We are glad to announce significant performance improvements in the latest versions of THOR.
We’ve refactored several processing units to bulk scan elements that have previously been checked each at a time. These changes affect the modules “Eventlog”, “Registry”, “RegistryHive” and “Logscan”.
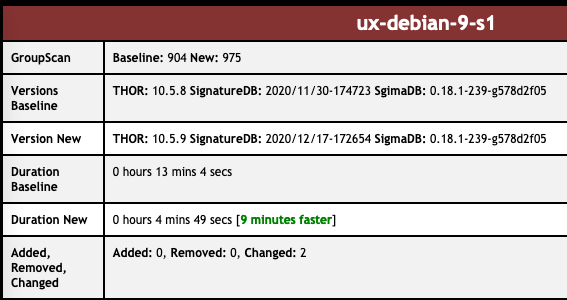
The performance improvements are impressive, especially on systems with big Windows event logs or log files on disk, but also on systems that contain a lot of registry hives like domain controllers or multi-user systems.
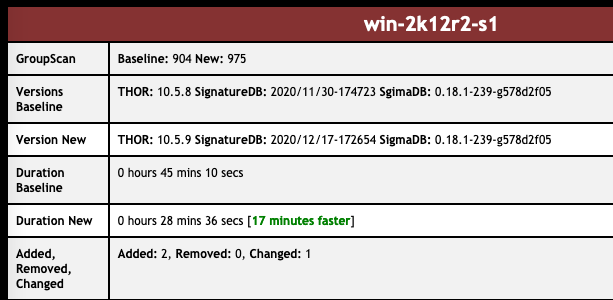
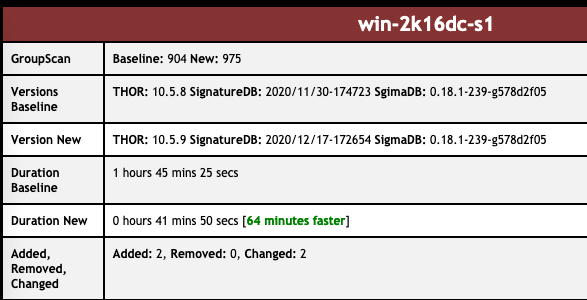
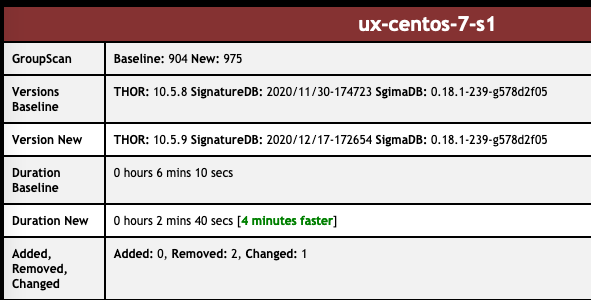
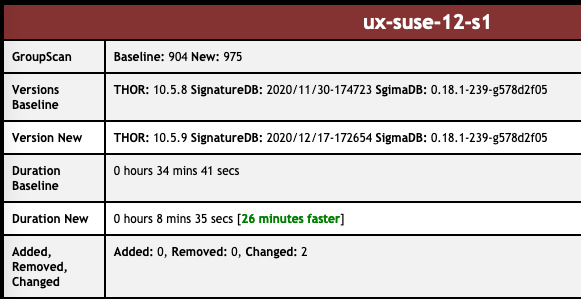
As these changes result in significant speed benefits, we’ve decided to exclude some elements from the “max-file-size” limit.
In the past, log files or registry hives bigger than “max-file-size” (default 12MB) have been skipped in normal scan modes. Only in intense (–intense) and lab scanning mode (–fsonly / –lab in TechPreview) these files have been included and analyzed with the respective modules.
THOR v10.5.9 and THOR v10.6.2 TechPreview now include these elements in their deeper analysis during file system scans. This could lead to longer scan times in some cases. We believe that overall scans turn out to be suprisingly faster and would be interested in feedback on the scan durations in your environments.










