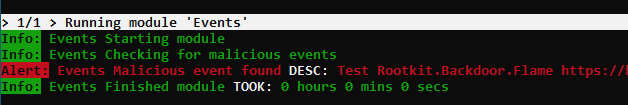
New Module “Events”
This module checks registered Events in the system environment as they are used by advanced malware and rootkits.
We have checked for malicious Events before, in the Rootkit module, but these checks were hardcoded. We’ve spun out that section and can now provide regular updates in a separate signature file.
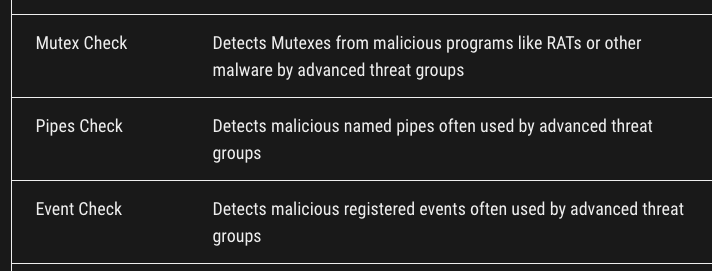
The “Events” module extends our set of rootkit related modules that already include the “Mutex” and “Named Pipe” modules.
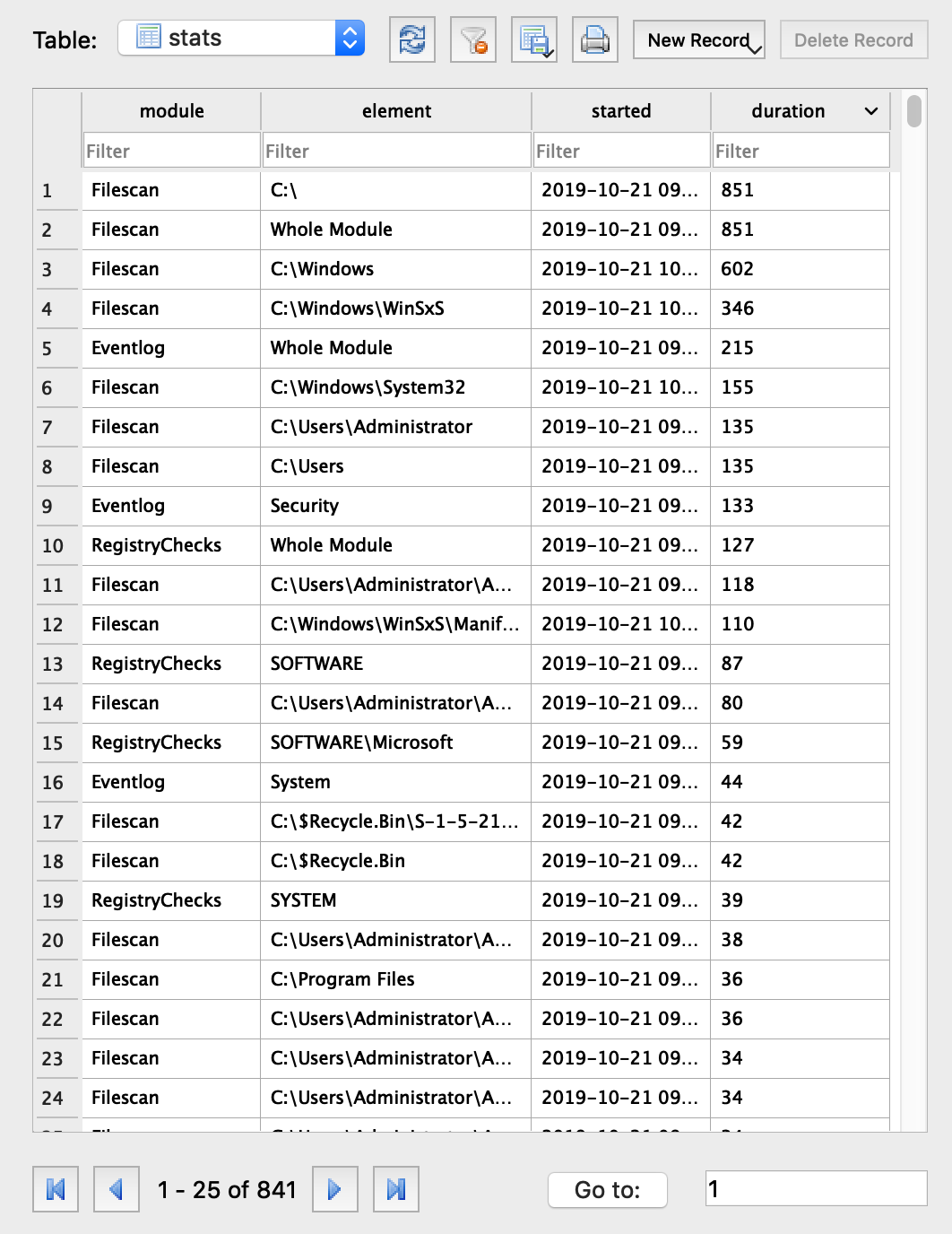
THOR DB with Timing Statistics
THOR v10.2 features an unencrypted table in THOR DB that shows timing information for the scanned elements. This could help you identifying elements that lengthen scans significantly and determine a time range in which certain elements have been scanned.
Reduced Output
A new switch “–reduced” allows to limit events to “Warning” and “Alert” types only.
Other Changes
- Upgrade to YARA 3.11
- Improved module messages (better description)
- Bugfix: Golden ticket detection module reported far too many Kerberos tickets with too long lifetime, message: “Kerberos ticket with very long life time detected – likely a Golden Ticket”. The issue has been fixed. Please make sure that you haven’t filtered / base-lined that event type.
- Added ExecFlag to SHIMCache output
- Apply YARA rules on WMI Event Filters
- Passing new external YARA variables ‘timezone’ and ‘language’ to registry rule set
- More robust custom YARA signature initialisation (syntax check and tests before compilation)










