Refactored Handle Detection
We have completely refactored THOR’s malicious Handle detection.
We now allow the use of regular expressions and combined all types in a single signature file named “malicious-handles.dat”.
Users can provide custom indicators by placing a file with the keyword ‘handles’ in name into the folder ./custom-signatures/iocs
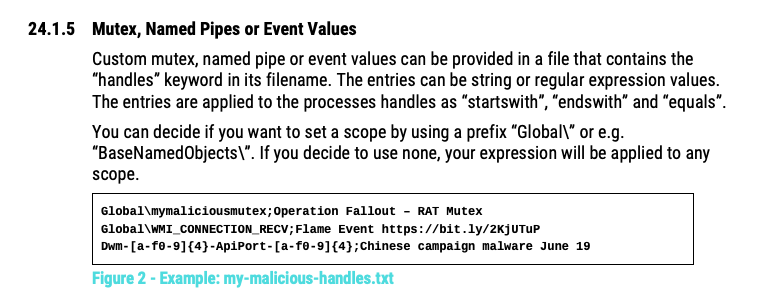
Process Handle Match Enrichment
Mutex, Named Pipe or Event matches will now trigger message enrichment in which the alert message is “enriched” with plenty of helpful information on the underlying process, including image file path, parent process and image file hashes.
This helps analysts to evaluate and classify the event.
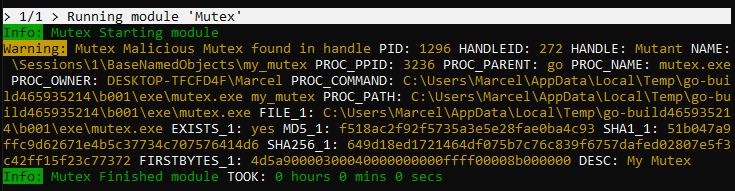
More Eventlog Sources
We’ve integrated more Windows logs in the default Eventlog scanning to detect keyword and filename IOCs in even more data sources.
This could increase scan duration significantly in cases in which you have defined custom unusually large maximum log sizes.
Custom Eventlog and Registry Exclusions
Users can now exclude certain Registry paths or Eventlogs from scanning.
We’ve added two new and empty exclude files in the ./config sub folder for your convenience.
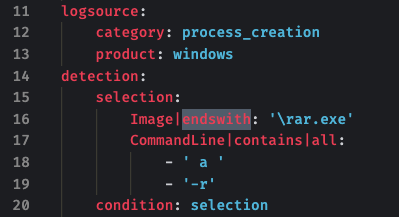
Support for new Sigma Modifiers
THOR now supports the newest value modifiers used in the most recent version of the Sigma standard.
- endswith
- startswith
Case ID (CID) get renamed
Previous versions of THOR offered a parameter -i / –case-id to set a unique identifier that appears as “CID: identifier” in all log lines of this specific scan.
With version 10.3 this CID gets renamed to SCANID and will be generated by default.
Every log line will contain a SCANID that makes it easier to associate a single line with the complete scan in reporting platforms like SIEM systems or ASGARD Analysis Cockpit.
You can still overwrite that value manually for legacy reasons or in order to group multiple scan runs into a single logical report.

Other Changes
- Feature: Log to local syslog with `–local-syslog` (Linux and macOS only)
- Improvement: Filename IOC “slash to backslash” transformation now works platform independent
- Improvement: SHIMCache Analysis in Registry Hives (not just live Registry)
- Improvement: Support for new license type “silent” (allows silent scans used in deployment tests)
- Improvement: YARA rule date in output messages
- Change: -j hostname will also adjust hostname in output file names
- Change: Don’t skip certain Registry paths with `–fullregistry` or in `–intense` mode
- Change: New value “max_file_size_intense” to be able to set a dedicated value for “intense” or “lab” scans
- Bugfix: missing start and end date in HTML report
- Bugfix: Message enrichment module processed duplicate values (e.g. Eventlog contained the filepath C:\w1.exe three times, the message enrichment included the additional attributes like EXISTS, MD5, SHA1, FIRSTBYTES three times, which is unnecessary)










