Sysmon is a powerful monitoring tool for Windows systems. Is is not possible to unleash all its power without using the configuration XML, which allows you to include or exclude certain event types or events generated by a certain process. Use the configuration to exclude high volume sources or event types of less interest (e.g. Process Termination).
Installation:sysmon.exe -i config.xml
Set new configuration:sysmon.exe -c config.xml
Get help on the configuration and filtering options via “sysmon -h config”.
The following example may help you to understand the format and define your own rules.
<sysmon schemaversion="1.0"> <configuration> <!-- Capture MD5 Hashes --> <hashing>MD5</hashing> <!-- Enable network logging --> <network></network> </configuration> <rules> <!-- Log all drivers except if the signature --> <!-- contains Microsoft or Windows --> <driverload default="include"> <signature condition="contains">microsoft</signature> <signature condition="contains">windows</signature> </driverload> <!-- Do not log process termination --> <processterminate></processterminate> <!-- Exclude certain processes that cause high event volumes --> <processcreate default="include"> <img condition="contains" gt="" chrome="" exe="" lt="" processcreate="" --="" do="" not="" log="" file="" creation="" time="" stamps="" filecreatetime="" network="" connections="" of="" a="" certain="" process="" or="" port="" networkconnect="" default="include" img="" destinationport="" 123="" rules="" pre="" />
You can always use the task name and the event fields to define more filters. The rule tag can be found in the event viewer on the task name.
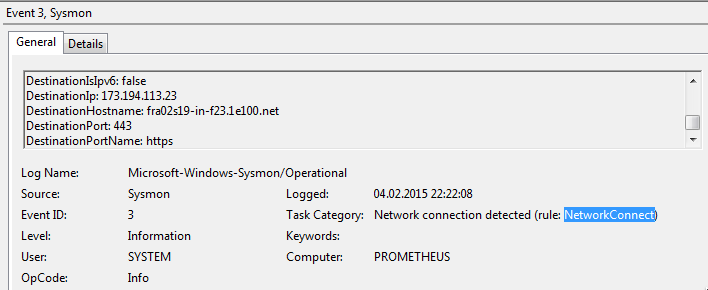
Sysmon Event Type
Use the event fields as tags to apply a certain filter.
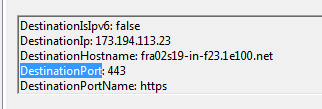
Sysmon Event Field
The available conditions for the field entries are as follows:
- is – Default, values are equals.
- is not – Values are different.
- contains – The field contains this value.
- excludes – The field does not contain this value.
- begin with – The field begins with this value.
- end with – The field ends with this value.
- less than – Lexicographical comparison is less than zero.
- more than – Lexicographical comparison is more than zero.
- image – Match an image path (full path or only image name). For example: lsass.exe will match c:\windows\system32\lsass.exe.










