Download the newest version of our Antivirus Event Analysis Cheat Sheet here. --- Update 09.09.18 10:30am CET Thanks to Markus Neis, I've updated version 1.4 and created a version 1.5 just a few hours after my tweet. You can download version 1.5 here.
SPARK uses Sigma Rules in Eventlog Scan
Sigma is a rule format for threat detection in log files. It is for log data what "Snort rules" are for network traffic or "YARA signatures" are for file data. It is easy to write and read. Writing a Sigma rule is a matter of minutes. On the right you can see a simple...
New Antivirus Event Analysis Cheat Sheet Version 1.2
Today we release a new version of our "Antivirus Event Analysis" Cheat Sheet that helps you with the analysis of Antivirus events by providing a clear decision matrix. We've updated many of the sections, added new VirusTotal online analysis checks and brought it in a...
The Best Possible Monitoring with Sigma Rules
Some of you may already have heard of Sigma, a generic approach for signatures used in SIEM systems. Its main purpose is to provide a structured form in which researchers or analysts can describe their once developed detection methods and make them shareable with...
Not All IOC Scanning Is the Same
In the recent months I had several talks with friends and coworkers about IOC scanning and how to integrate IOCs from threat intel feeds into our scanners or other products that our customers already use. People often tell me that EDR or client management product X...
How to Fall Victim to Advanced Persistent Threats
During the last four years, I was engaged on incident response teams for several large advanced persistent threat (APT) cases involving different German corporations. In this time, we have developed methods and tools to detect compromised systems, while also planning...
YARA Rules to Detect Uncommon System File Sizes
YARA is an awesome tool especially for incident responders and forensic investigators. In my scanners I use YARA for anomaly detection on files. I already created some articles on "Detecting System File Anomalies with YARA" which focus on the expected contents of...
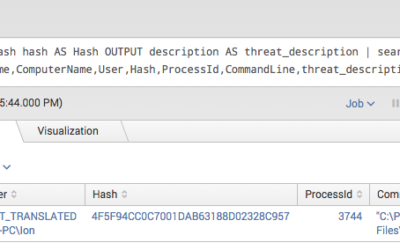
Splunk Threat Intel IOC Integration via Lookups
Today most security teams have access to a lot of different information sources. On the one hand they collect log data from different sources and try to correlate them in a useful way in so-called SIEM systems. On the other hand they receive threat information from...
Detect System File Manipulations with SysInternals Sysmon
SysInternals Sysmon is a powerful tool especially when it comes to anomaly detection. I recently developed a method to detect system file manipulations, which I would like to share with you. We know how to track processes with the standard Windows audit policy option...
Sysmon Example Config XML
Sysmon is a powerful monitoring tool for Windows systems. Is is not possible to unleash all its power without using the configuration XML, which allows you to include or exclude certain event types or events generated by a certain process. Use the configuration to...