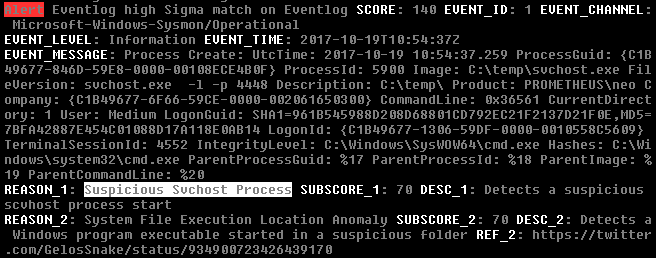
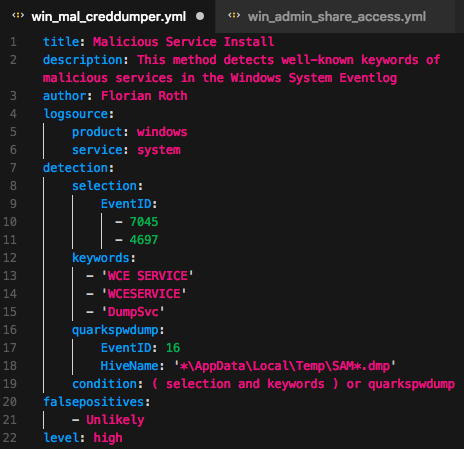
On the right you can see a simple Sigma rule that checks the “System” eventlog for traces of password dumper activity. The detection section contains 1+ identifiers (selection, keywords, quarkspwdump) that can be defined freely by the rule author. These selectors are used in the condition to build the rule.
It also contains a description, references, possible false positives and a level.
Wouldn’t it be great if you could apply Sigma rules on the endpoint?
This way you are able “query” the standalone systems that are not connected to your SIEM and uncover otherwise common blind spots in your environment.
We ship the current rule set, which is part of the public Sigma repository and contains more than 200 rules with our SPARK program package in an encrypted form. (*.yms)
You can add your own Sigma rules to the “./custom-signatures/sigma/” folder in the SPARK program directory.
To activate Sigma scanning, use the new “–sigma” parameter.
Currently only SPARK supports this feature and there are no plans to implement this in THOR as well.
The feature is currently free for all customers but may become a premium feature that has to be licensed separately by the end of the year depending on the customer’s plan.
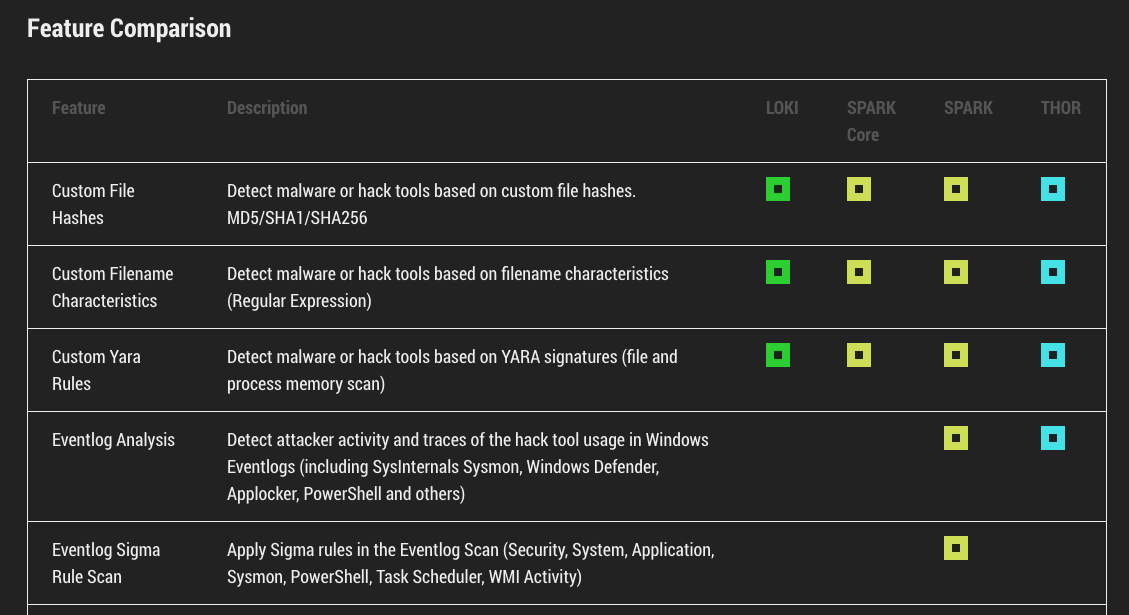
See the comparison table for a complete overview on all features.