Why Customers Choose Nextron
Over 500 customers around the globe trust our products including Fortune Global 500 companies, government agencies and NGOs.
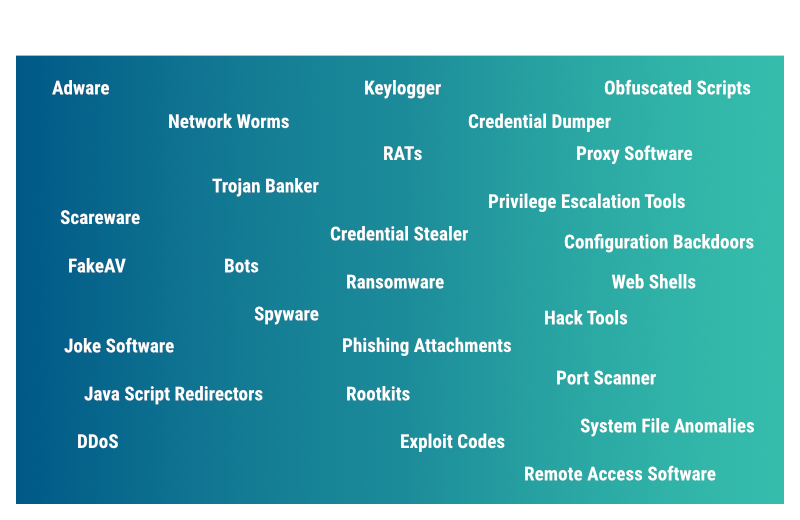
We detect what your Antivirus and EDR misses
Our research focuses on backdoors, hack tools, obfuscated scripts, web shells, and adversary activity that the usual Antivirus and EDR misses to detect.


Automated Compromise Assessments
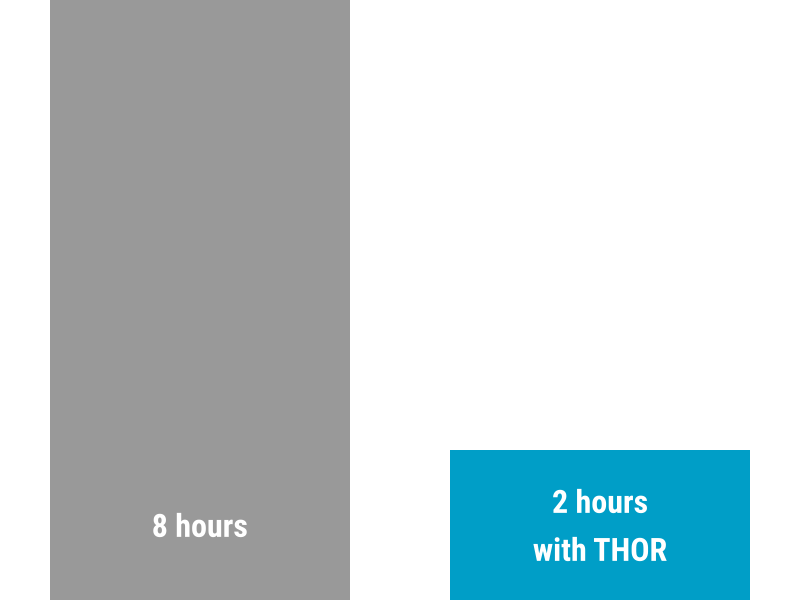
Checking a system for traces of attacker activity is a time-consuming and laborious task. Our scanner THOR automates compromise assessments and removes the need for tedious work.

Accelerated Forensic Analysis
THOR allows your forensic analysts to focus on the important work. It uses thousands of patterns, YARA and Sigma rules to preprocess forensic images and highlight suspicious elements. It speeds up the analysis process substantially, uncovers malicious activity sooner, saves time and money.

Flexible Deployment
THOR can be used as a stand-alone scanner, on thousands of end systems controlled from an ASGARD Management Center or as a web service in form of THOR Thunderstorm collecting from outdated or exotic operating systems.

Unlimited Possibilities
Our scanners and agents run on Microsoft Windows, Linux, macOS and some IBM AIX variants. However, the collectors for THOR Thunderstorm run on just any operating system. You can scan live systems, disk images or specific forensic evidence like EVTX files, memory dumps or Registry hives.


Everything is On-Prem
Our scanners don’t communicate with a remote system. They can even be used in air-gapped networks. Your confidential data never leaves your network.

Stability has Top Priority
THOR does not require a tangible scanner or agent hooks functions. THOR also does not require the need to install a driver. They can adjust their workload to the system’s resources and don’t interfere with other installed security software like an Antivirus or an EDR.

Highly Customizable
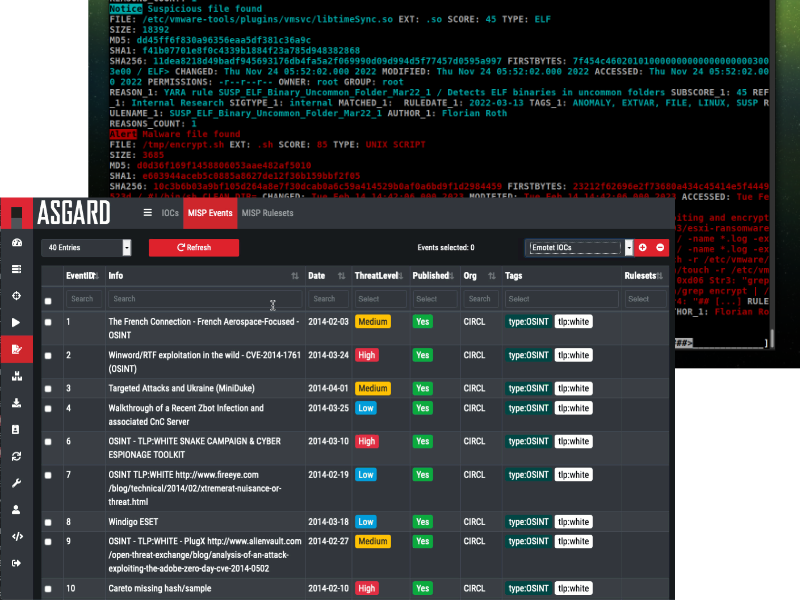
It’s important to be able to scan any malicious threats your organization may face. We make it seamless to add and maintain your own IOCs and rules. THOR accepts many different types of IOCs and ASGARD offers native MISP integration.

