Following THOR’s approach of showing suspicious elements, it is not feasible to completely avoid false positives. Therefore we always try to provide as much information as possible for an analyst to assess such a suspicious element as quickly as possible.
Users liked the DeeDive feature in which a string match on a chunk of data does not only include the matching string but also the surrounding strings, which help enormously to evaluate the criticality of a matching YARA signature.
The TechPreview version of THOR 10.6 now introduces this extra information in many other modules.
The following example shows a false positive in which the string ‘ -p 0x53A4C60B’ matched on the process memory of the ‘svchost.exe’ process with the full command line as ‘svchost.exe -k ClipboardSvcGroup -p’.
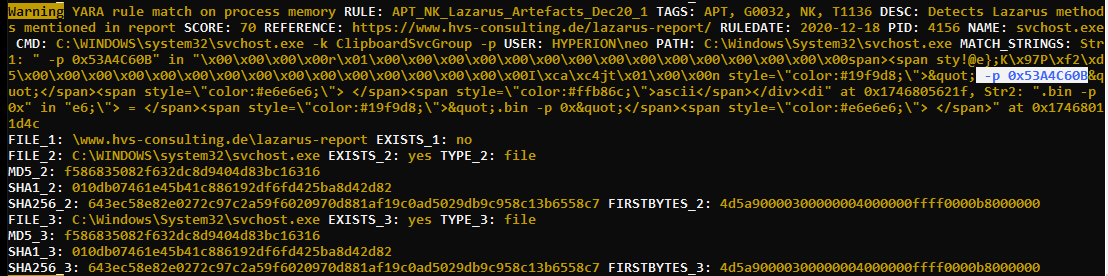
In previous versions THOR you would only see the matching string, but the new versions will also show the 40 bytes before and after the string match. (in the example it has been set to 100 bytes by using `–string-context 100`)
This helps analysts to assess the match more easily without having a process memory dump. In the example above, analyst can review that data block in which the string match occurred and see that it has been within HTML text that has been copied to memory. It could be an analyst system on which someone handling forensic reports copied sections from one document to another, but it’s certainly not the threat, which the YARA rule tried to detect.
This feature will be available in the upcoming THOR TechPreview 10.6.4.










