It is everything that EDRs aren’t:
- it is completely transparent and fully customisable due to the open Sigma rule set and configuration files
- it saves 99% of the network bandwidth and storage
- it works completely on-premises, no data leaves your network
- it can be configured to use only a limited amount of resources
We offer an enterprise and a “Lite” version, which is free of charge. The free version uses only the open source rule set, lacks comfort features and a central management.

100% Transparency
You always know exactly why a rule triggered and can adjust that rule to your needs. Every rule has descriptions and references that explain the author’s intentions. No machine learning magic that generates tons of false positives.

Highly Customizable
Aurora features built-in detection rules for multiple stages of a kill chain, addressing different user requirements. However, unique enterprise environments might need additional rules and adjustments. Aurora allows users to modify and add new rules to meet these specific needs.

Minimal Network Load and Storage Costs

Completely On-Premises
Your confidential data never leaves your network.

Limited Resource Usage
AURORA allows you to throttle its CPU usage and event output rate. These optional throttling options allow you to set priorities and put your system’s stability first.

Free Version
What are the main differences to Sysmon?

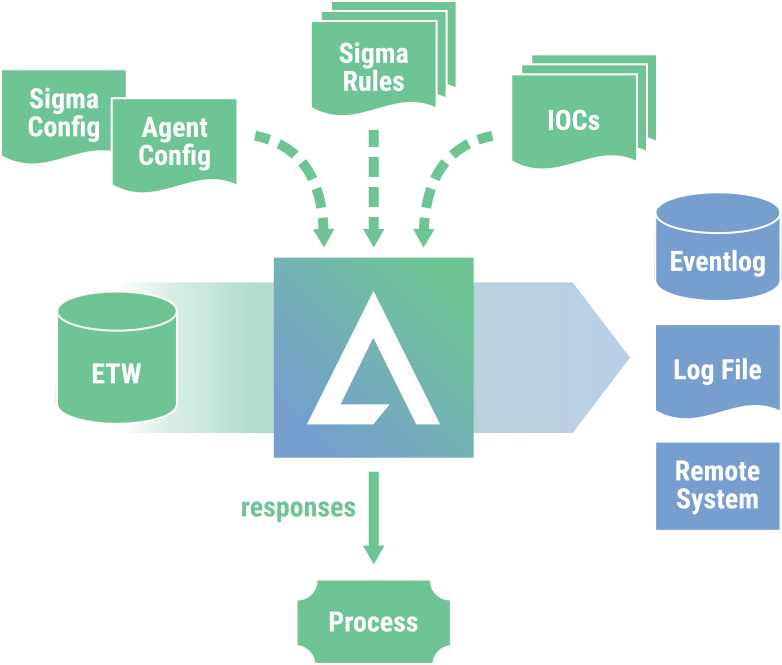
AURORA reads data from many different ETW channels and enriches this data with live information to recreate events that are very similar to the events generated by Sysmon.

The relative log volume is very low as AURORA only submits the events on which a Sigma rule triggered.

AURORA supports different output channels: Windows event log, log file, UDP/TCP targets.

The integrated throttling features put the system’s stability first.

It requires no additional kernel driver and therefore poses a limited risk to the system’s stability.
AURORA Lite
Free Community Edition- Sigma-based event matching on ETW data
- Open source rule set
- Without Nextron’s Sigma rule set
- Open source IOC set
- Without Nextron’s IOC set (used in THOR)
- Alert output channels: Eventlog, File, UDP/TCP
- No comfortable management with ASGARD
- No additional detection modules
- 5 rules with response actions
- No rule encryption
AURORA
Full-Featured Agent- Sigma-based event matching on ETW data
- Open source rule set
- Nextron’s Sigma rule set
- Open source IOC set
- Nextron’s IOC set (used in THOR)
- Alert output channels: Eventlog, File, UDP/TCP
- Comfortable management with ASGARD
- Additional detection modules
- Unlimited number of response actions
- Rule encryption
Not Included in the Free Version
No Nextron Sigma Rule Feed
AURORA Lite ships with the Open Source rule set and allows users to add custom rules. It does not contain Nextron’s private Sigma rules, developed and maintained by Florian Roth and his research team.
Without THOR's IOC Set
No Comfortable Management
No Extra Modules
Only 5 Response Actions
No Encrypted Rules
Licensing Differences
You can use AURORA Lite for:
- Use on any local, state, federal or international government agency.
- Educational and research purposes.
- Internal company use.
You need AURORA Enterprise for:
- Use on third-party networks.
- Use as part of a paid engagement.
