Detection at its best.
Nextron Systems specializes in providing cutting-edge security solutions for Threat Detection and Response (TDR). Our goal is to assist you in safeguarding your company’s digital assets against an ever-evolving threat landscape.
Impressive Detection Rate
THOR’s impressive detection rate is well-known in the industry and fits the needs of threat hunters around the globe.
Unmatched Flexibility
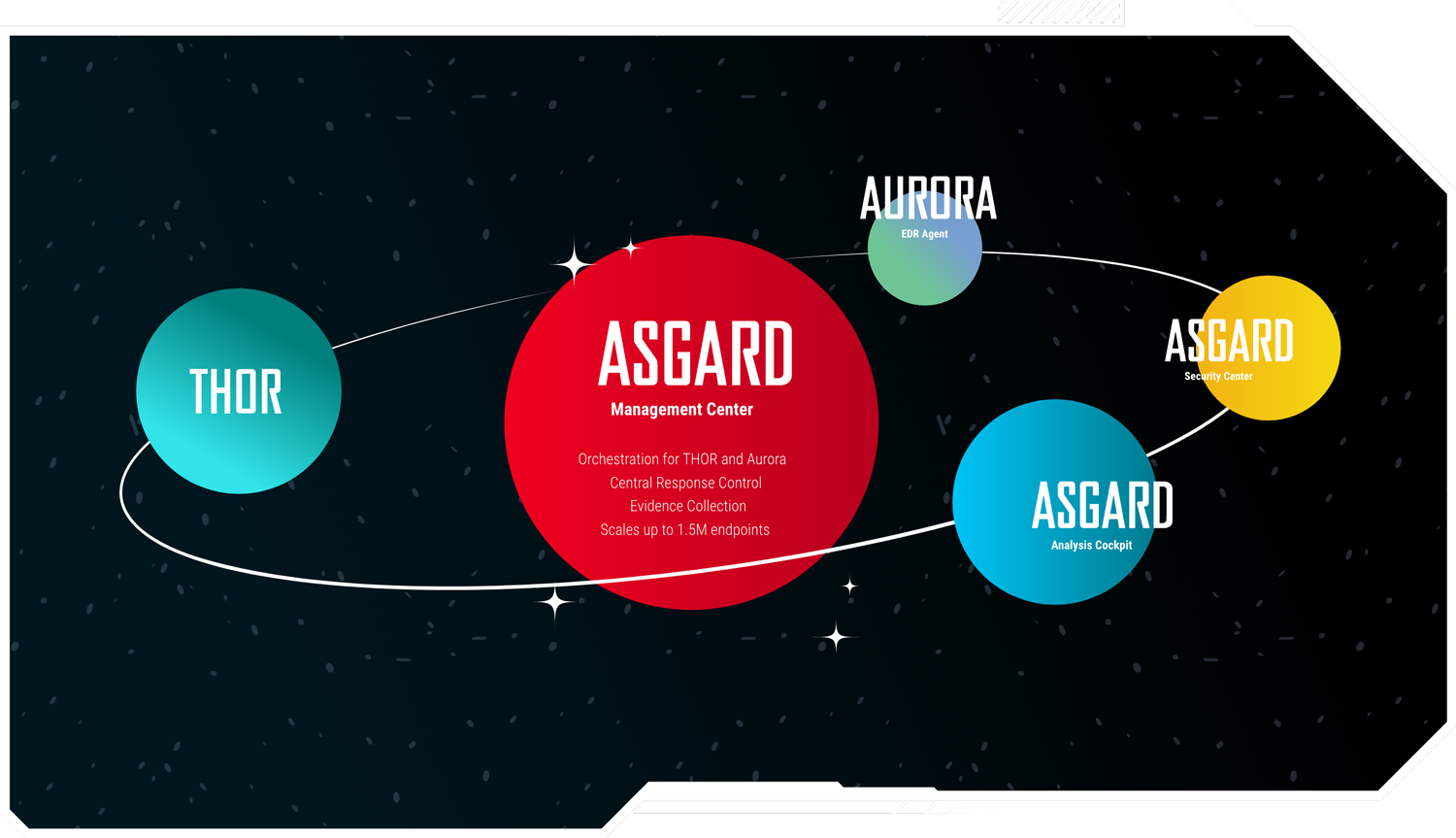
Use our scanners fully managed with the ASGARD platform or stand-alone as portable scanners.
Trans-Regional Trust
We are a German-based company, and all of our solutions can be used on your premises.

Take advantage of our strength
Continuous Compromise Assessment
Stay one step ahead of cybercriminals and protect your business! With Nextron, you can proactively detect advanced hacker activities earlier than ever before and reduce the likelihood of security breaches many times over.

Incident Response
Have you already been hacked? Now is the time to act fast! Nextron provides you with a quick assessment of the extent of the compromise and implements effective countermeasures to prevent a recurrence.


Forensic Analysis Tools
Save time and still be effectively protected against hacker attacks? With Nextron’s powerful tools for fast ad-hoc scanning of endpoints and images, you can save yourself extra work.

Our Partners
Nextron Product Universe
News & Insights

Protecting Your Business: Addressing the Microsoft Exchange Vulnerability Crisis
Discover how to safeguard your business from the ongoing Microsoft Exchange vulnerability crisis highlighted by the German Federal Office for Information Security (BSI). Learn about critical warnings, the importance of patching, and how automated compromise assessments with THOR Cloud Lite can fortify your cybersecurity strategy.

Unveiling KamiKakaBot – Malware Analysis
Back in January 2023 Group-IB first reported and documented the TTPs of DarkPink, an APT group that targets the Asia-Pacific regions. We’ve been monitoring KamiKakaBot samples since September of last year. And at the start of this year in January we’ve noticed 2 new...

Tales Of Valhalla – March 2024
Every month the Nextron Threat Research Team (NTRT) shares insights into evasive threats that we’ve seen in the wild via our Valhalla service. The aim is to highlight interesting samples our rules detected and have or had very low detection rates as reported by...
Our Experts
“I founded Nextron to be a hub for innovation in detection engineering. Our aim is to set new standards and develop tools and rules that expand the detection capabilities of traditional software, focusing on identifying unknown threats. My driving force is the commitment to ensure that the bad guys don’t get away with what they do.”
Boris Deibel
Director Managed Services
Head Healthcare Business (DACH)
„Helping prospects to design the best solution architecture and supporting clients to maximize the value they get from Nextron is an extremely satisfying job.“
We are hiring!
Do you want to become part of a competent team of experts and help in the fight against cyber criminals? Then join us in the Nextron cosmos and get to know us – we look forward to meeting you!













