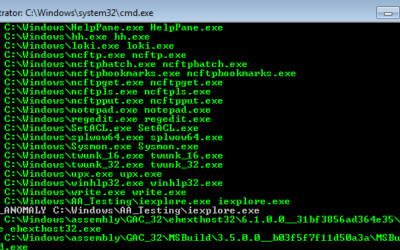
Every month the Nextron Threat Research Team (NTRT) shares insights into evasive threats that we’ve seen in the wild via our Valhalla service. The aim is to highlight interesting samples our rules detected and have or had very low detection rates as reported by...
Using THOR Lite to scan for indicators of Lazarus activity related to the 3CX compromise
On March 29, 2023 CrowdStrike detected malicious activity, originating from a legitimate, signed binary called 3CXDesktopApp. The binary is part of a softphone system developed by 3CX.The observed malicious activity consisted of beaconing to infrastructure controlled...
Not All IOC Scanning Is the Same
In the recent months I had several talks with friends and coworkers about IOC scanning and how to integrate IOCs from threat intel feeds into our scanners or other products that our customers already use. People often tell me that EDR or client management product X...
How to Fall Victim to Advanced Persistent Threats
During the last four years, I was engaged on incident response teams for several large advanced persistent threat (APT) cases involving different German corporations. In this time, we have developed methods and tools to detect compromised systems, while also planning...
Synergetic Effects of Network and Host Based APT Detection
People often ask me if they still need our host based scanner THOR now that they have bought a network appliance that already checks all content that goes into and leaves their network. I normally answer that it is not a question of one solution versus another, but a...
Detect System File Manipulations with SysInternals Sysmon
SysInternals Sysmon is a powerful tool especially when it comes to anomaly detection. I recently developed a method to detect system file manipulations, which I would like to share with you. We know how to track processes with the standard Windows audit policy option...
APT Detection is About Metadata
People often ask me, why we changed the name of our scanner from "IOC" to "APT" scanner and if we did that only for marketing reasons. But don't worry, this blog post is just as little a sales pitch as it is an attempt to create a new product class. I'll show you why...
How to Scan for System File Manipulations with Yara (Part 2/2)
As a follow up on my first article about inverse matching yara rules I would like to add a tutorial on how to scan for system file manipulations using Yara and Powershell. The idea of inverse matching is that we do not scan for something malicious that we already know...