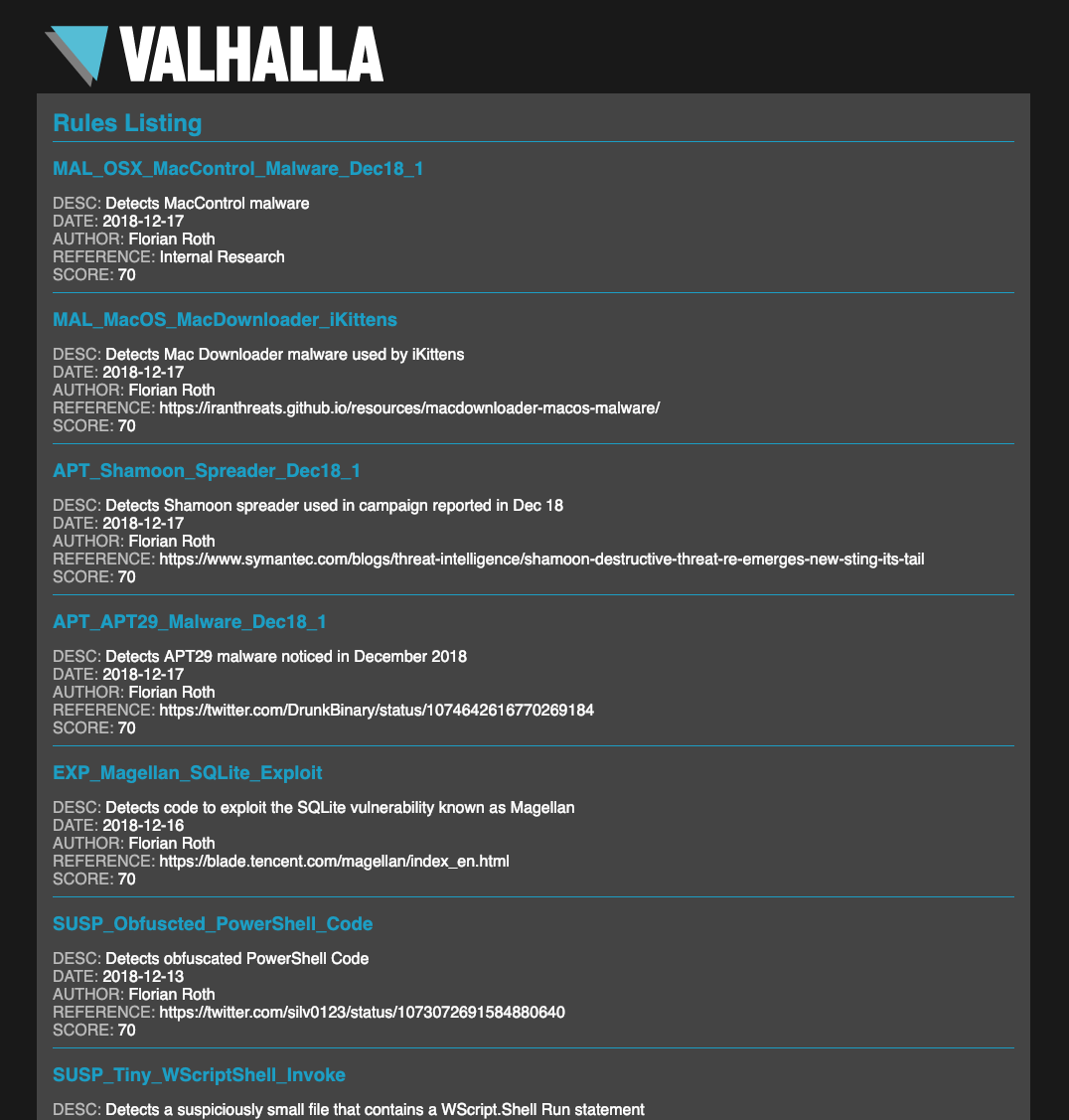
As previously announced our YARA rule packs and feeds will be available in March/April 2019. We’ve put a lot of effort into a internal system named “Mjolnir” that parses, normalizes, filters, tags and automatically modifies our rule base, which contains more than 9000 YARA rules.
This system will now fill a database of tagged YARA rules – the basis of our new YARA services.
The services will be divided into two categories:
- YARA Rule Set
- YARA Rule Feed
YARA Rule Set
The YARA rule set consist of more than 7000 YARA rules of different categories that are used in our scanners.
Some of our rules use extensions (external variables) that are only usable in our scanner products. These rules, experimental, third party and other classified rules will not be part of the purchasable rule set.
YARA Rule Feed
The YARA rule feed is a subscription on our rules. The feed always contains the rules of the last 90 days, which is between 250-400 YARA rules.
Rule Samples
The quality of the rules in the rule set are comparable to the rules in our public “signature-base” repository.
Some good examples for the different rule categories are:
- Webshell – FOPO Obfuscated Webshells
- Exploit – Exploit Codes for CVE-2017-8759
- Hacktool – BlackBone Driver Injector
- Suspicious – Suspicious Big Scheduled Task Files
- APT – Turla Rules
Quality and Focus
The rules are tested against a data set of more than 350 TB of goodware. The goodware file repository consists of Windows OS files, several full Linux distributions and a big collection of commercial and free software.
However, false positives are always possible. We do not recommend any destructive action on a signature match, like delete or blocking.
The main focus of our rules are:
- Threat Hunting
- Classification
- Anomaly Detection
- Compromise Assessment