In order to automate the process of A) analyzing the exported functions and B) run the various DLL functions I created a script called “DLLRunner”. What it does is rather simple:
- First, it uses the Python module pefile to analyze the PE and retrieve a list of all exported functions with name and ordinal.
- Second, it executes the various exported functions by name or ordinal
- Third, it passes a set of parameters to the function in order to satisfy requirements and trigger any activity (simple “fuzzing”)
This is what it does:
rundll32.exe path/to/file.dll,exportedfunc1 rundll32.exe path/to/file.dll,exportedfunc2 rundll32.exe path/to/file.dll,exportedfunc3
The simple fuzzing mode looks like this:
rundll32.exe path/to/file.dll,exportedfunc1 "0" rundll32.exe path/to/file.dll,exportedfunc1 "1" rundll32.exe path/to/file.dll,exportedfunc1 "http://evil.local" rundll32.exe path/to/file.dll,exportedfunc1 "Install" ...
Examples
I tested the script on “url.dll” which is typically located in the system32 folder.
python dllrunner.py -f C:\Testing\url.dll --debug
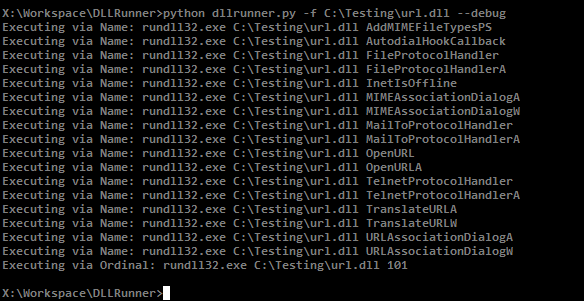
DLLRunner executing all exported functions
It caused a function called “TelnetProtocolHandler” and “TelnetProtocolHandlerA” to pop a telnet shell.
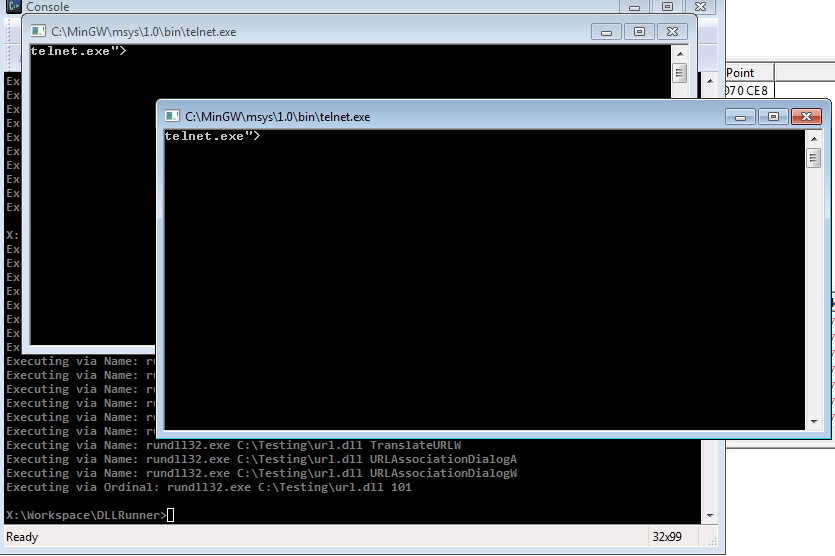
DLLRunner popping telnet windows via exported function “TelnetProtocolHandler”
If you pass “–fuzz” DLLRunner will pass several params to the functions. This caused a function in “url.dll” to pop browser windows with a fuzz parameter “http://evil.local”.
python dllrunner.py -f C:\Testing\url.dll --debug --fuzz
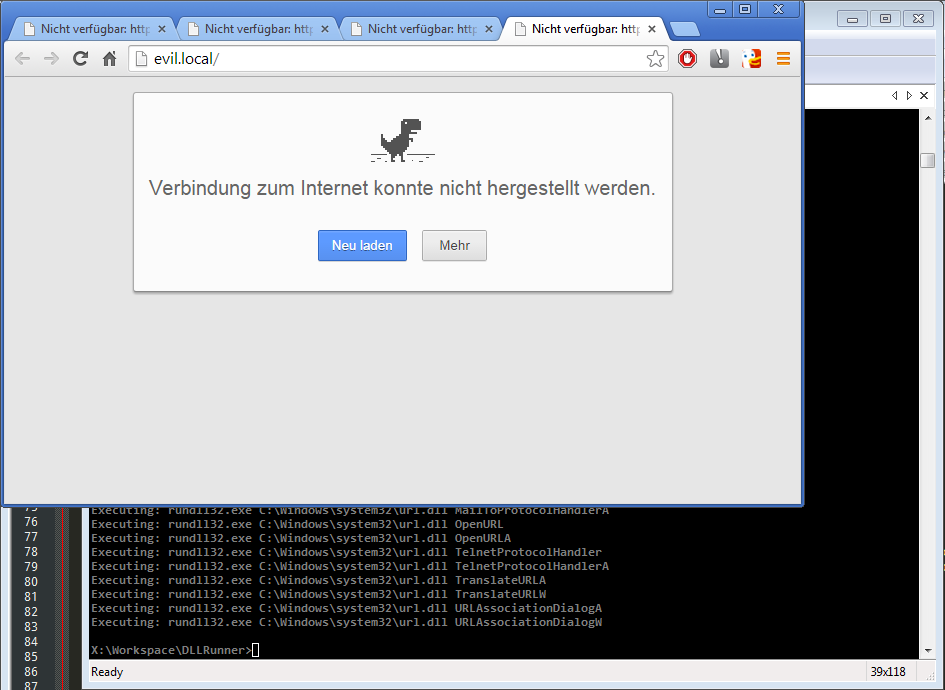
Running DLLRunner in Fuzzing mode
I am still not sure if this is something useful. I have to do further testing to improve the fuzzing idea. I am open to any advice and would like to see something like this integrated in common sandboxes like cuckoo.