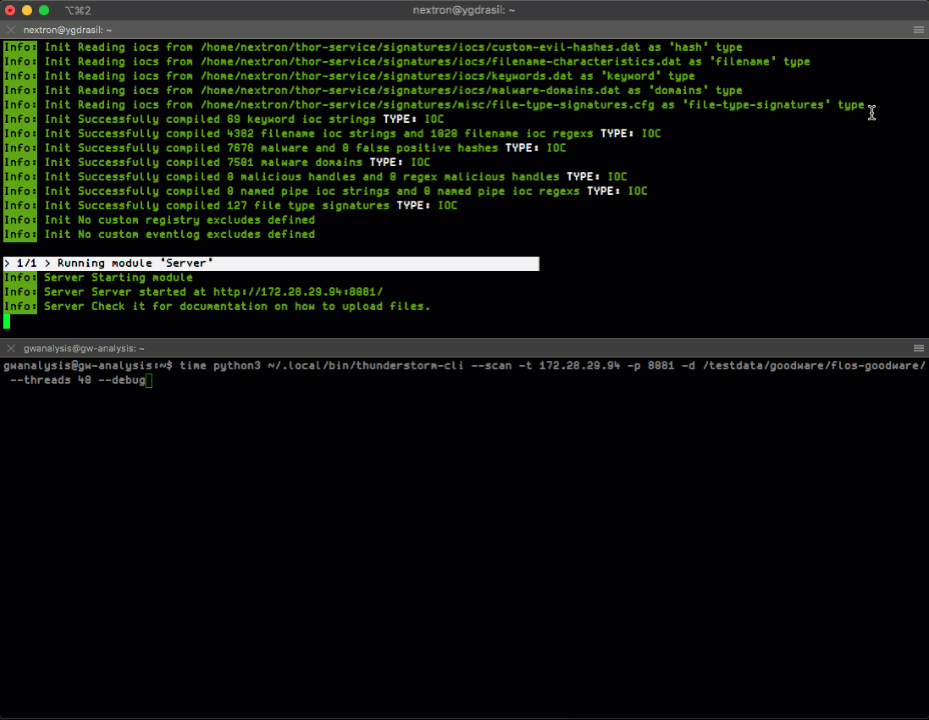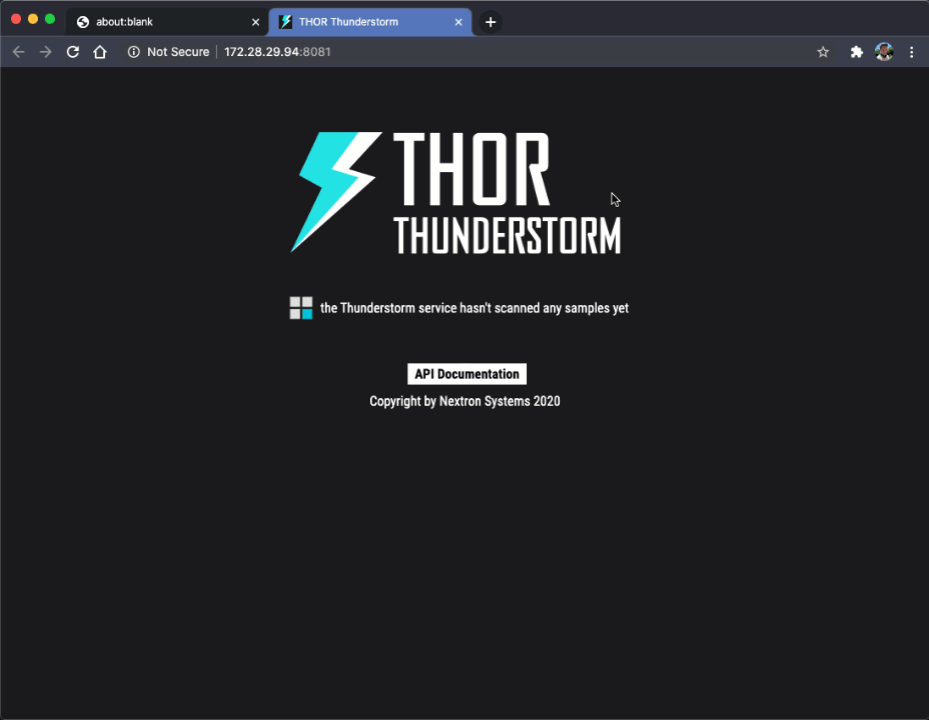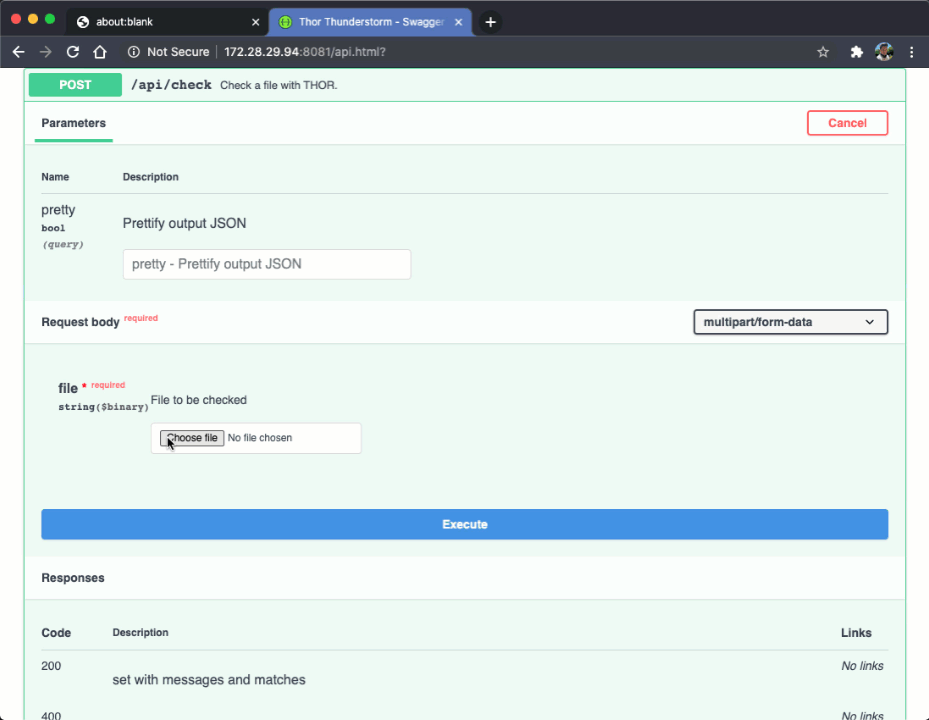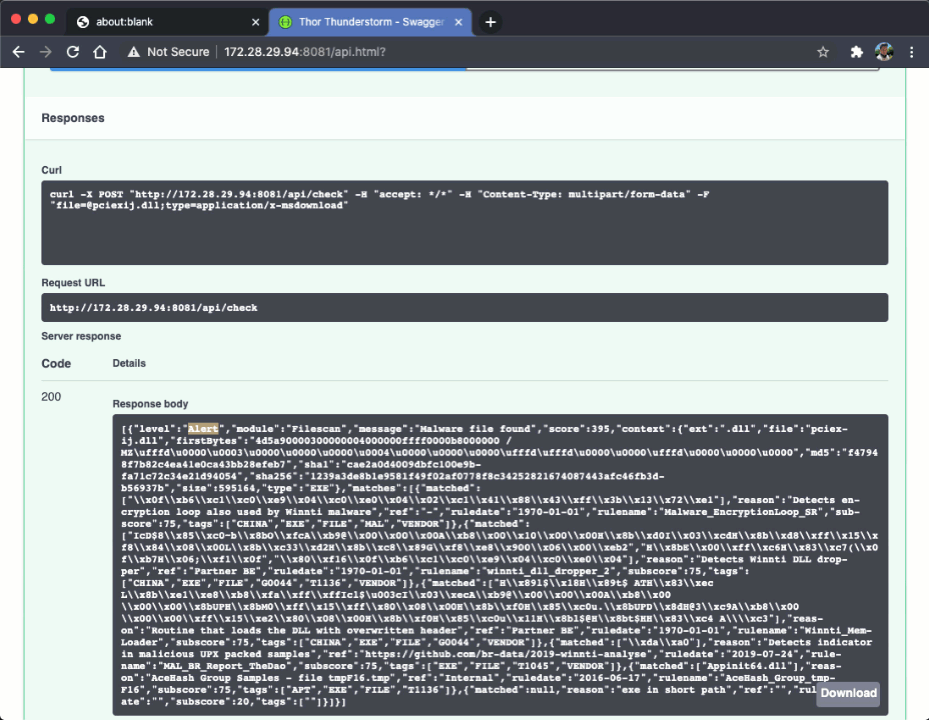
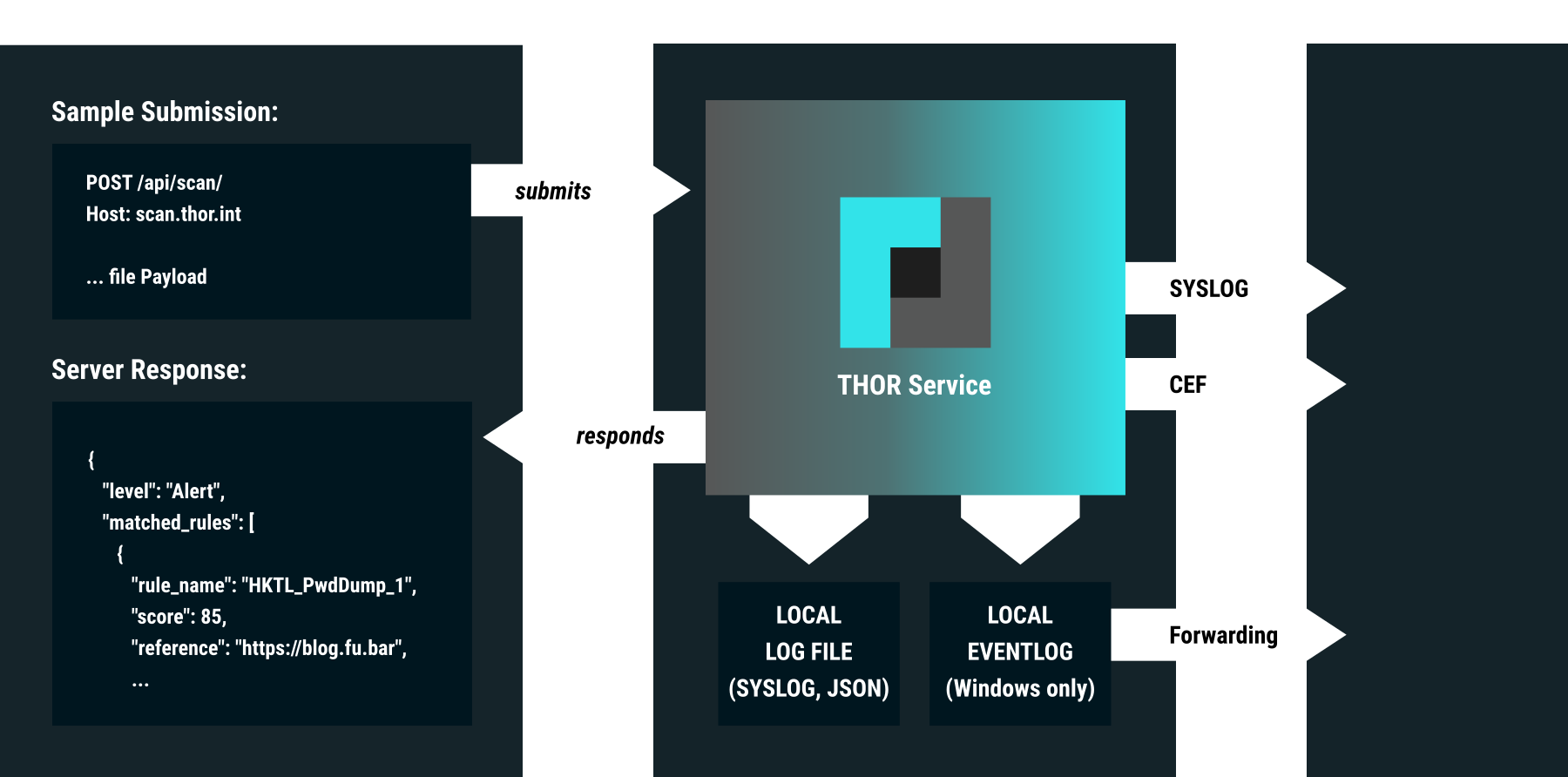
A RESTful web service that receives samples and returns a scan result.
It is feature-rich and very fast.
Use Cases
- Remote File Collection
- ICS Networks
- Out of Reach Devices
- Out of Reach Operating Systems
- S3 Bucket Scanning
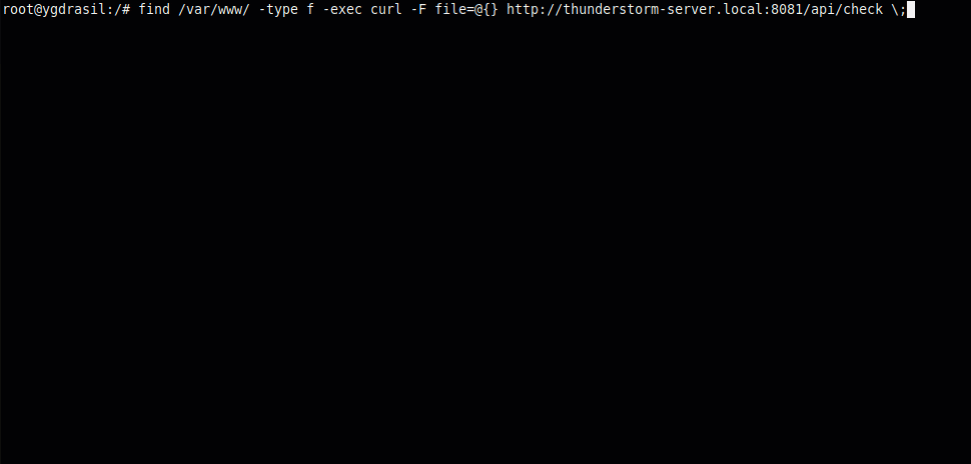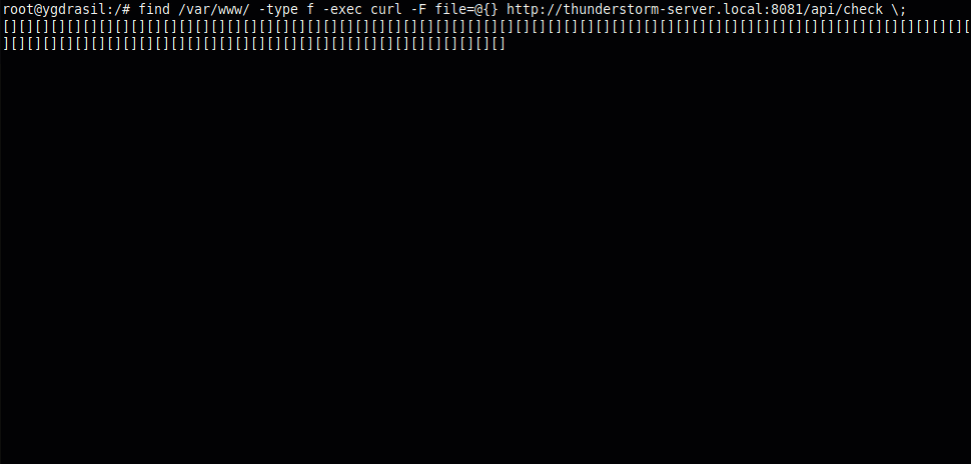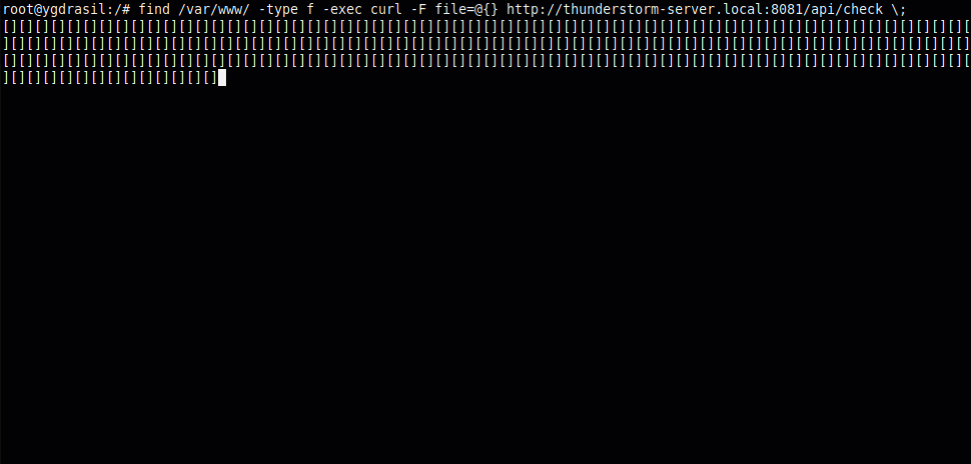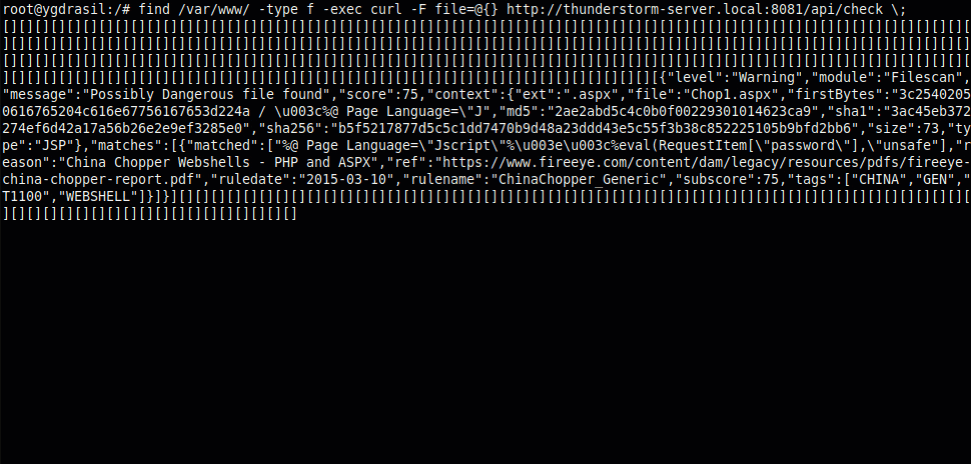
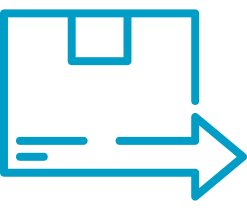
Alerts and warnings produced by THOR Thunderstorm highlight interesting elements in file data, registry hives, eventlog files and more.
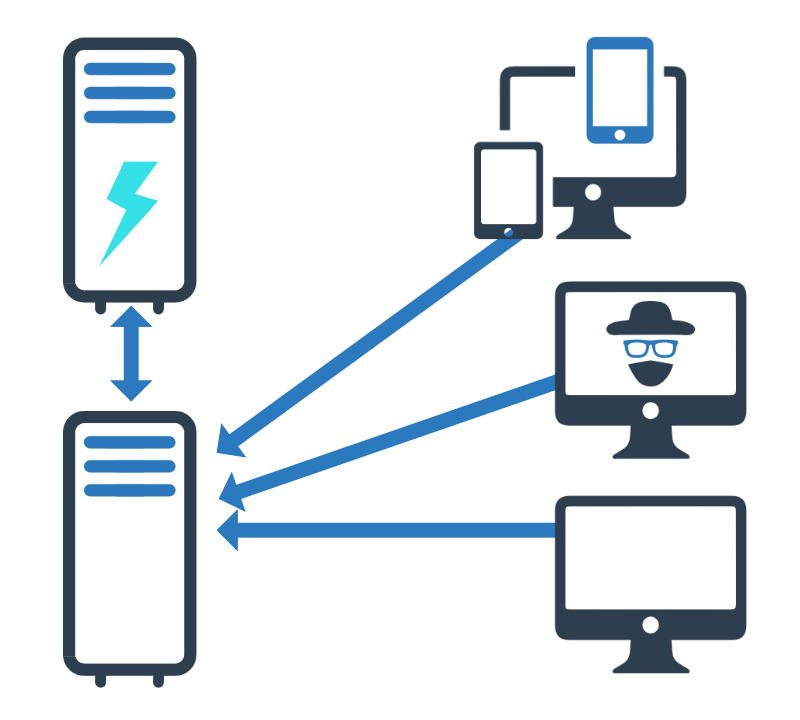
With THOR Thunderstorm, you just have to collect and submit the files.

Since file collection is a lot easier than endpoint scanning, all you need is way to export the remote system’s files or directly send them to THOR Thunderstorm.
Imagine that you can collect and submit files from network devices, telephone systems or embedded devices.
Select files based on size, age or type and schedule frequent upload tasks to analyze only new or modified files.

By using it in a container that scales with the demand, you can process millions of files in a few minutes.
Flexibility
Most operating system provide tools to walk the file system and submit files via HTTP. The examples below are intentionally short and compact to inspire you with their simplicity. Think of all devices that you could analyze this way. No agent, no portable scanner, just simple file submission via HTTP.
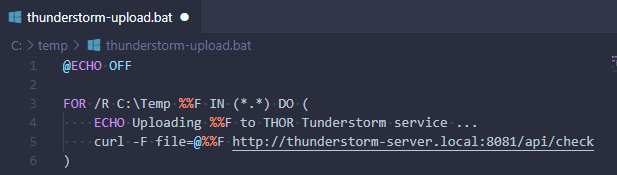
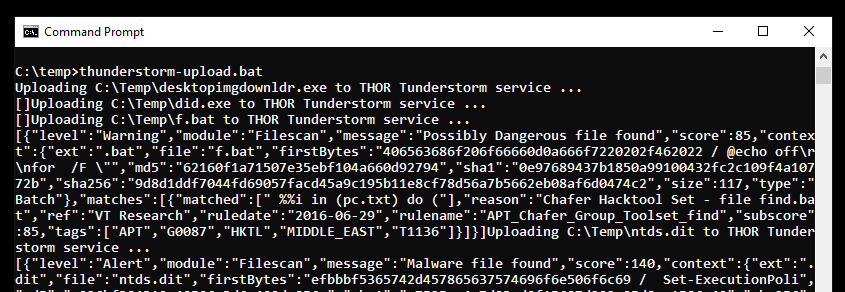
This example shows a simple batch file that walks recursively over a given folder an submits all files. You could extend it to the whole disk and reduce the submission to certain file extensions (e.g. exe, bat, ps1, js).
This examples shows how easy it is to get all files in a web server root checked by THOR Thunderstorm just by using bash, find and curl.
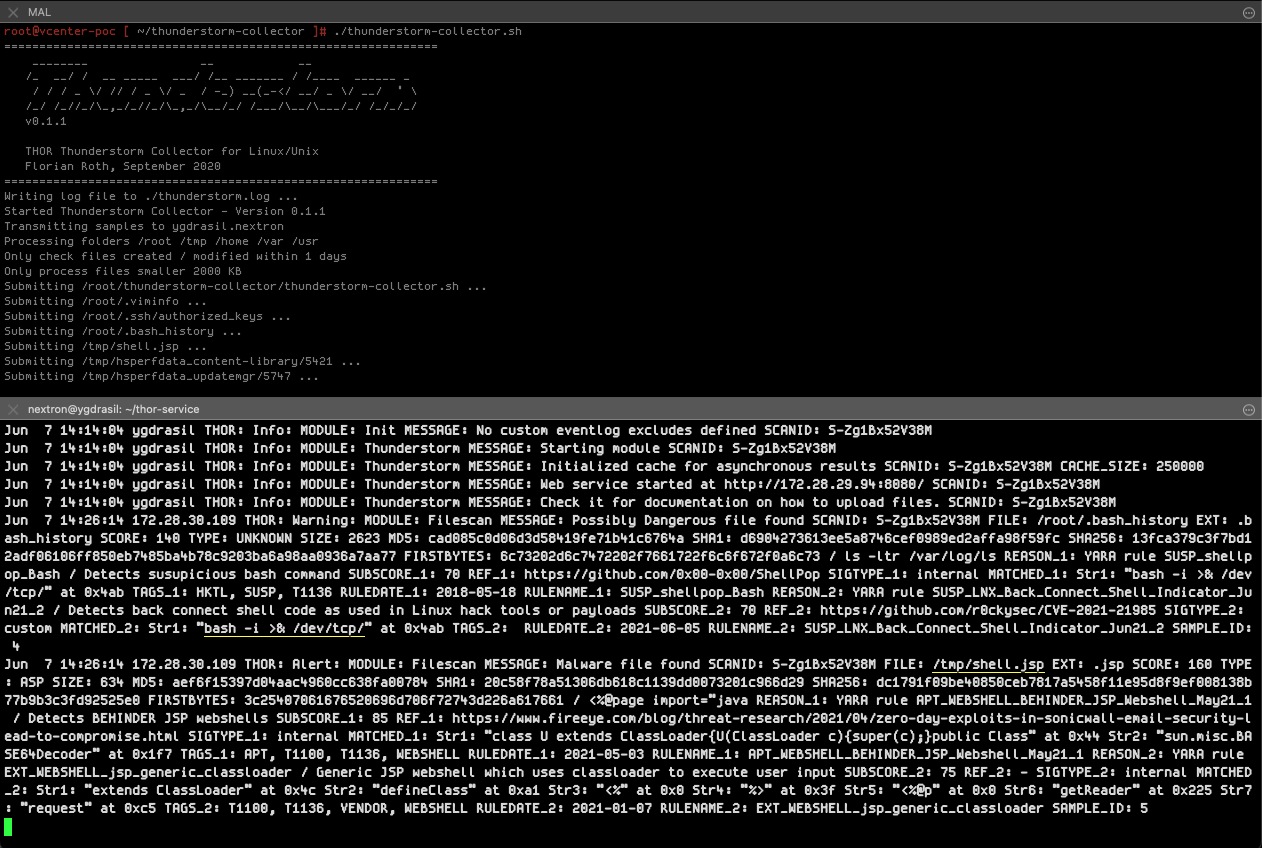
Modes of Operation
The service can be started in two scan modes: Pure YARA or Full-Featured YARA
Pure YARA
In the pure YARA mode (--pure-yara) THOR Thunderstorm only applies the 30,000 internal and all custom YARA rules to the submitted samples. It’s leightweight and super fast.

Full-Featured YARA
The full-featured mode is the default. In this mode Thunderstorm also parses and analyses Windows Eventlogs (EVTX), registry hives, memory dumps, Windows error reports (WER) and more. It’s not just a YARA scan, but a full forensic processing.
Collectors
The Thunderstorm Collector repository contains a Go based collector, precompiled for many different operating systems and architectures as well as collectors scripts (Batch, Bash, PowerShell).
We have pre-build collectors for Windows, Linux, macOS, AIX, Solaris on x86, x64, Arm, PowerPC, MIPS, RISC-V, Plan9, S390x (IBM Z) architectures.
These collectors allow you select files based on age, size and type for submission to a Thunderstorm server.
API Client
We provide a Python module and Python based API client that supports multi-threaded submission to the THOR Thunderstorm service.
The API documentation is embedded into the web service itself. You can even send requests right from the browser to test it live.
Web GUI
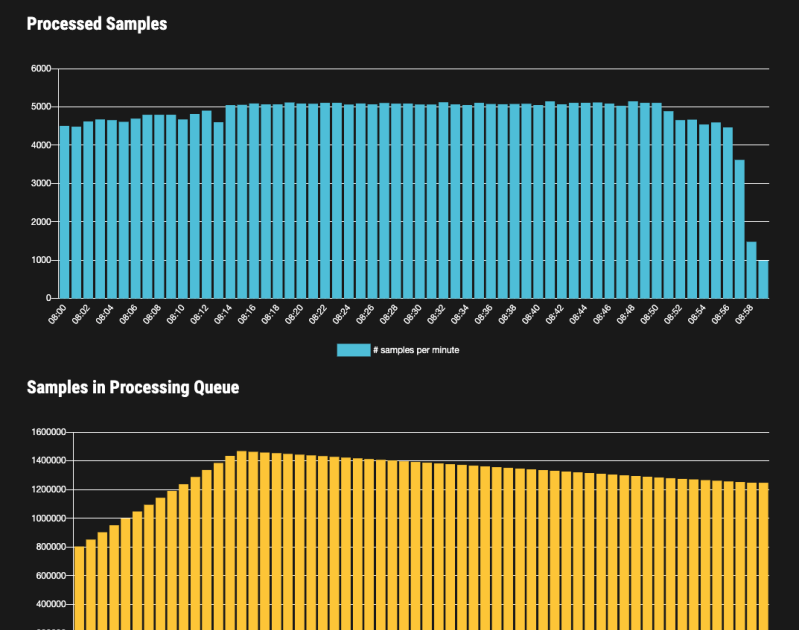
The Web GUI contains important information about the service like the signature set version, uptime, number of processed and queued samples and much more.
It contains some graphs that help you to assess the actual server load and processing speed.
It also contains links to the API documentation, the Python API library and the Thunderstorm Collectors for your convenience.