THOR v10.1 features a mode of operation that is especially helpful in incident response or compromise assessment scenarios - remote scanning. Imagine that you're in a firefighting scenario - a breach has been confirmed and management wants to have quick results on...
Write YARA Rules to Detect Embedded EXE Files in OLE Objects
This is the first blog post published on our new website. If you followed my blog on www.bsk-consulting.de you should consider subscribing to the RSS feed of this blog or the "Nextron Systems Newsletter". This is one of the YARA related blog posts showcasing a special...
YARA Rules to Detect Uncommon System File Sizes
YARA is an awesome tool especially for incident responders and forensic investigators. In my scanners I use YARA for anomaly detection on files. I already created some articles on "Detecting System File Anomalies with YARA" which focus on the expected contents of...
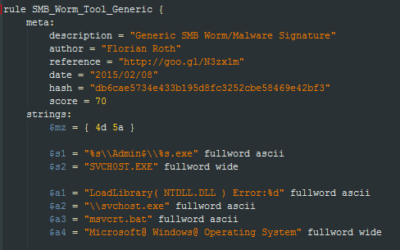
How to Write Simple but Sound Yara Rules
During the last 2 years I wrote approximately 2000 Yara rules based on samples found during our incident response investigations. A lot of security professionals noticed that Yara provides an easy and effective way to write custom rules based on strings or byte...