We are glad to announce significant performance improvements in the latest versions of THOR. We've refactored several processing units to bulk scan elements that have previously been checked each at a time. These changes affect the modules "Eventlog", "Registry",...
ASGARD v1.7.2 with File and Memory Collection
Our brand new ASGARD 1.7 comes with a shiny new feature: Evidence Collection The evidence collection feature allows you to collect files or main memory from connected end systems. The memory and file collection tasks provide a throttling option to reduce the upload...
Detect System File Manipulations with SysInternals Sysmon
SysInternals Sysmon is a powerful tool especially when it comes to anomaly detection. I recently developed a method to detect system file manipulations, which I would like to share with you. We know how to track processes with the standard Windows audit policy option...
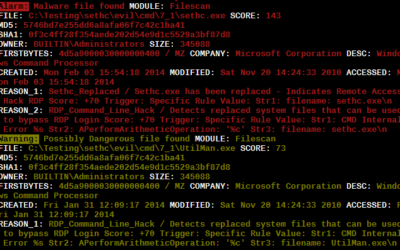
Inverse Yara Signature Matching (Part 1/2)
During our investigations we encountered situations in which attackers replaced valid system files with other system files to achieve persistence and establish a backdoor on the systems. The most frequently used method was the replacement of the "sethc.exe" with the...