THOR Cloud is our new, lightweight and easy to deploy on-demand compromise assessment scanner.
THOR Cloud eliminates the need for on-premise systems for licensing and scanner package downloads. With THOR Cloud, all you need is a small yet powerful tool known as the THOR Cloud launcher. Simply bring it to your endpoint or allow end users to download and execute it themselves.
This launcher serves as the core of a comprehensive on-demand forensic investigation, powered by our advanced scanner, THOR. Equipped with over 30,000 pre-built signatures designed to detect various traces of hacking activity, THOR ensures thorough analysis and identification of potential security threats.


No Requirements - No Hassle

In-Depth Investigations

Easy Integration
THOR Cloud Lite
Free Community Edition- Scans with THOR Lite
- Windows, Linux and macOS
- 30 scans per month
- Basic IOC management
- Limited Coverage (open source YARA and IOC rule set)
- No commercial use allowed
THOR Cloud Lite Plus
Free until June 30, 2024- Scans with THOR Lite
- Windows, Linux and macOS
- up to 1,000 scans per month
- Advanced IOC management
- Commercial use allowed
- Sigma scanning
- Encrypted reports (private key)
- Limited Coverage (open source YARA, Sigma and IOC rule set)
THOR Cloud
Enterprise- Scans with full THOR version
- Windows, Linux and macOS
- Full coverage (all 27 THOR modules)
- Full Nextron rule sets (30,000 YARA, Sigma and IOC rules)
- Advanced IOC management
- Commercial use allowed
- Sigma scanning
- Encrypted reports (private key)
Lightweight Deployment
Easily deploy and run THOR scans using the lightweight THOR Cloud launcher binary, simplifying the setup process.
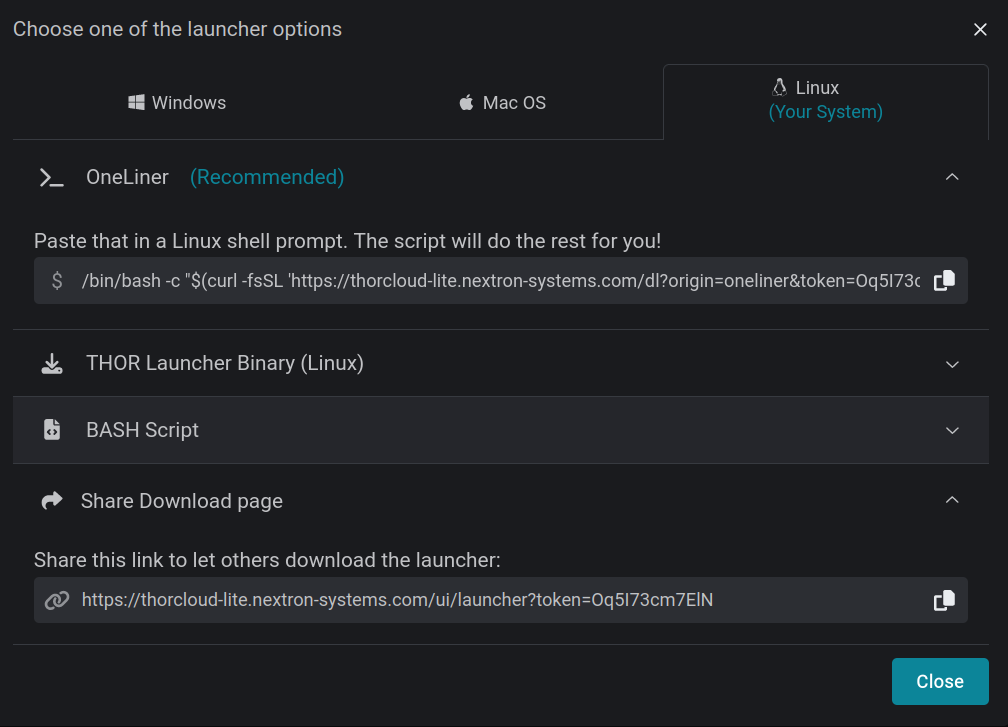
Download options in admin interface
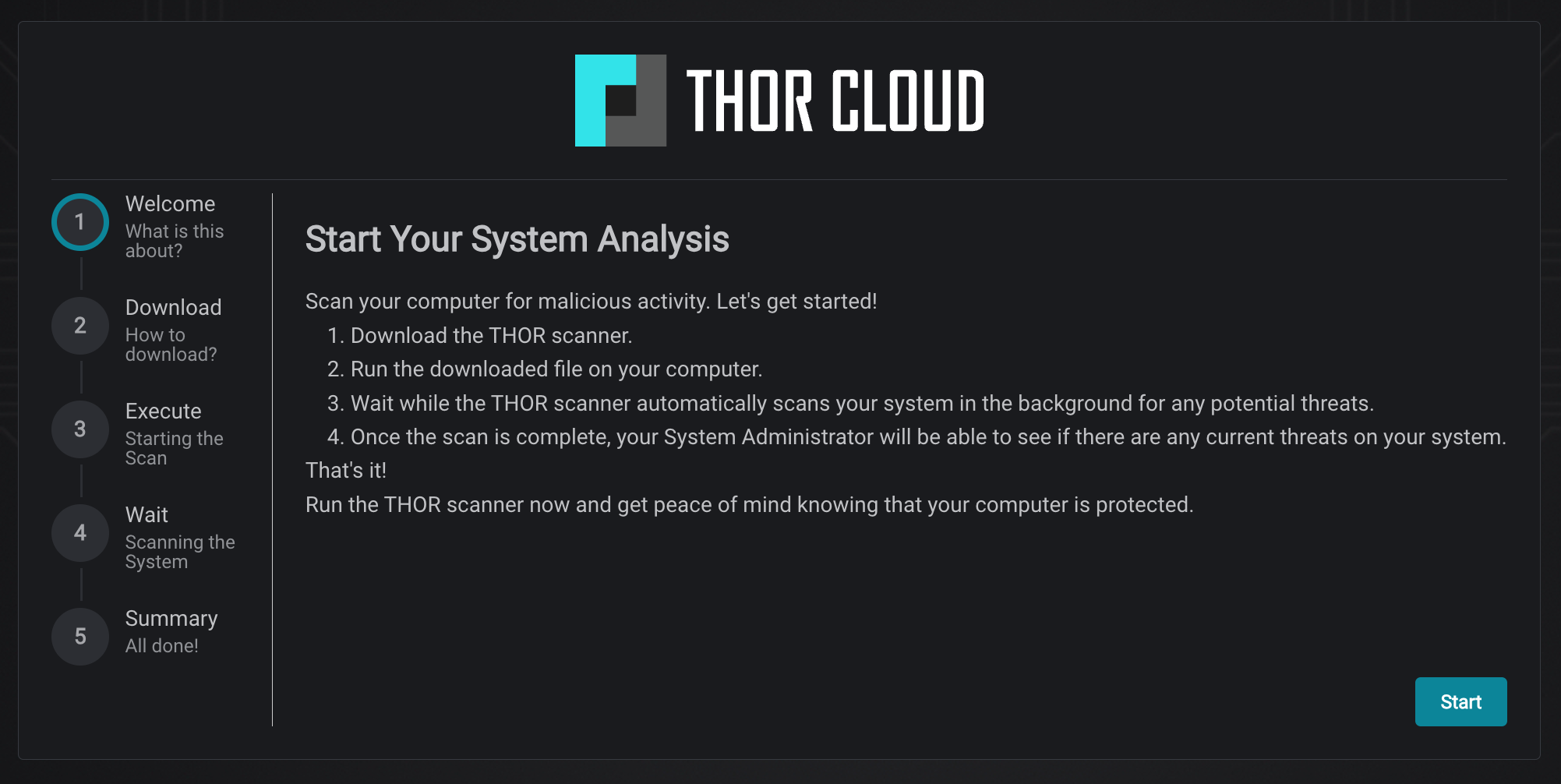
Guided launcher download for end users (optional)
Centralized Cloud Management
Enjoy the convenience of central management for scans through the intuitive web-based GUI, providing a unified interface for configuration and monitoring.
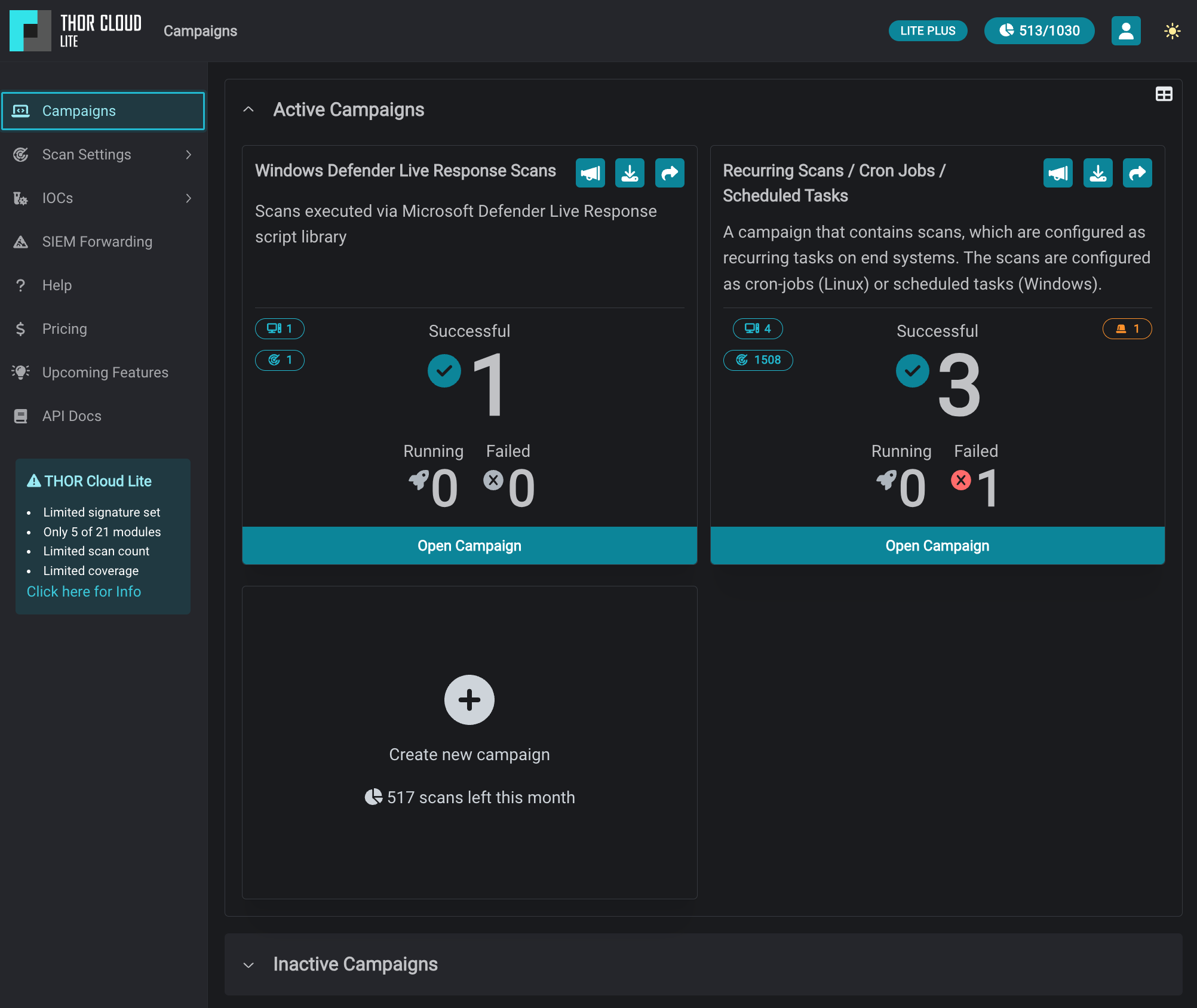
No On-Premises Server or Agents
Benefit from a serverless and agentless approach with THOR Cloud. There’s no need to maintain on-premises servers or deploy additional agents, simplifying your infrastructure requirements.

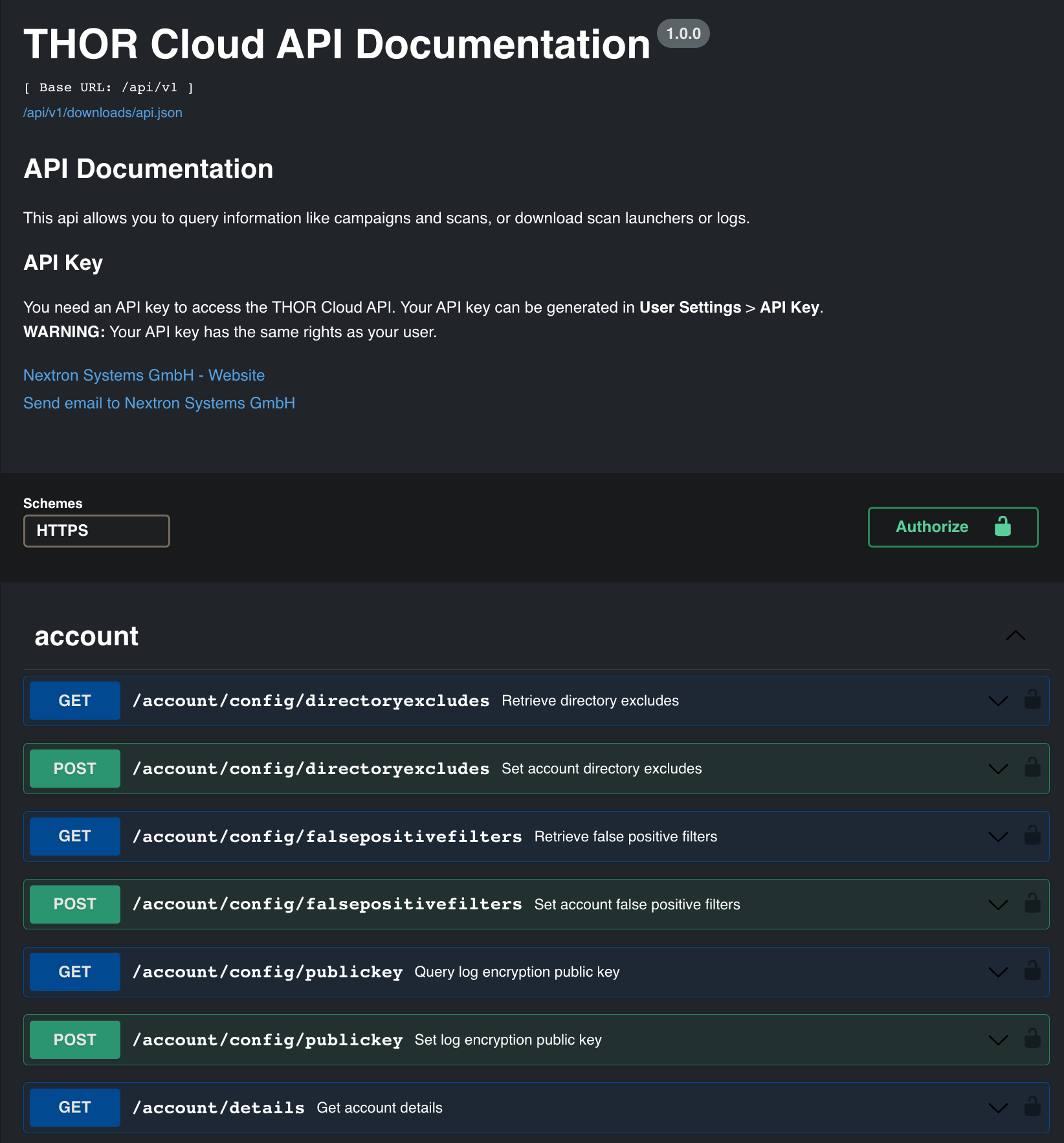
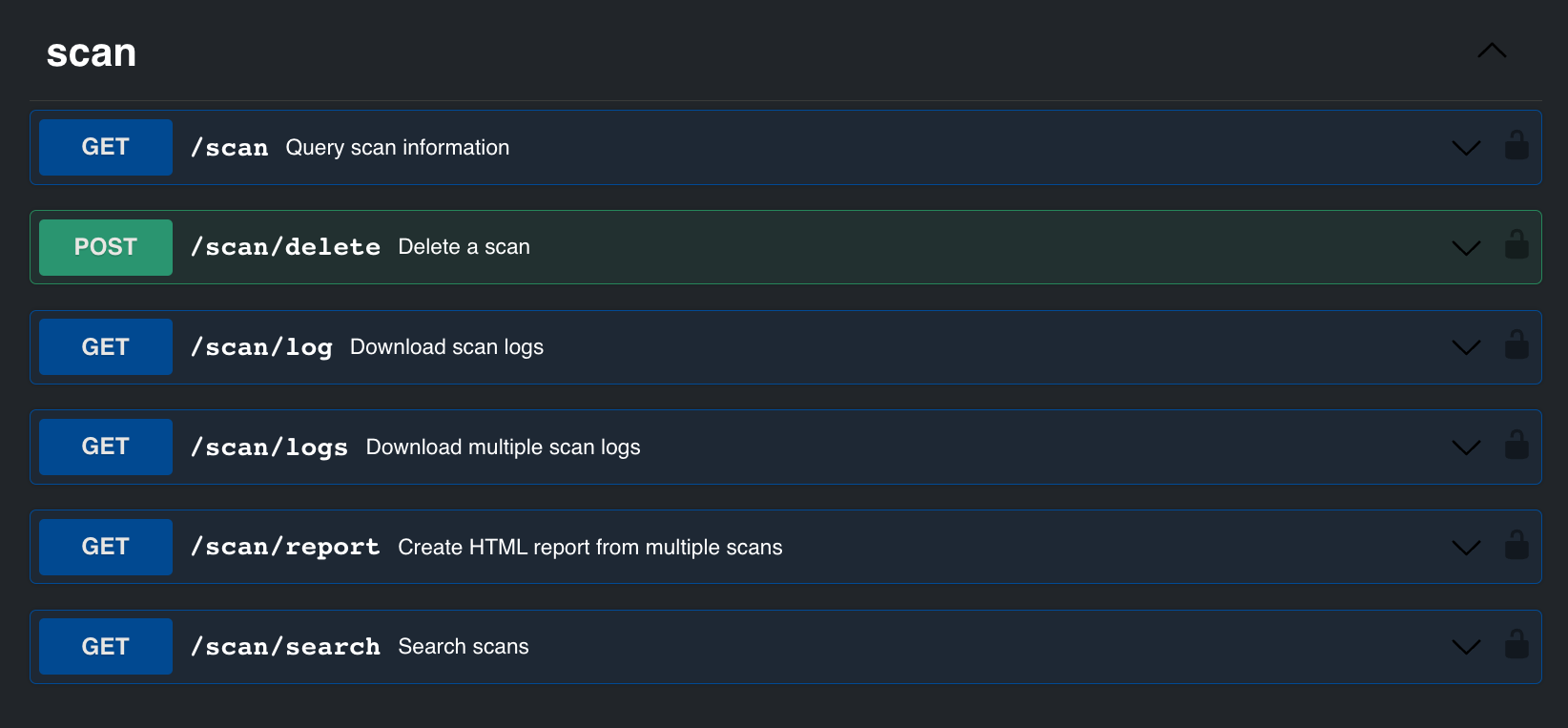
Full Featured API
Leverage the power of the comprehensive THOR Cloud API, enabling seamless integration and customization within your existing systems and workflows.
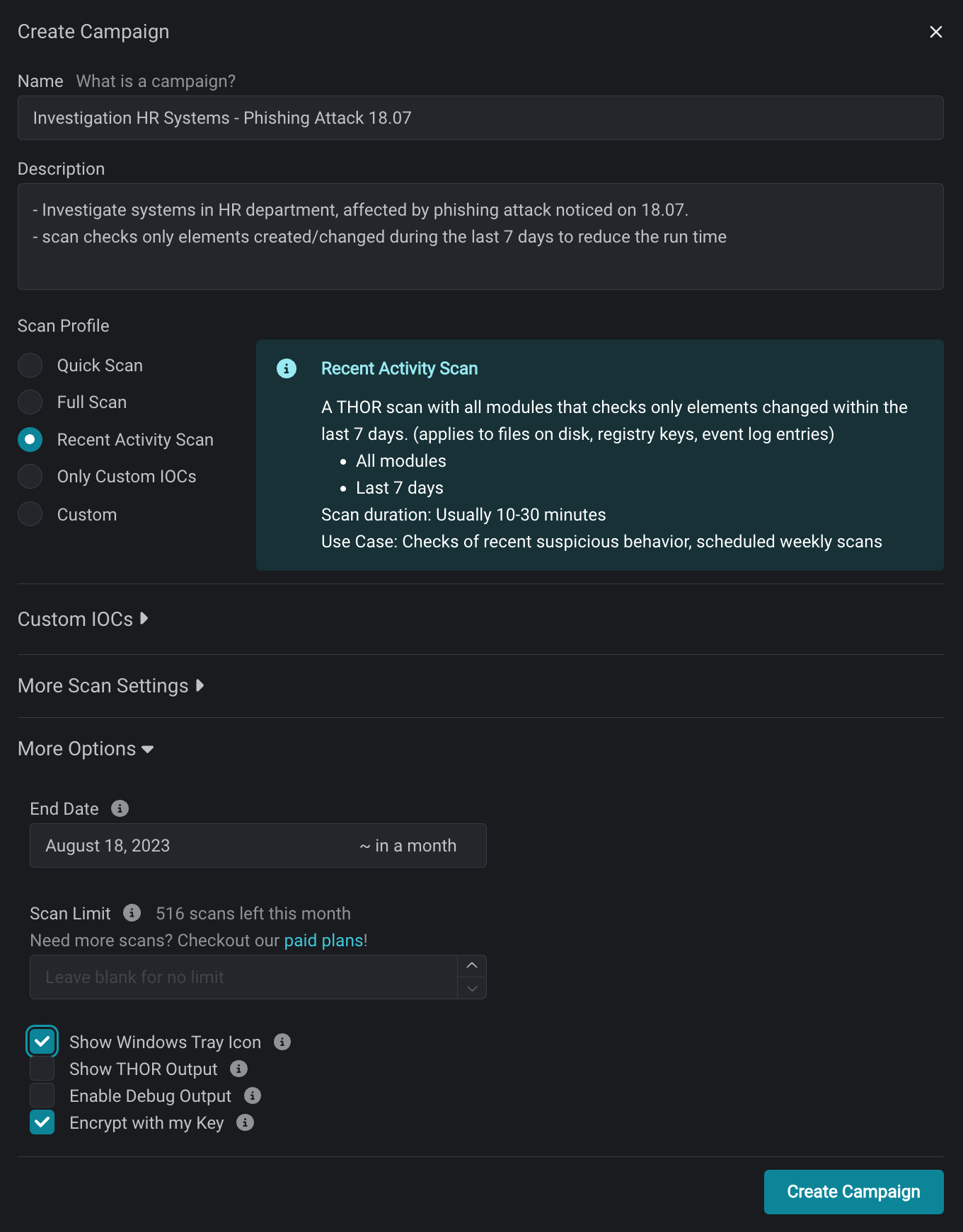
Command-Line Free
Say goodbye to complex command-line interactions. THOR Cloud eliminates the need for command-line operations, streamlining the scanning process.
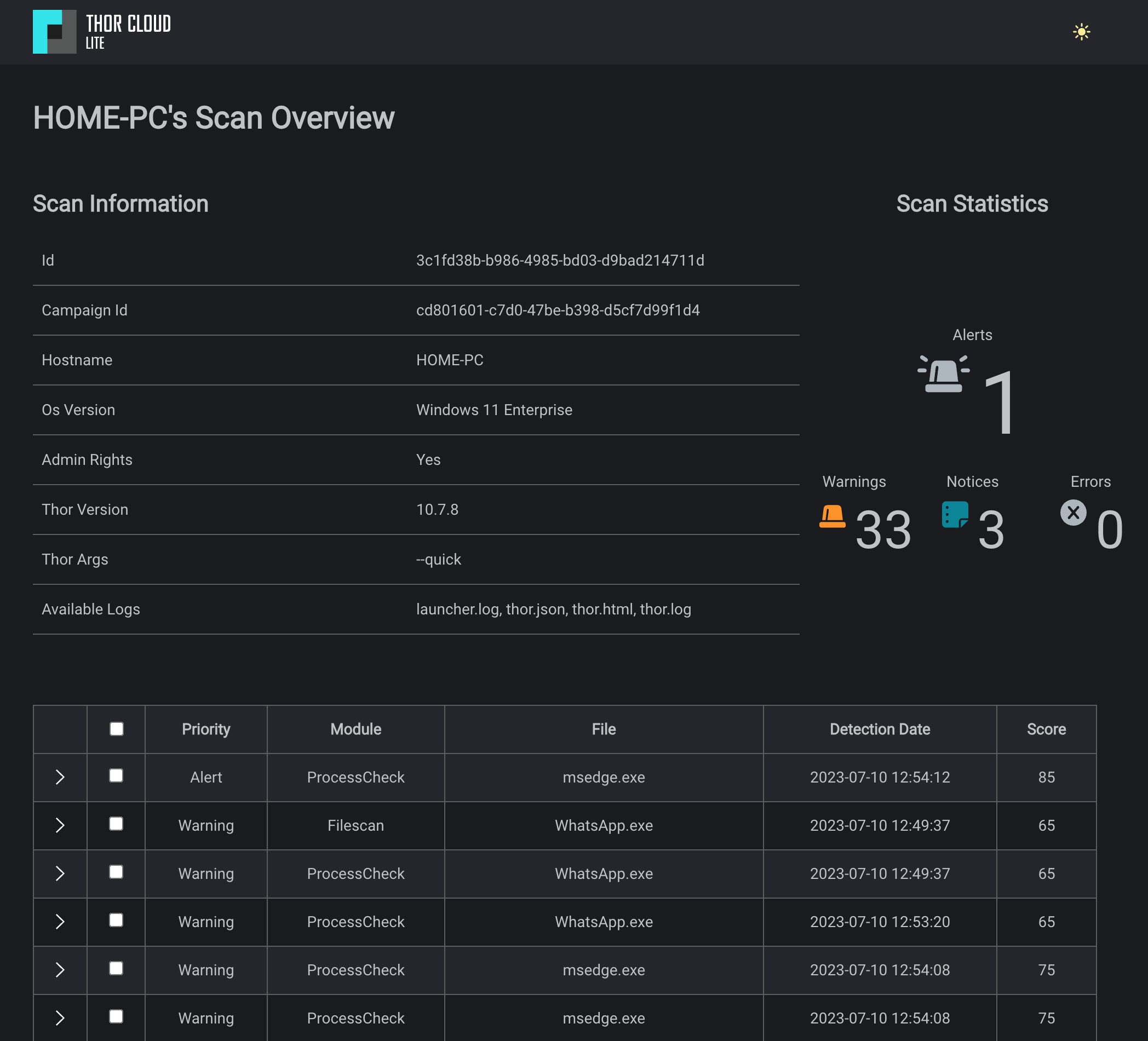
Comprehensive Reports
Scans generate various output files, including an HTML report that provides analysts with a prioritized view of the scan log.
With quick investigation and qualification of security events taking just minutes, THOR Cloud serves as an ideal extension to support your SIEM or EDR analysts in gathering additional information and forensic evidence.