THOR TechPreview version 10.6.8 will introduce a completely new module named ETW Watcher, which runs in a separate thread and monitors the systems during a scan run. As its name indicates, the ETW Watcher module makes use of Event Tracing for Windows (ETW).
So, whenever you start a scan run on an end system, one thread performs all the usual checks while another thread analyses certain event channels and correlates events to detect malicious activity.
Consider it an agent-less, portable, short term EDR.
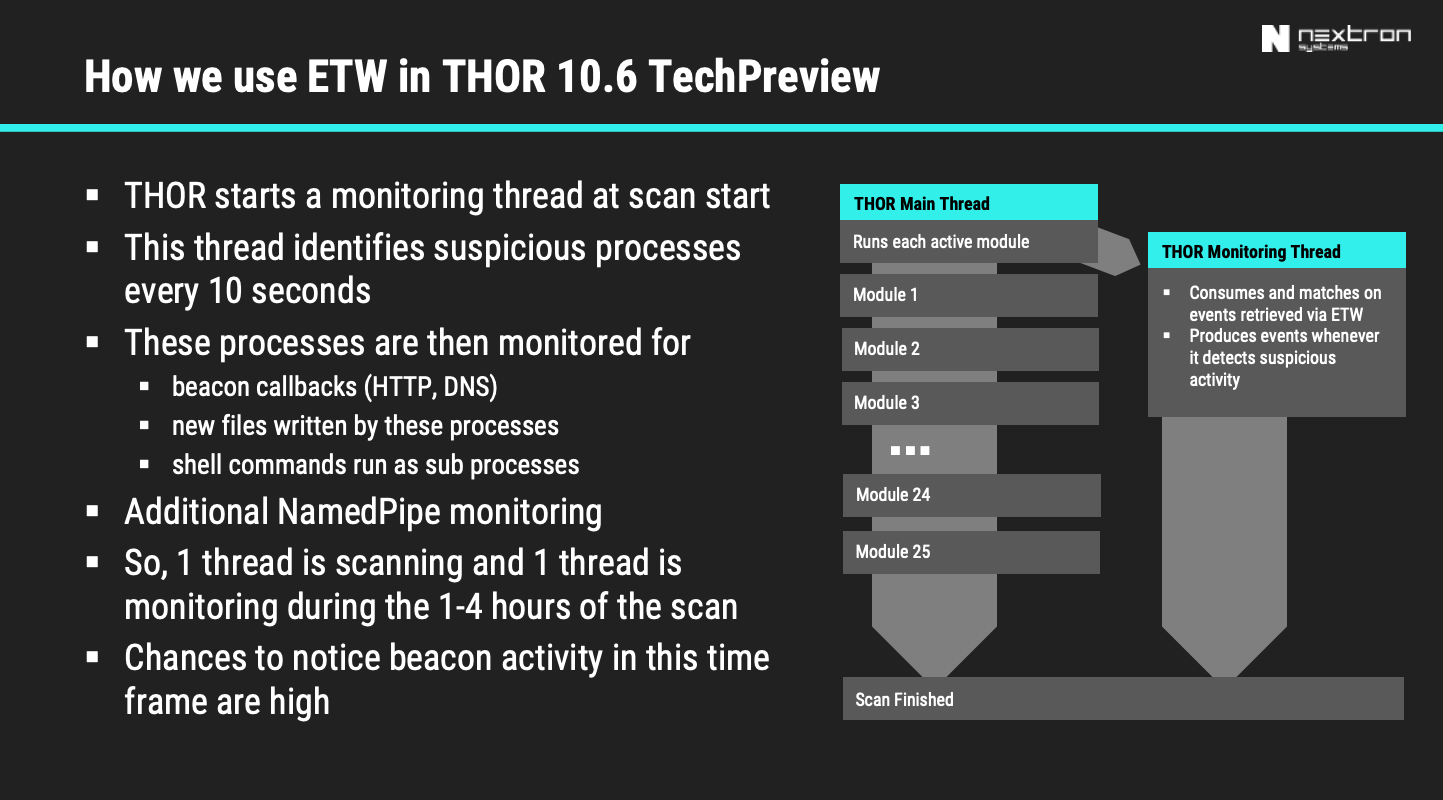
The first task of this new module is the detection of C2 beaconing activity as e.g. used in attacks that utilize Cobalt Strike.
The following screenshots show messages created by the ETW Watcher module. Since all of our modules apply a so called message enrichment, you’ll also notice further messages before and after the highlighted events. These additional messages are generated during the enrichment of the original event.
“Enrichment” means that we add additional information to the original event – e.g. if a file path is given in the original message, THOR tries to find that file, scans it using the “FileScan” module and adds information to the original event. The same is true for process ID values. This adds as much meta data as possible and helps analysts to assess the event as quickly and easily as possible.
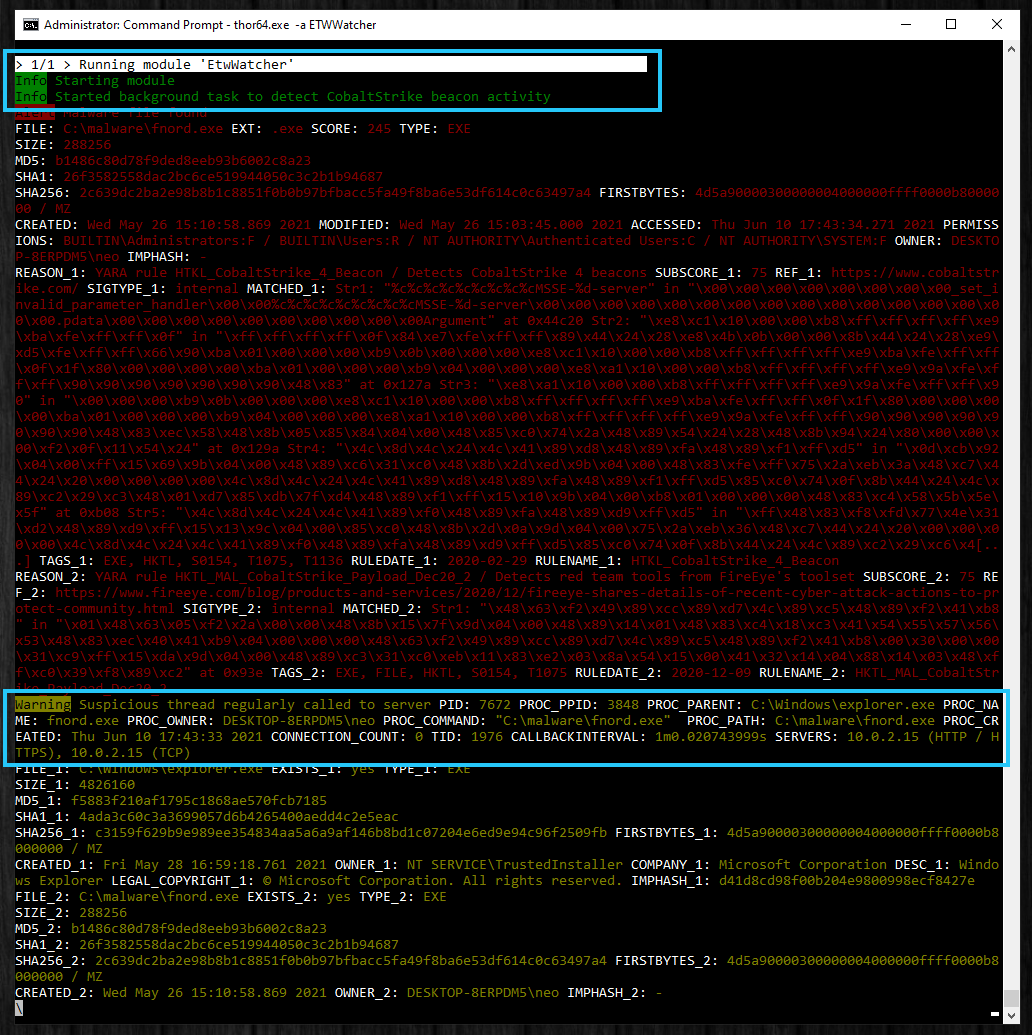
The example above shows a beacon detection that mentions a process named “fnord.exe” frequently calling out to 10.0.2.15 via HTTP and TCP. Message enrichment shows the result of a file scan above (red alert message; appears before the actual event because the enrichment happens before the message composition).
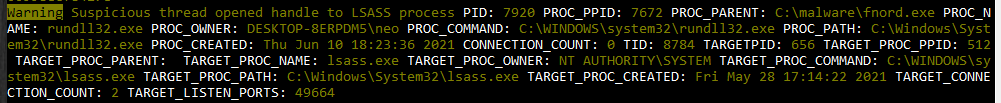
The next example shows the result of a “hashdump” command sent to the beacon. It causes the beacon to open a handle to the LSASS process memory, which THOR detects and reports as a Warning level message.
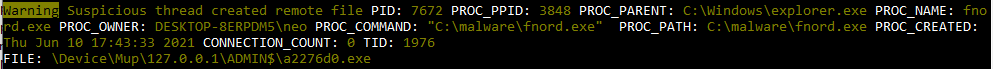
The next example shows a privilege escalation attempt performed by that same beacon.
The ETW Watcher module will be integrated in THOR TechPreview version 10.6.8 and only is available on Windows. It will not be available in THOR Lite and THOR 10.5.










