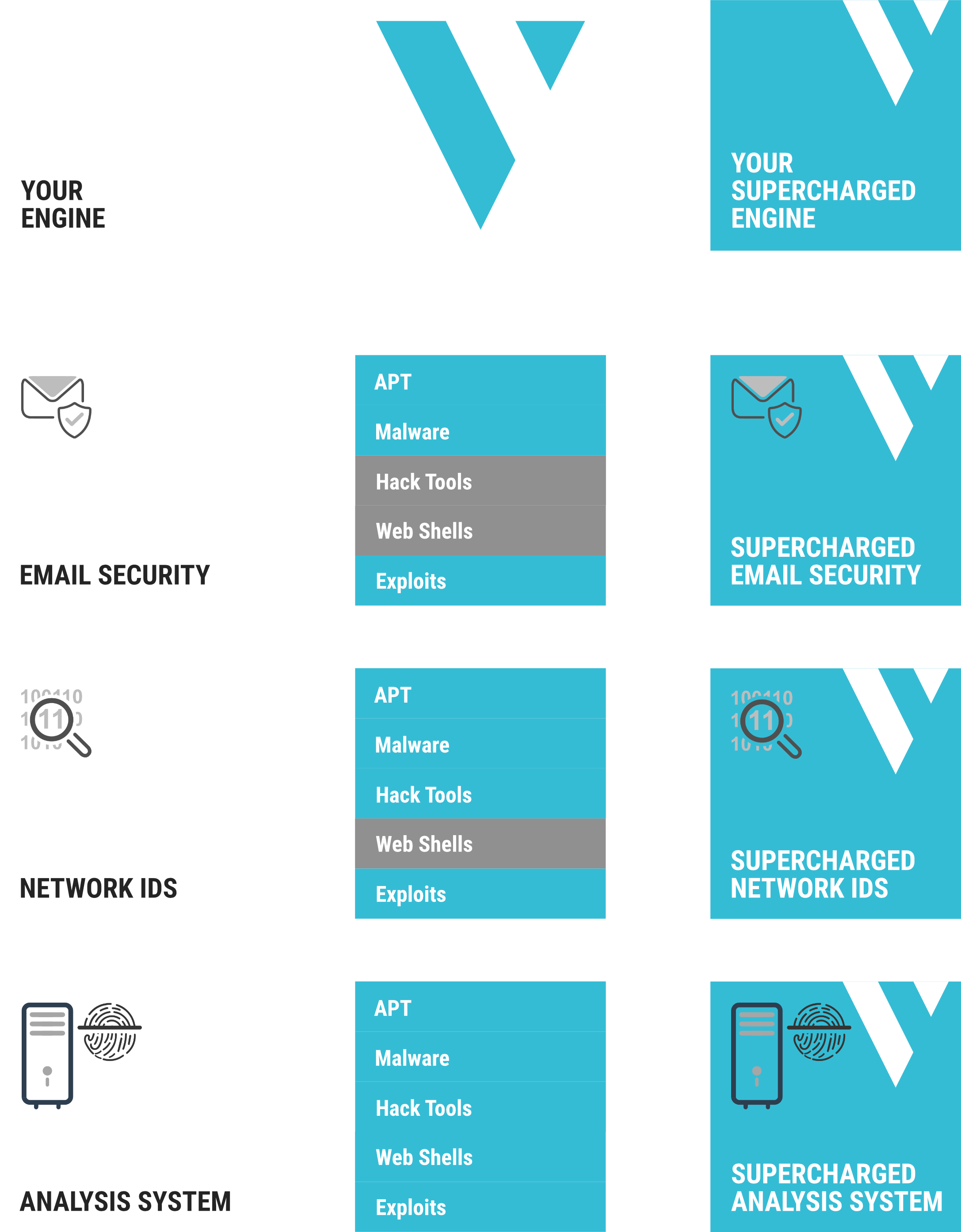
VALHALLA boosts your detection capabilities with the power of thousands of hand-crafted high-quality YARA and Sigma rules.
Our team curates more than 20,000 quality tested YARA rules in 8 different categories: APT, Hack Tools, Malware, Web Shells, Exploits, Threat Hunting, Anomalies and Third Party. The first five of them can subscribed, the other three are only used in a compiled and encrypted form in our scanner THOR.
Valhalla’s database grows by around 1500 YARA and 250 Sigma rules every year. A subscription includes the curation of old rules. We change and improve between 300 and 500 old rules every year.
With access to Valhalla, you can supercharge your detection by adding most of our highly successful THOR scanners’ signatures to your own scan engines.
All rules are performance optimised and quality tested against Terabytes of goodware and other data.
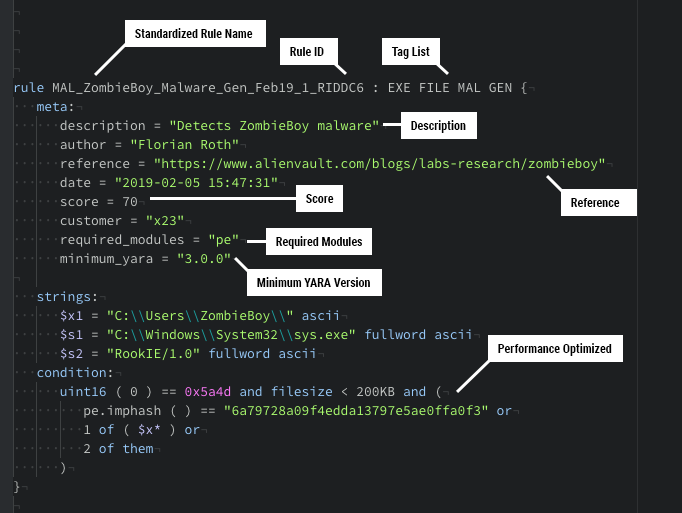
Rich Meta Data
Valhalla provides rich meta data that adds valuable context to each match, such as a web reference, related threat group campaigns, hashes of samples for which the rule was initially created and a list of public samples on which the rule has matched so far.
Each rule contains information about the required YARA version and modules to run that rule.
The API client allows you to retrieve only those rules that your product supports.
The rule’s score and tags indicate its reliability and scope. Both can be used to select the perfect rule set for your application.
Smart API
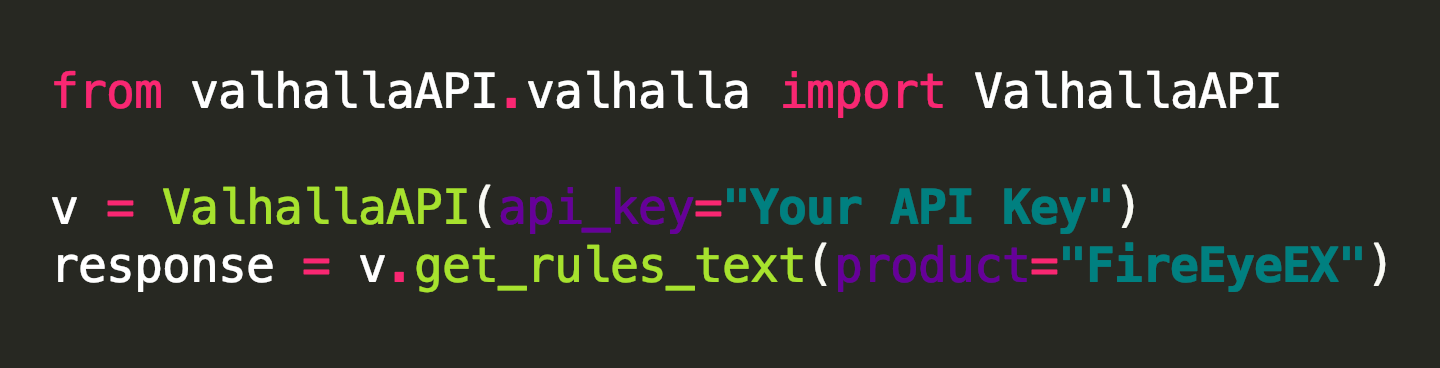
The Python module allows you download the subscribed categories as text or JSON object. It even has presets for well-known products that support YARA scanning like FireEye’s appliances, Tenable, Tanium, CarbonBlack or Symantec MAA.
It requires no more than 3 lines of code to retrieve the subscribed YARA rule set.
Web Site
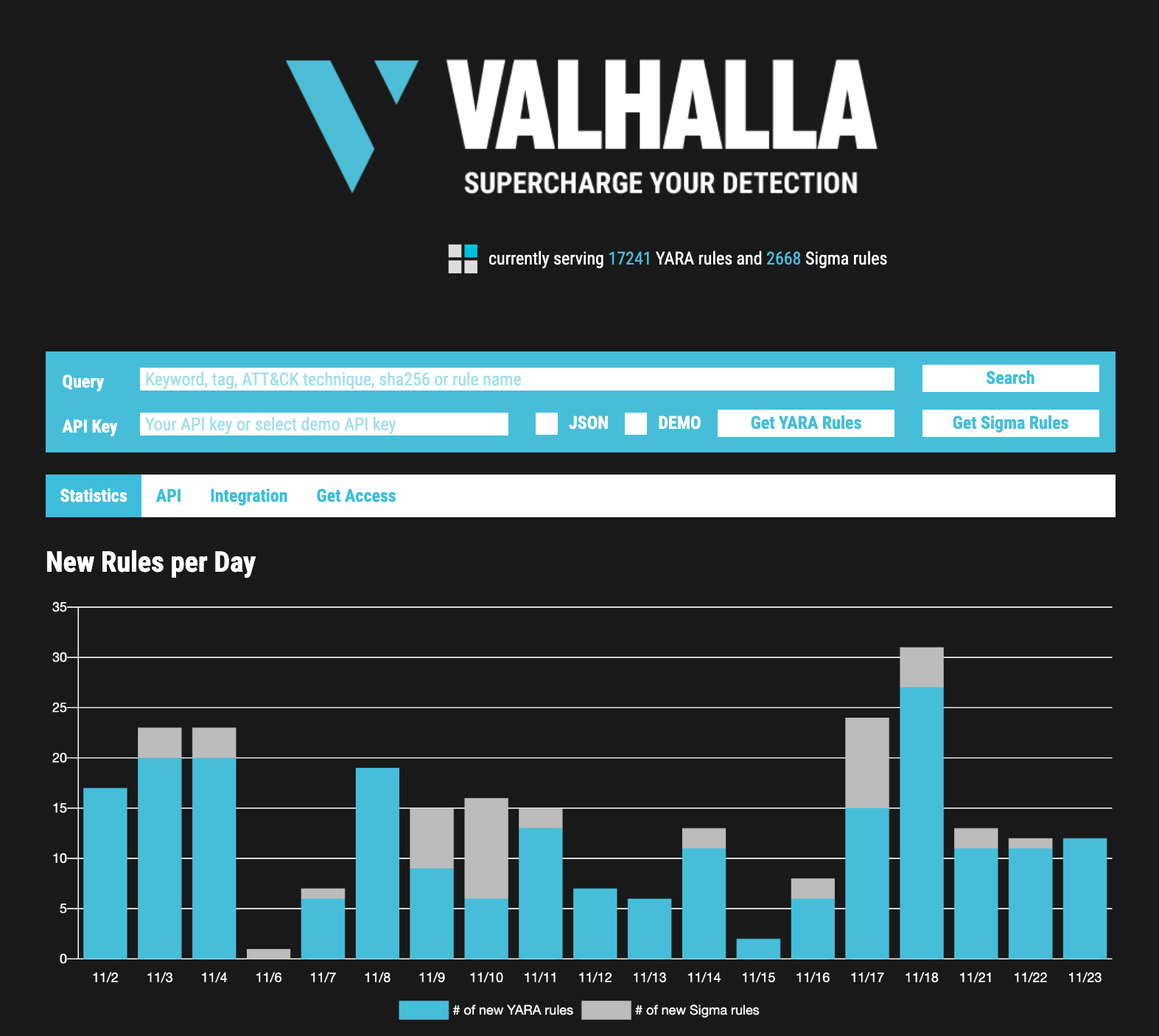
The website https://valhalla.nextron-systems.com allows you to immediately retrieve your subscribed rules using nothing but a web browser.
Just insert your API key and click on “Get Rules”.
You can also select the “JSON” checkbox to get them in JSON format or select “DEMO” to test drive this feature with a demo API key, which allows you to retrieve all public YARA or Sigma rules in the selected format.
The website also contains statistics about the current rule set.
Command Line Client
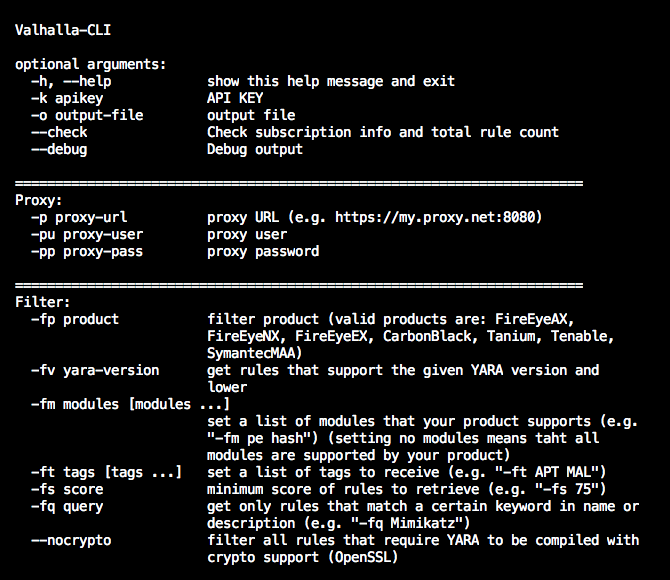
The comfortable command line client ‘valhalla-cli’ helps to integrate the rule retrieval into your deployment process.
It’s really as simple as it gets.
It can be installed running the following command:
pip3 install valhallaAPI
The next command retrieves all subscribed rules:
valhalla-cli -k APIKEY
The command line client supports proxy servers and allows you to apply numerous filters, e.g.
- Exclude rules with low scores
(e.g. threat hunting rules with scores lower than 75) - Exclude rules that wouldn’t work on your scan engine (e.g. “Tanium”)
- Retrieve only rules with certain tags
(e.g. “CHINA”, “APT”)

(note: the API key shown in the animated GIF is not valid anymore)
Integration
The web API allows you to retrieve the perfect set that integrates seamlessly with the platform that you use for YARA scanning. Depending on your use case, we recommend subscriptions for different rule categories.
Note: The feed cannot be downloaded or used on Microsoft Windows or macOS systems.
Growth
The rule set grows by 1000 to 1500 hand-written and quality tested rules per year.
Delivery
You can download the full subscribed set via web browser or use our public API client written in Python to get a customized rule set that fits your scan engine.
Subscription
We offer subscriptions for each of our rule set categories or the whole curated rule set.
Each subscription includes improvements, fixes and updates on the subscribed categories for 12 months.
Performance Optimization
All rules are used in our scanners and therefore optimized for performance. The planned version 1.1 of the API will allow you to pull less strict rule sets that are more effective for in-memory detection and the detection in data streams.
Curation
We improve between 300 and 500 old rules per year. These improvements include false positive reductions and the tightening or extension of existing rules.
Trial
We cannot offer a trial of our rule set.
However, the public API allows you to retrieve and test a streamlined demo rule set, which is an equivalent of the public signature-base that is integrated in our free scanners LOKI and THOR Lite
Special Strengths
APT
- High grade rules for malware and tools used by threat groups
- Based on public reports, our own undisclosed threat intel work, threat intel partners, threat exchanges and active incident response cases (mainly Europe, Asia and the Middle East)
Web Shells
- Often very low Antivirus detection ratio
- One of the things most EDRs are unable to detect
Hack Tools
- Rules to detect a variety of offensive security tools and frameworks
- Rules cover the tool itself, output, helper files and special command line parameters to detect their use in log files
Threat Hunting (only in THOR)
- Generic rules / heuristic detection methods focus on methods and obfuscation instead of specific threats
- Highly effective in detecting new, yet unknown threats
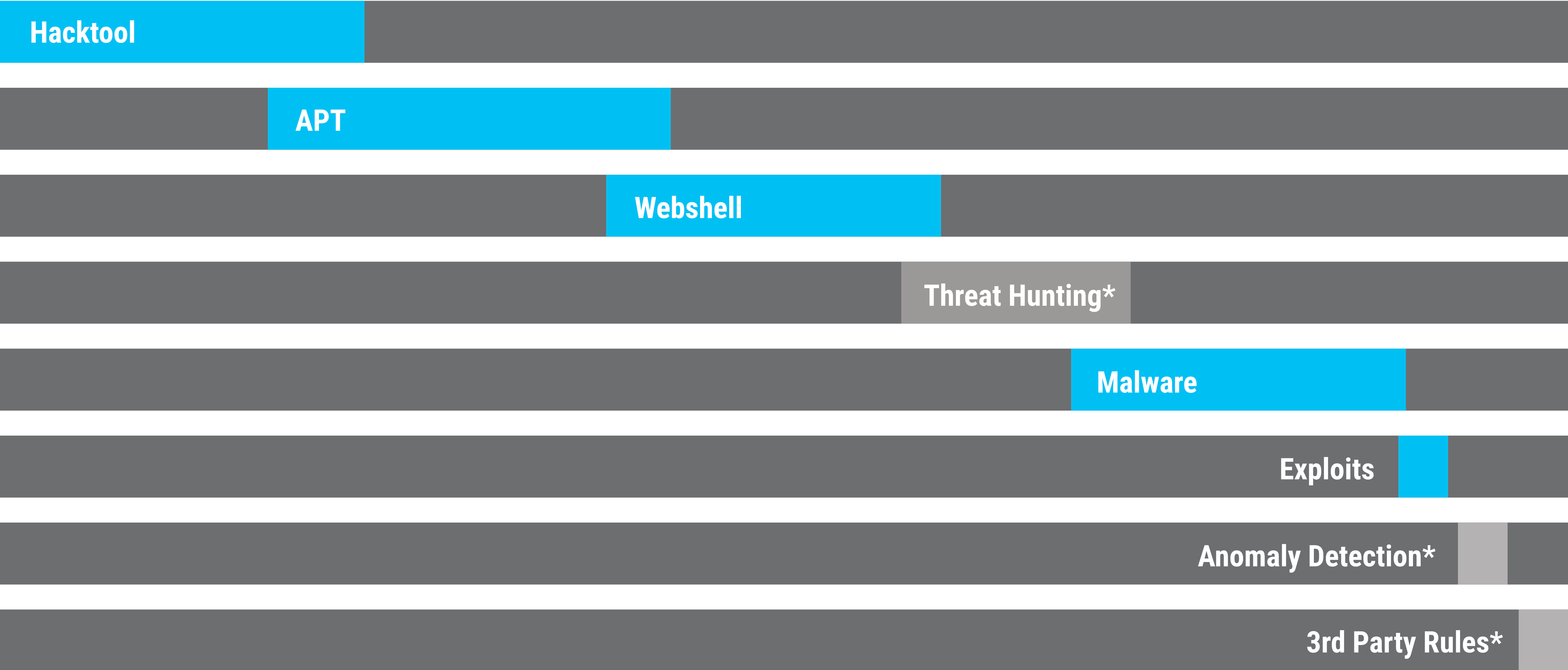
Subscribable Categories

Hacktools
This category contains all kinds of tools used for hacking purposes and often classified as “Potentially Unwanted Application (PUA)” like port scanners, password dumpers, privilege escalation, lateral movement or tunneling tools. It also contains rules for output or temporary files of the mentioned hacktools that adversaries sometimes forget to remove from the compromised systems.

APT
It contains all kinds of hacktools or malware related to threat actor activity. Rules with this tag often have references to certain threat actor reports. This category has many overlaps to the “Hacktool” and “Malware” categories.

Webshells
This category contains web shells written in PHP, JSP(X), ASP(X) that attackers drop on web servers to persist and pivot to other systems in the network. It also has many rules for obfuscated web shells.

Malware
This category contains all types of commodity malware, credential stealer, worms, ransomware, cryptocoin miner and all other types of common malware.

Exploits
This is the smallest category for rules that detect exploit codes, weaponized documents and tools to exploit local and remote exploits. The rules typically contain links to research and CVE numbers as references.
Categories Only Available in THOR Scanner

Threat Hunting
The threat hunting category contains the most extraordinary set of rules for anomaly, obfuscation and suspicious indicator detection. The rules are often highly generic and able to detect yet unknown threats. It contains rules for casing anomalies, many rules for differently encoded keywords, rare executable packers, PE header data anomalies and other obfuscation techniques.

Anomaly Detection
Anomaly detection rules are special rules that make use of external variables passed into the rule matching process by the scanner. We use anomaly detection rules to report modified system files, uncommon process characteristics and suspicious combinations (e.g. RARSFX file with Microsoft copyright)

3rd Party Rules
Rules provided by our threat intelligence and incident response partners cannot be provided in clear text form.
Categories – Quantity Comparison
* only in THOR scanner
