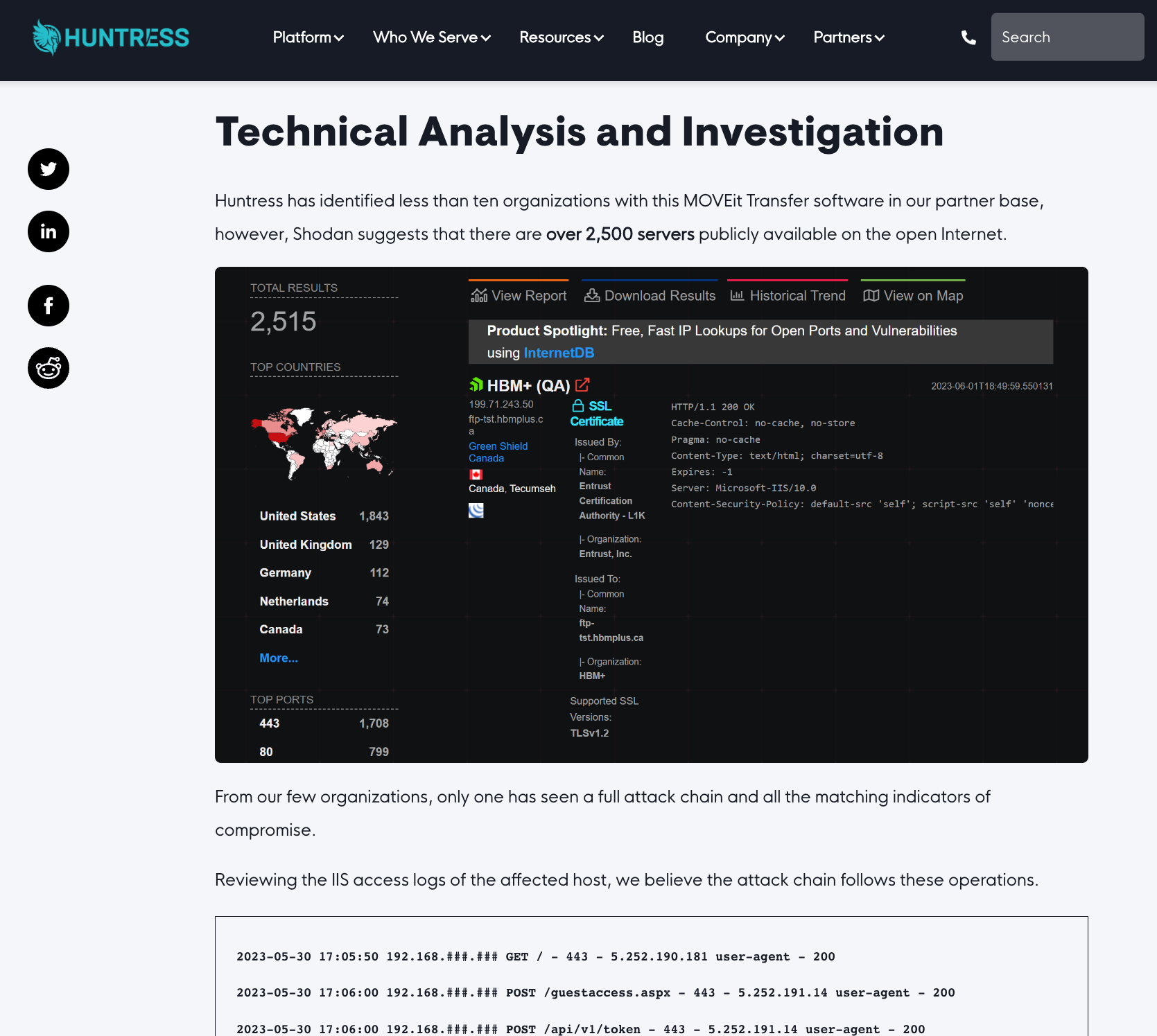
On June 1st, the vendor of MOVEit Transfer, previously known as Ipswitch but now called Progress, announced the discovery of a critical security vulnerability that has been exploited. MOVEit is an enterprise software utilized by numerous organizations globally for secure managed file transfer. According to Shodan, an internet search engine, there are currently over 2,500 servers publicly accessible on the open Internet running MOVEit.
You can find more information on the threat in the vendor’s advisory and the following articles by TrustedSec, Huntress Labs and Mandiant:
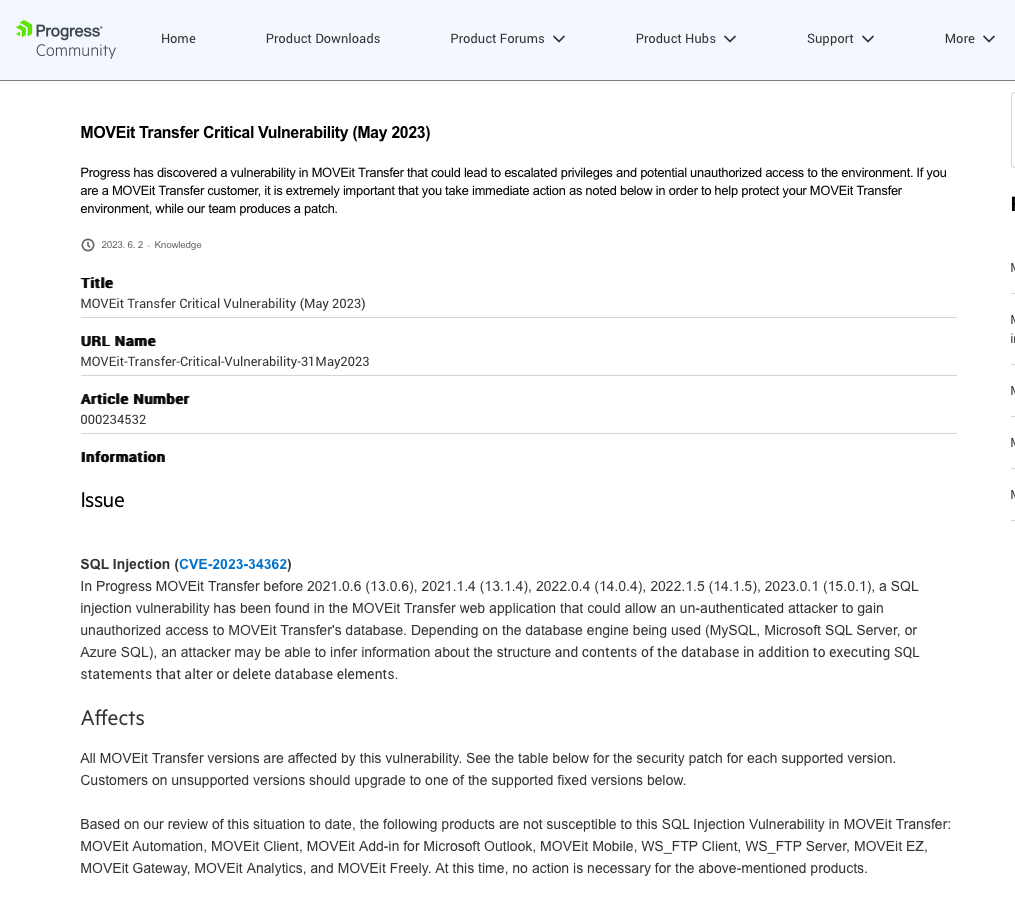
Vendor Advisory
The advisory by the vendor Progress was published on 01.06. and gets constantly updated
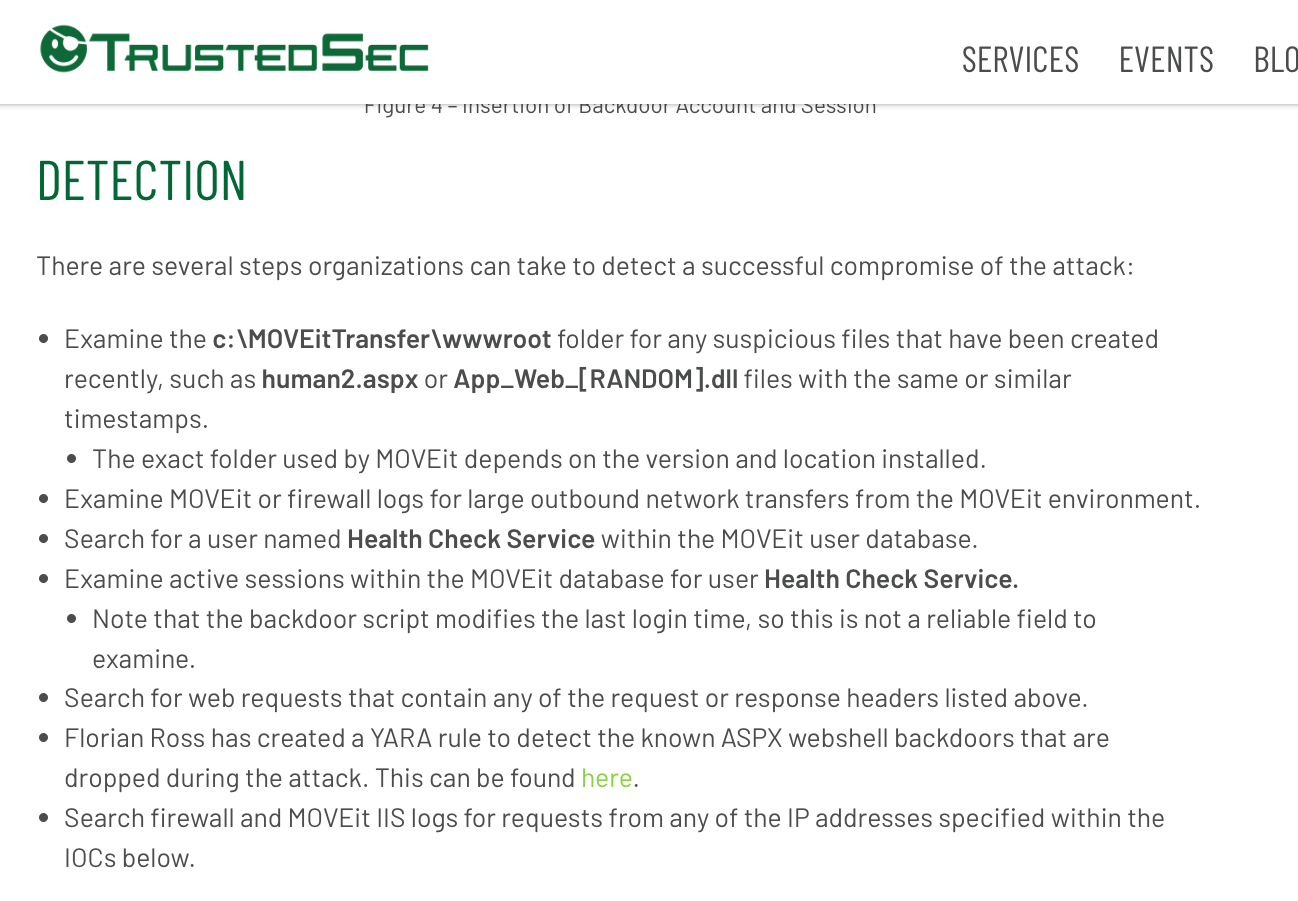
TrustedSec Article
This article by TrustedSec lists a lot of indicators and contains information on the dropped web shell
Huntress Labs Article
Huntress Labs reports on the activity including log file entries, IOCs and a YARA rule
Mandiant Report
Mandiant’s report attributes the activity to UNC4857
Upon initial awareness of the compromise, we initiated our own investigation and promptly released a series of detection rules to our public repositories. These Indicators of Compromise (IOCs) and YARA rules were immediately accessible to users of THOR Lite.
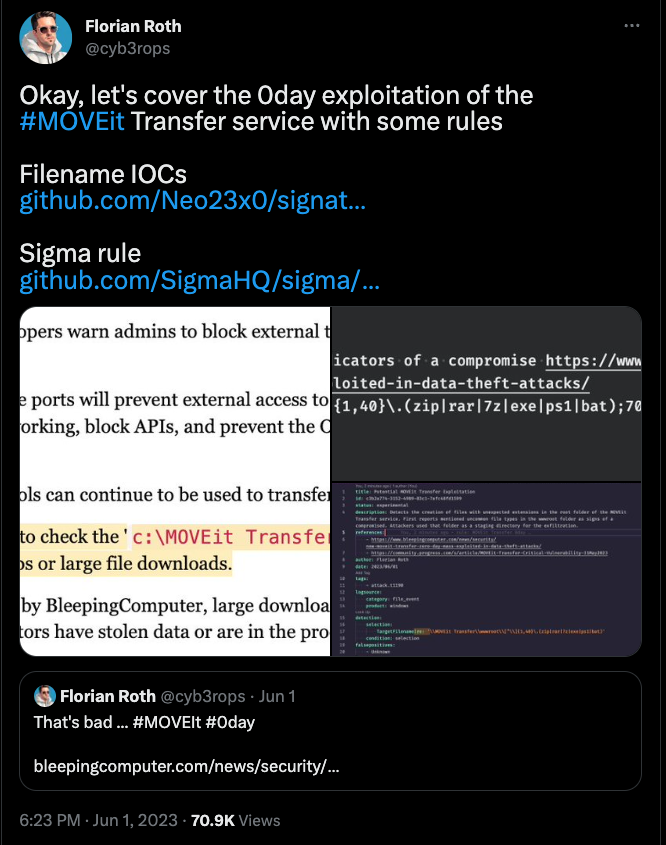
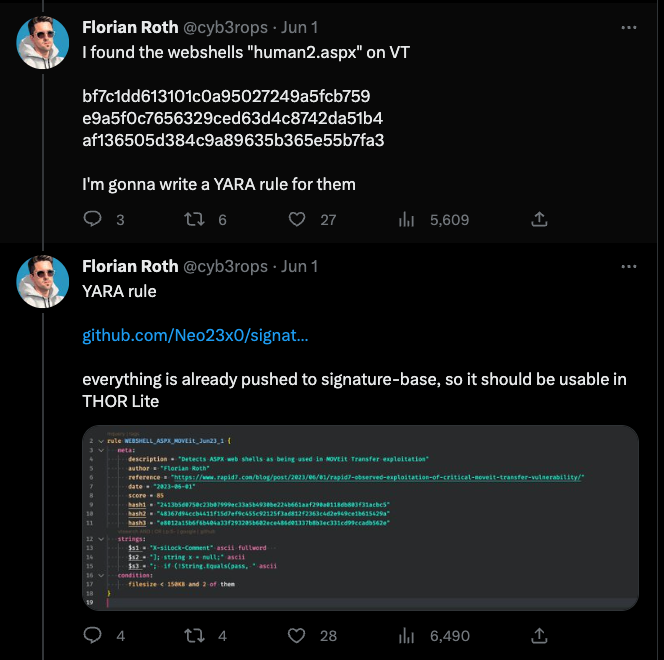
While having detection mechanisms in place is a positive step, assessing the situation and ensuring that no system in the network has been impacted by the threat is often a challenging task.
To facilitate this process and perform a rapid scan of your own environment at no cost, one option is to utilize the THOR Lite scanner. By employing this tool, you can leverage the rules mentioned earlier and swiftly evaluate your network for potential threats.
Enter THOR Lite
THOR Lite is the streamlined version of our compromise assessment scanner, THOR. It utilizes YARA rules and Indicators of Compromise (IOCs), such as hash values and file names, to effectively identify malicious activity.
In this technical blog article, we will delve into the utilization of THOR Lite for scanning end systems to detect any signs of malicious activity associated with the MOVEit exploitation.
Furthermore, we will explore the diverse range of indicators that THOR Lite can detect, guide you through the process of tool setup and configuration, and offer tips for comprehending the scan results.
By the end of this article, you will have a comprehensive understanding of how to utilize THOR Lite to conduct compromise assessments within your network.
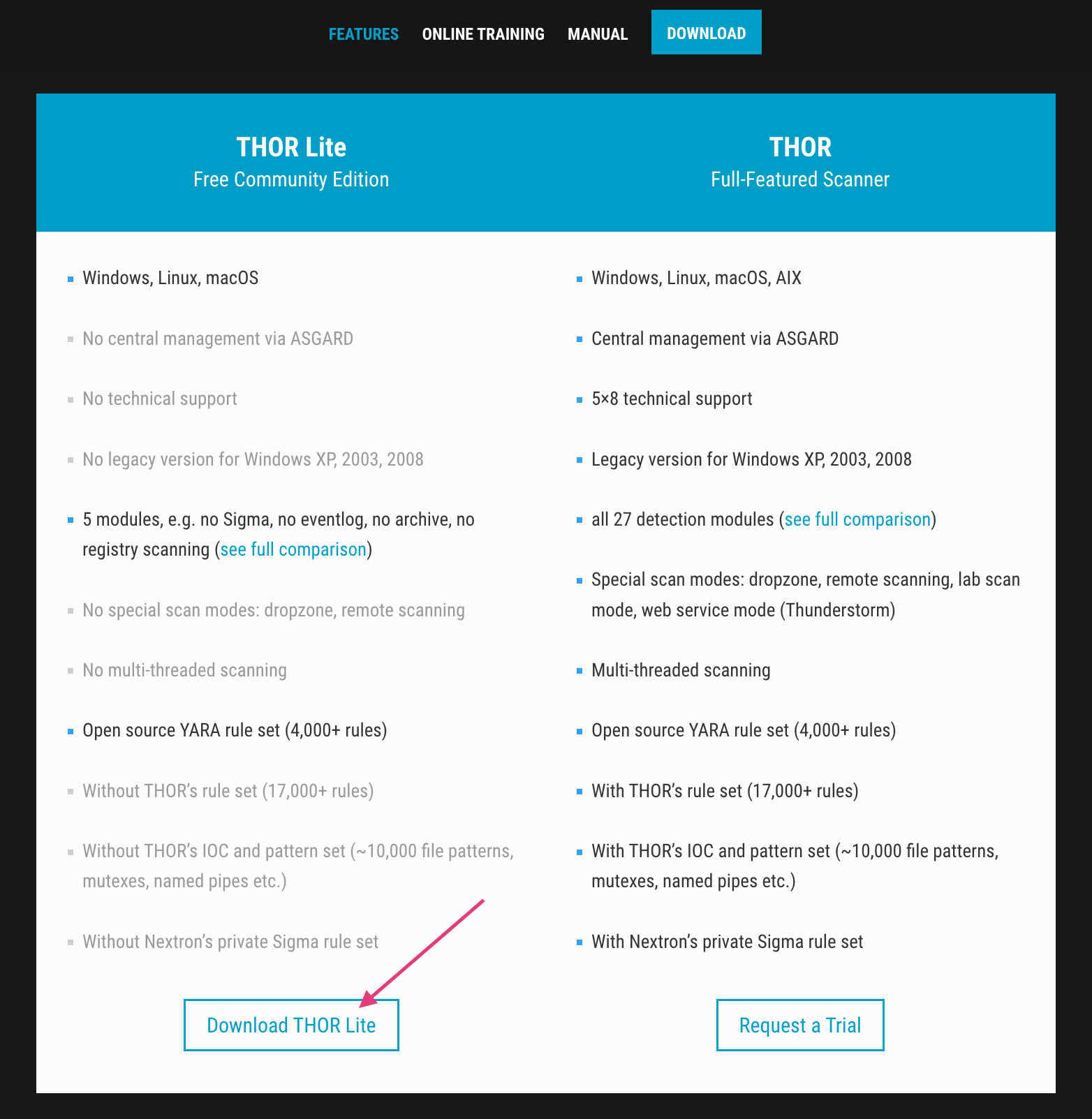
Download THOR Lite
Visit the product page, subscribe to the newsletter to get the program package and a license file.
Email content:

Getting Started
Once you have downloaded the program package in the form of a ZIP archive, extract its contents and locate the license file (.lic). Move the license file to the program folder.
To initiate the program, simply double-click on the “thor64-lite.exe” file without any additional flags. Alternatively, you can open a Windows command line with administrator privileges and navigate to the directory where you extracted the program package.
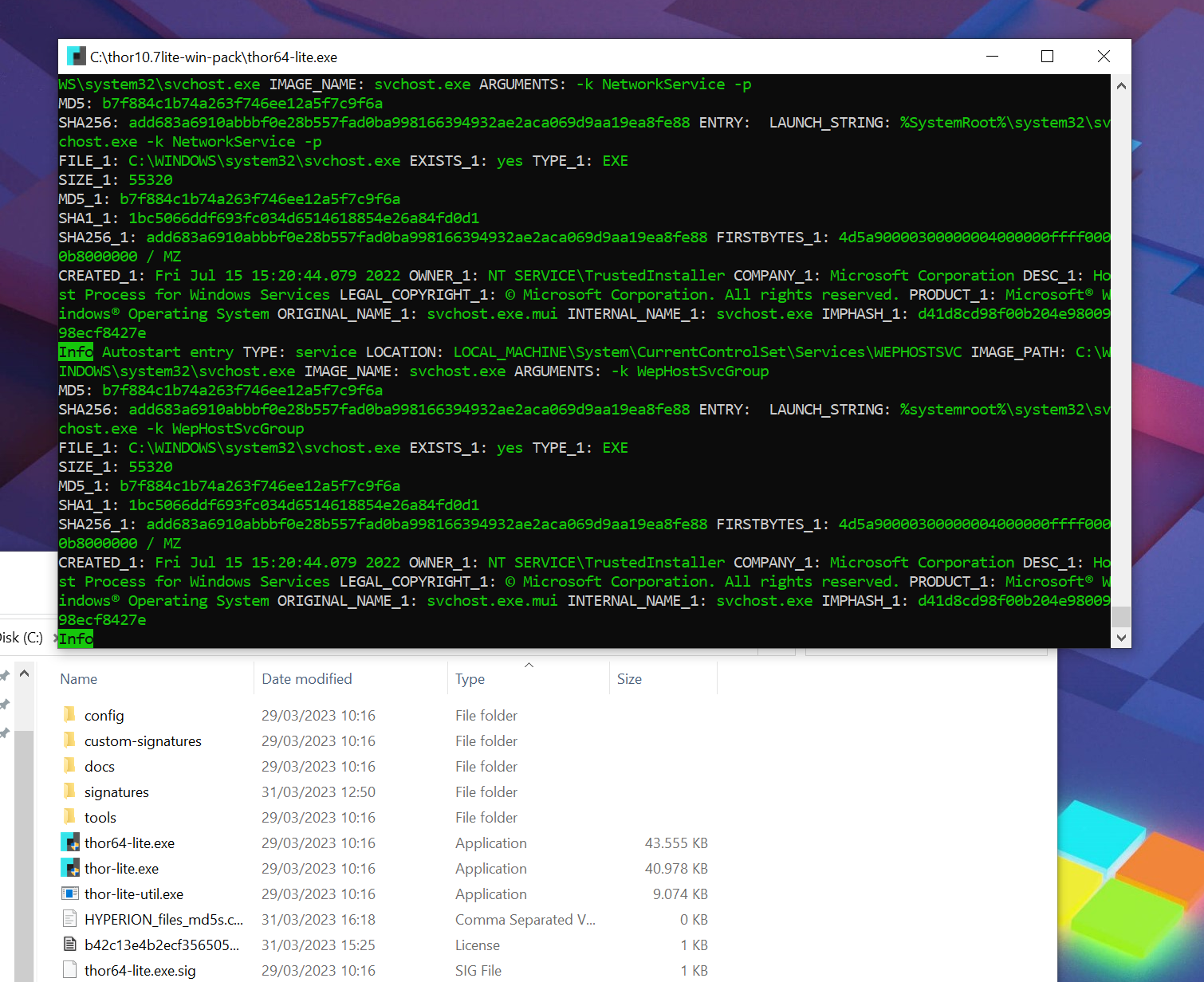
Upon running the program, a scan window will appear, automatically closing upon completion of the scan. Typically, scans require approximately 1-4 hours to complete, although there are techniques to expedite the scanning process.
Flags to Consider
--nosoft --nolowprio
If you are scanning virtual machines or systems that experience constant high load from other processes, it can be beneficial to utilize the “–nosoft” and “–nolowprio” flags. These flags allow THOR to run with the same process priority as any regular process, helping to ensure that the scan operates smoothly alongside other ongoing processes.
--lookback 150 --global-lookback
If you are interested in scanning recently created files and log entries, these flags direct THOR to exclusively scan elements that have been created or modified within the past 150 days. Any file or event log entry older than that timeframe will be ignored, resulting in a significantly smaller set of elements being scanned.
--cpulimit 30
To minimize the impact on end users working on a system during the scanning process, you have the option to reduce the CPU usage of the scanner to, for example, 30%. By doing so, you can prevent them from noticing the scan by decreasing the overall system load and fan noise.
Recommended CommandLine Flags for this Use Case
If a regular scan takes an excessive amount of time, we recommend utilizing the following command line flags to expedite the scan process by limiting it to the changes that have occurred within the last 150 days:
thor64-lite.exe --nolowprio --lookback 150 --global-lookback
To minimize CPU usage and make it as inconspicuous as possible for end users working on the scanned systems, employ the following command:
thor64-lite.exe --lookback 150 --global-lookback --cpulimit 35
Update the Signatures
To ensure that THOR always operates with the latest set of signatures related to the MOVEit exploitation, we are continuously working on enhancing and updating them. To incorporate the newest signatures, utilize the following command:
thor-lite-util.exe upgrade
Interpreting the Scan Results
During the scan you’ll see several messages in green and blue colours. Warning and alert messages use a yellow or red color. But don’t worry when you notice a message of that color. Remember that THOR is a scanner that highlights malicious and suspicious elements for review by an administrator or forensic analyst. Not everything shown as a “warning” message has to be a real threat.
After the scan finishes, users can find an HTML report in the program folder that lists all findings.
We recommend searching the HTML report for the “MOVEit” keyword and only review matches with the specific IOCs and YARA rules related to this activity.
THOR Lite is able to detect various forensic artefacts:
- The dropped ASPX web shell
- The compiled ASPX web shell in caches (even if attackers removed the .aspx file)
- Exploitation in the web server log files
- Access to webshell in web server log files
- Suspicious file types or extensions in the reported staging directories
Signatures
The subsequent listings display all the publicly available signatures that we have created and implemented in THOR Lite to identify malicious activity.
YARA (public)
WEBSHELL_ASPX_MOVEit_Jun23_1
WEBSHELL_ASPX_DLL_MOVEit_Jun23_1
LOG_EXPL_MOVEit_Exploitation_Indicator_Jun23_1
LOG_EXPL_MOVEit_Exploitation_Indicator_Jun23_2
SIGMA (public)
Emerging Threat Folder: CVE-2023-34362-MOVEit-Transfer-Exploit
Rule Title: Potential MOVEit Transfer CVE-2023-34362 Exploitation
UUID: c3b2a774-3152-4989-83c1-7afc48fd1599
Rule Title: MOVEit CVE-2023-34362 Exploitation Attempt – Potential Web Shell Request
UUID: 435e41f2-48eb-4c95-8a2b-ed24b50ec30b
IOCs
Filename IOCs
filename-iocs.txt @ signature-base
Hash IOCs
hash-iocs.txt @ signature-base
C2 IOCs
c2-iocs.txt @ signature-base
Full THOR Version
Please bear in mind that THOR Lite is solely a demo version of our complete scanner, which encompasses over 27 detection modules and more than 20,000 YARA rules. In contrast, THOR Lite employs only 5 modules and 2,500 rules.
For a comprehensive comparison of features, you can refer to the full feature comparison available here. Additionally, there is a detailed blog post that delves into the dissimilarities between the two versions, which you can find here.