The first part of this blog series covers how THOR can be used to scan a Docker image. In the second part of this series, we will talk about how you can use THOR to scan running Docker containers. Now, consider this new use case: You want to check if your running Docker container was attacked by some Log4Shell exploit. To do this, we will show you how you can start THOR inside a running container!
Prerequisites
- Running Docker container with a shell installed (e.g. sh, bash, …)
- In this example we will use Alpine Linux
- THOR 🙂
- In this example we will use Thor-Lite. However, for a real-world usecase you should consider using the full Thor version (Thor vs Thor-lite).
Running THOR in a Docker container
First, we have to find the Docker ID of the container we want to check using: docker ps.
This will list all Docker containers running on the current host.
Sidenote: The following should also work with all the other containerization platforms (e.g. podman, Kubernetes, OpenShift, etc.).
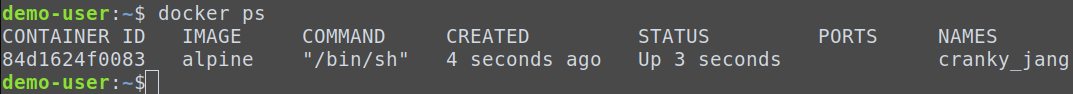
84d1624f0083. Now we copy the THOR files to the container:
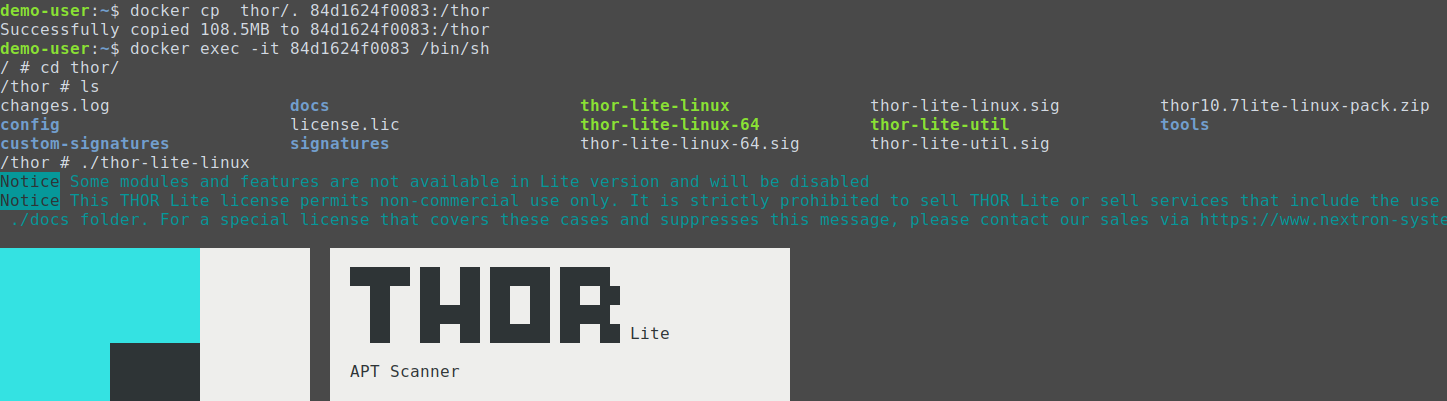
docker cp thor/. 84d1624f0083:/thor
docker exec -it 84d1624f0083 /bin/sh
Inside the Docker container you can cd thor and start THOR: ./thor-lite-linux.
{docker-id}_files_md5s.csv{docker-id}_thor_{date}.html{docker-id}_thor_{date}.txt
These files contain all findings of the THOR scan.
docker cp 84d1624f0083:/thor/dffcea1e1fe9_files_md5s.csv .docker cp 84d1624f0083:/thor/dffcea1e1fe9_thor_2023-04-26_0728.html .docker cp 84d1624f0083:/thor/dffcea1e1fe9_thor_2023-04-26_0728.txt .
Note: You have to replace 84d1624f0083 with our Docker ID.
Lastly, to clean up your container run the following: docker exec -it 84d1624f0083 rm -rf thor.
This will delete all files that were created in the earlier steps.










