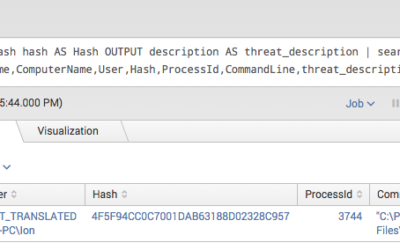
Today most security teams have access to a lot of different information sources. On the one hand they collect log data from different sources and try to correlate them in a useful way in so-called SIEM systems. On the other hand they receive threat information from...
Smart DLL execution for Malware Analysis in Sandbox Systems
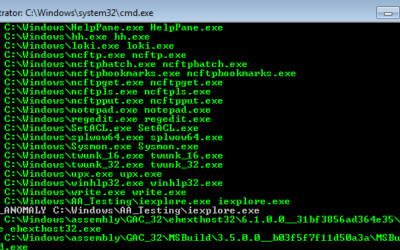
While analysing several suspicious DLL files I noticed that some of these files (which were obviously malicious) didn't perform their malicious activity unless a certain function was triggered. The malware used a registry entry to execute a certain function that is...
How to Scan for System File Manipulations with Yara (Part 2/2)
As a follow up on my first article about inverse matching yara rules I would like to add a tutorial on how to scan for system file manipulations using Yara and Powershell. The idea of inverse matching is that we do not scan for something malicious that we already know...
Howto detect Ebury SSH Backdoor
Die folgende Yara Signatur kann für die Erkennung der Ebury SSH Backdoor verwendet werden. rule Ebury_SSHD_Malware_Linux { meta: description = "Ebury Malware" author = "Florian Roth" hash = "4a332ea231df95ba813a5914660979a2" strings: $s0 = "keyctl_set_reqkey_keyring"...
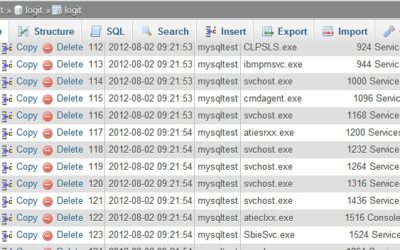
Logit – Windows Log Tool für Eventlog und MySQL
Die neue Version 0.3 des Kommandozeilenwerkzeugs zur Protokollierung von Programmausgaben in Dateien und das Windows Eventlog namens Logit unterstützt jetzt auch die Protokollierung in MySQL Datenbanken. Logit erwartet einen Ausgabestrom oder führt selbst ein Programm...
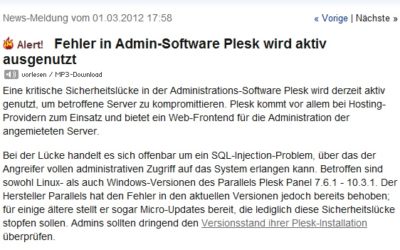
Plesk 0-day Workaround
Ein kürzlich bekannt gewordener 0-day Exploit für Plesk bedroht zahlreiche Server-Installationen. Betroffen sind vorasussichtlich alle Versionen vor Plesk 11. Die Lücke soll bereits genutzt worden sein, um tausende Installationen zu unterwandern. Über das ausgenutzte...
SIDMaster Windows SID to Username Tool
Das Werkzeug "SIDMaster" ermöglicht, einen Windows Benutzernamen in eine SID (Windows Security Identifier) aufzulösen. Das Programm ist einige Kilobyte groß und benötigt keine Installation. Es erfordert ein installiertes .NET 3.5 oder 4.0 auf dem System, auf dem es...
Neue Version 0.5 unseres Windows Syslog Client "NeoLogger"
Die neue Version 0.5 von NeoLogger überwacht jetzt auch ein Verzeichnis (-dir) und Unterverzeichnisse (-sub) auf Änderungen an Dateien mit Endung “.log” (-ff) und sendet alle neuen Zeilen (-tail) mit dem Dateinamen der geänderten Datei als Prefix (-fn) an den...
Plesk Sicherheitsproblem mit Microupdates lösen
Ein Sicherheitsproblem im Server-Management-Werkzeug Plesk bedroht viele über dieses System gemanagte Serversysteme. In einem heute veröffentlichten heise-Alert wird das Problem beschrieben und auch auf die Workarounds für ältere Systeme verlinkt. Die Lücke wird nach...