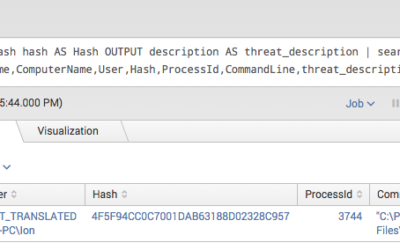
Today most security teams have access to a lot of different information sources. On the one hand they collect log data from different sources and try to correlate them in a useful way in so-called SIEM systems. On the other hand they receive threat information from...
Detect System File Manipulations with SysInternals Sysmon
SysInternals Sysmon is a powerful tool especially when it comes to anomaly detection. I recently developed a method to detect system file manipulations, which I would like to share with you. We know how to track processes with the standard Windows audit policy option...
APT Detection is About Metadata
People often ask me, why we changed the name of our scanner from "IOC" to "APT" scanner and if we did that only for marketing reasons. But don't worry, this blog post is just as little a sales pitch as it is an attempt to create a new product class. I'll show you why...
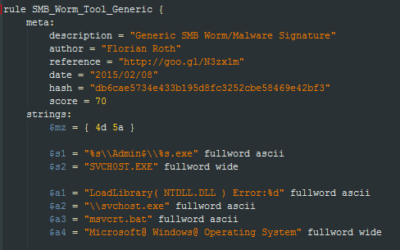
How to Write Simple but Sound Yara Rules
During the last 2 years I wrote approximately 2000 Yara rules based on samples found during our incident response investigations. A lot of security professionals noticed that Yara provides an easy and effective way to write custom rules based on strings or byte...
Incident Response Consulting
In den vergangenen Monaten konnten wir mehrere Kunden bei der Bewältigung und Behandlung massiver Angriffe unterstützen. Zufällige Entdeckungen im Kundennetz zeigten in allen Fällen nur die "Spitze es Eisbergs" größerer und länger andauernder Attacken. Nachdem ein...
Windows Client Security Audit
Das von uns entwickelte "Windows Client Security Audit" wurde auf Grund der neuen Erkenntnisse aus den Vorträgen der DEFCON 20 Konferenz im Juli erweitert. Konkret wurden Tests zur Prüfung der VPN-Konfigurationen und der NTML bzw. Kerberos Authentifizierung...