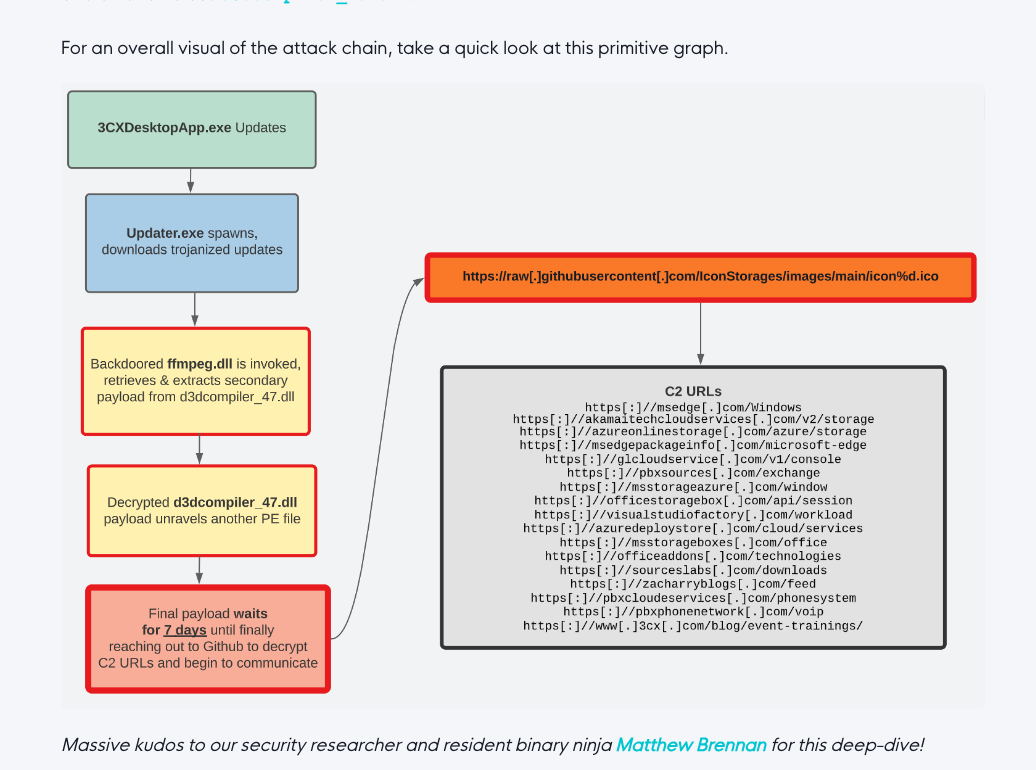
On March 29, 2023 CrowdStrike detected malicious activity, originating from a legitimate, signed binary called 3CXDesktopApp. The binary is part of a softphone system developed by 3CX.
The observed malicious activity consisted of beaconing to infrastructure controlled by the actors, leading to the deployment of second-stage payloads and in a few cases direct on-keyboard activity from the attackers.
You can find more information on the threat in the following articles by CrowdStrike, Volexity and Huntress Labs:
CrowdStrike Report
The first report on the activity linking it to LABYRINTH CHOLLIMA aka Lazarus group.
Volexity Article
This article by Volexity lists a lot of indicators and reports on the final stage in form of the stealer ICONIC
Huntress Labs Article
Huntress Labs report on the activity including process patterns, rules and IOCs
After the compromise became first known, we began our own investigation and in the following few hours released a number of detection rules to our public repositories.
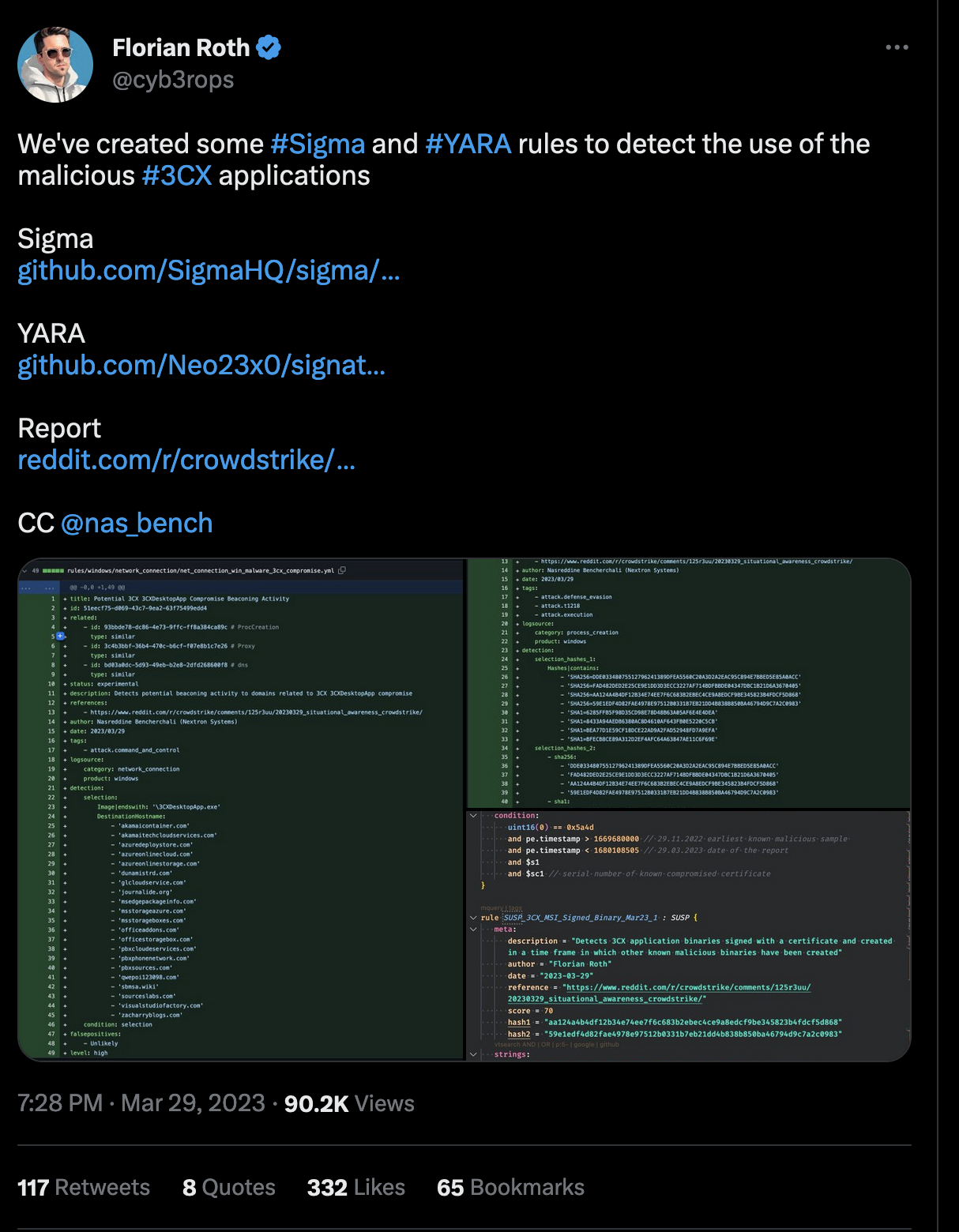
While having the detection in place is a great start, often times it’s not an easy task to assess the situation and make sure that no system in the network is affected by the threat.
One way to leverage these rules and quickly scan your own environment for free, is using THOR Lite scanner.
Enter THOR Lite
THOR Lite is the reduced version of our compromise assessment scanner THOR. It uses YARA rules and Indicators of Compromise (IOC) like hash values and file names to detect malicious activity.
In this technical blog article, we’ll explore how to levreage THOR Lite to scan end systems for signs of malicious activity related to the 3CX compromise.
We’ll also discuss the various types of indicators that THOR Lite can detect, walk through the process of setting up and configuring the tool, and provide tips for interpreting the scan results.
By the end of this article, you should have a solid understanding of how to use THOR Lite to run a compromise assessments within your network.
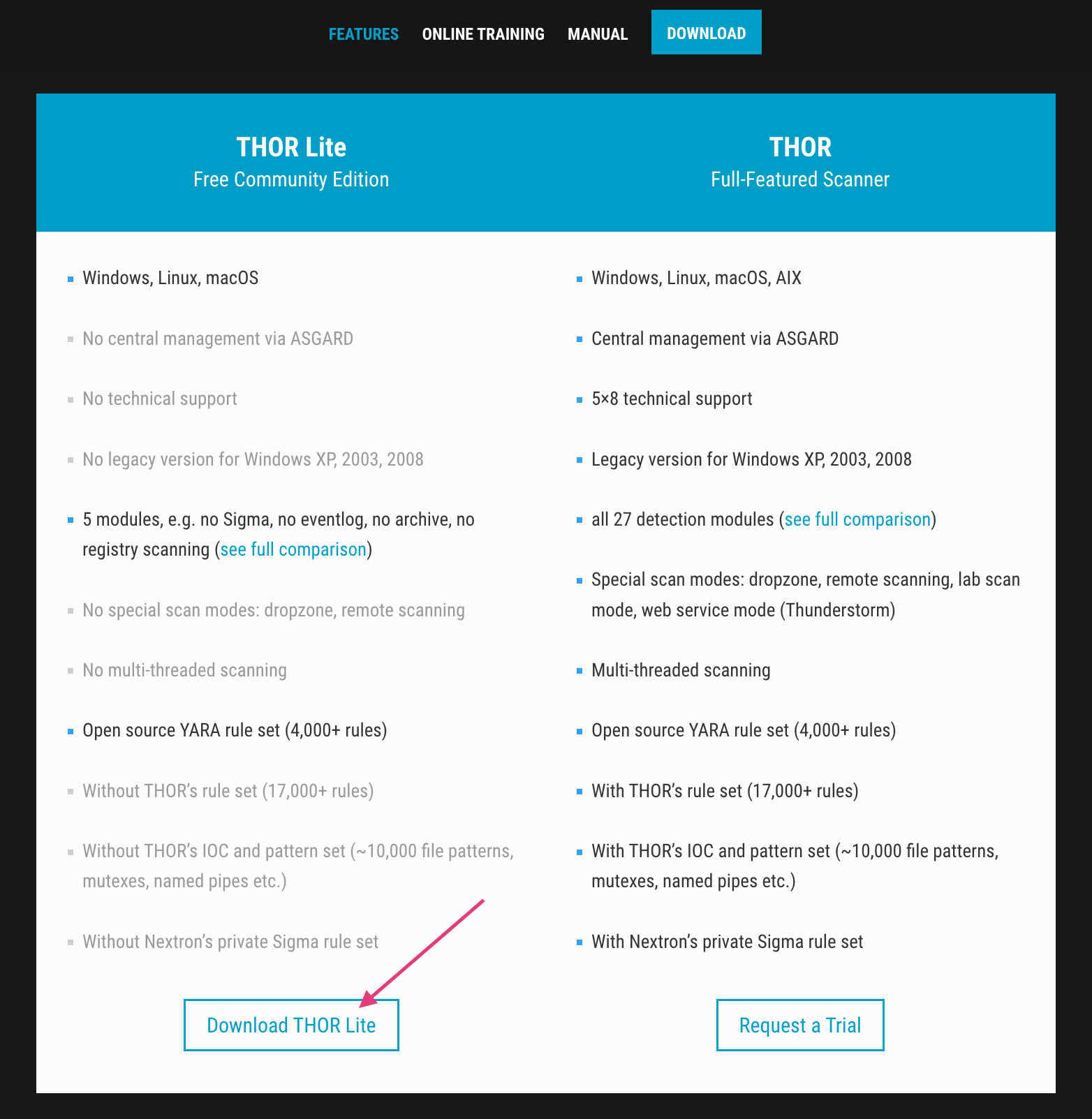
Download THOR Lite
Visit the product page, subscribe to the newsletter to get the program package and the license file.
(note: we offer a special license file to 3CX customers that enables an additional module from the full version to extend the detection coverage even more)
You can download this special license here: (expires 30.04.2023)
Email content:

Getting Started
After you’ve downloaded the program package as a ZIP archive, extract it and place the license file (.lic) in the program folder.
Double click on the “thor64-lite.exe” to run it without any flags or open a Windows command line as an administrator and navigate to the folder where you’ve extracted the program package.
You should then see the scan window that closes automatically when the scan is complete. Usually scans take between 1-4 hours, but there are some ways to speed up the scan.
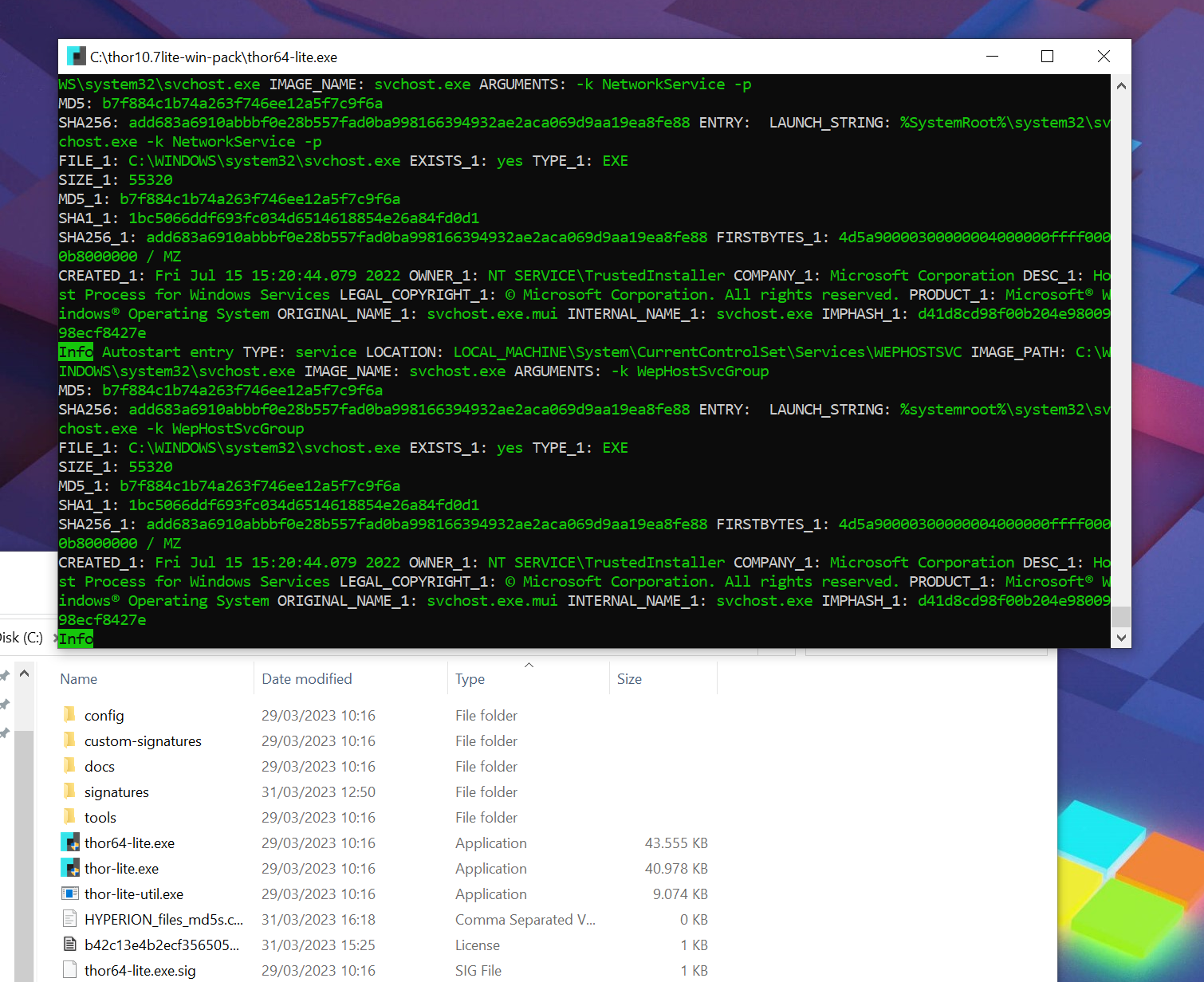
Flags to Consider
--nosoft --nolowprio
If you’re scanning virtual machines or systems that are under a constant high load by other processes, it could be helpful to use the “–nosoft” and “–nolowprio” flags to let THOR run with the same process priority as any other regular process.
--lookback 150 --global-lookback
If you’re interested in scanning recently created files and log entries. These flags instruct THOR to only scan elements created or changed within the last 150 days (why 150?). It would ignore any file or eventlog entry older than that and thus scan a much smaller set of elements.
--cpulimit 30
To minimize the impact for the end user working on a system while it is getting scanned, you can reduce the CPU usage of the scanner to e.g. 30% to avoid them taking notice of the scan by reducing the overall load and fan noise.
Recommended CommandLine Flags For The 3CX Use Case
If a normal scan takes too long, we recommend the following command line flags in order to reduce the scan duration by restricting the scan to the changes of the last 150 days:
thor64-lite.exe --nolowprio --lookback 150 --global-lookback
In order to reduce the CPU usage and make it as imperceptible as possible to the end user working on the scanned systems use the following command:
thor64-lite.exe --lookback 150 --global-lookback --cpulimit 35
Update the Signatures
We’re constantly working on enhancing and updating the signatures related to the 3CX compromise. Updates are to be expected over the weekend and next week. To make sure THOR always works with the newest set of signatures use the following command:
thor-lite-util.exe upgrade
Interpreting the Scan Results
During the scan you’ll see several messages in green and blue colours. Warning and alert messages use a yellow or red color. But don’t worry when you notice a message of that color. Remember that THOR is a scanner that highlights malicious and suspicious elements for review by an administrator or forensic analyst. Not everything shown as a “warning” message has to be a real threat.
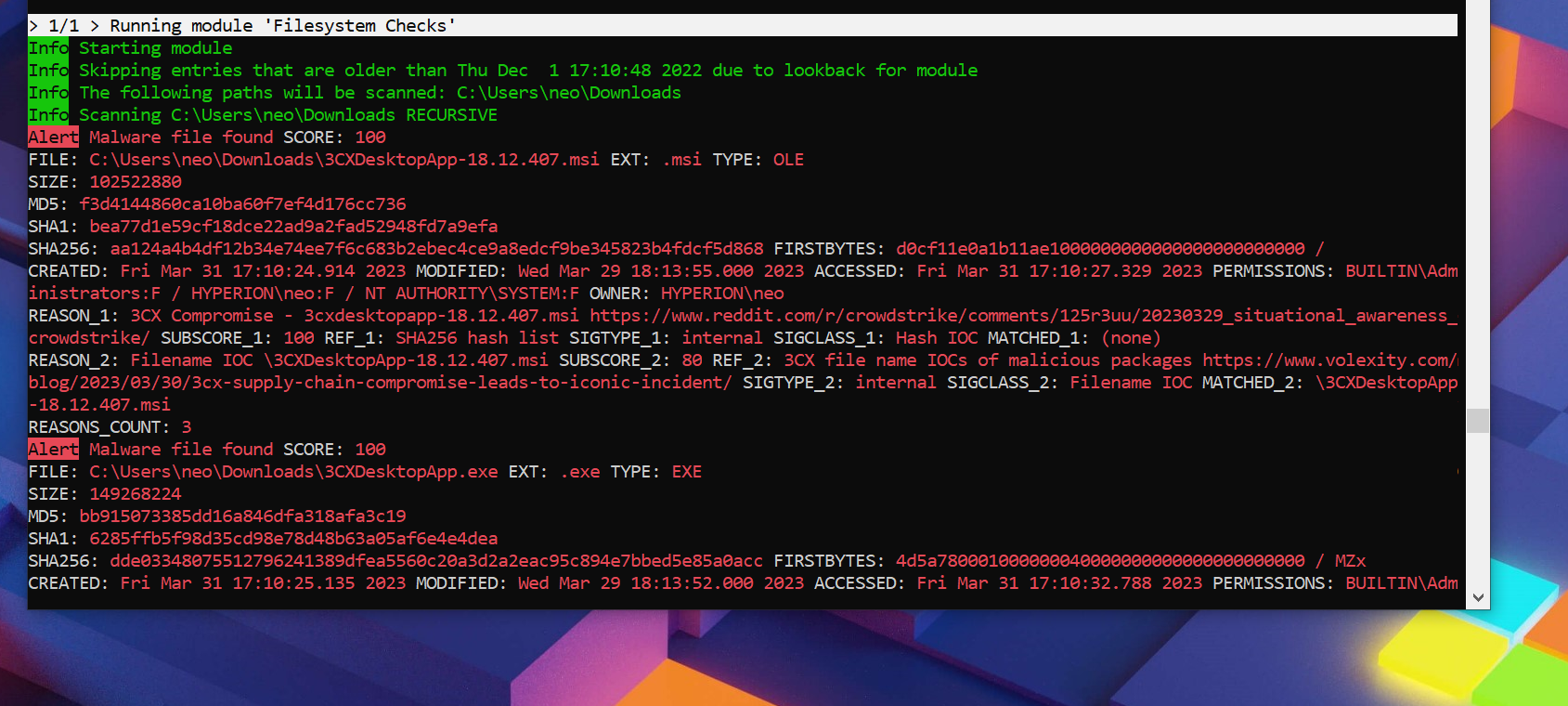
After the scan finishes, users can find an HTML report in the program folder that lists all findings.
We recommend searching the HTML report for the “3CX” keyword and only review matches with the specific IOCs and YARA rules related to this activity.
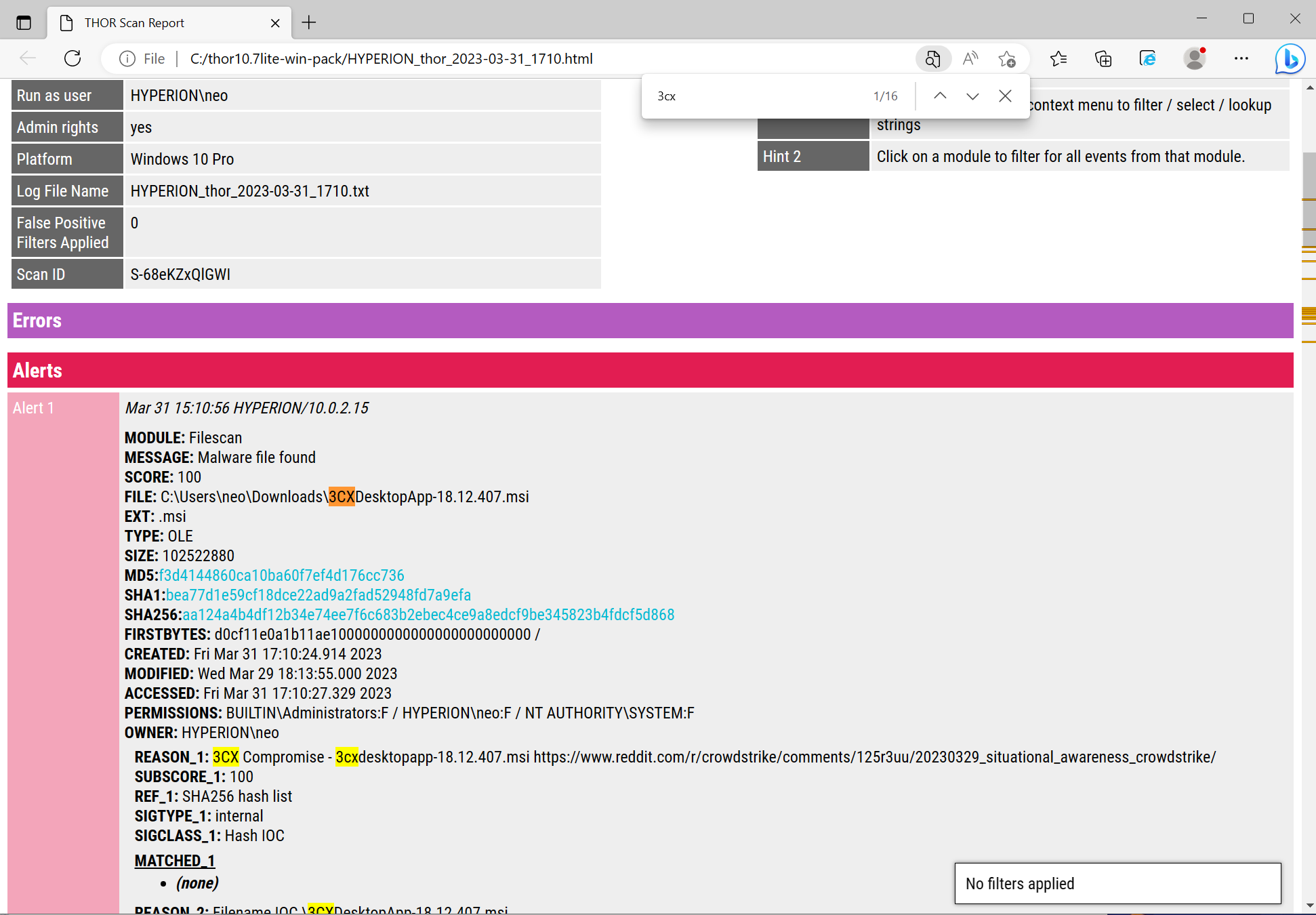
THOR Lite is able to detect various forensic artefacts:
- The installer files
- The malicious binaries
- The loaded malware in-memory
- Process connections to known C2 addresses
- Traces of activity in local log files
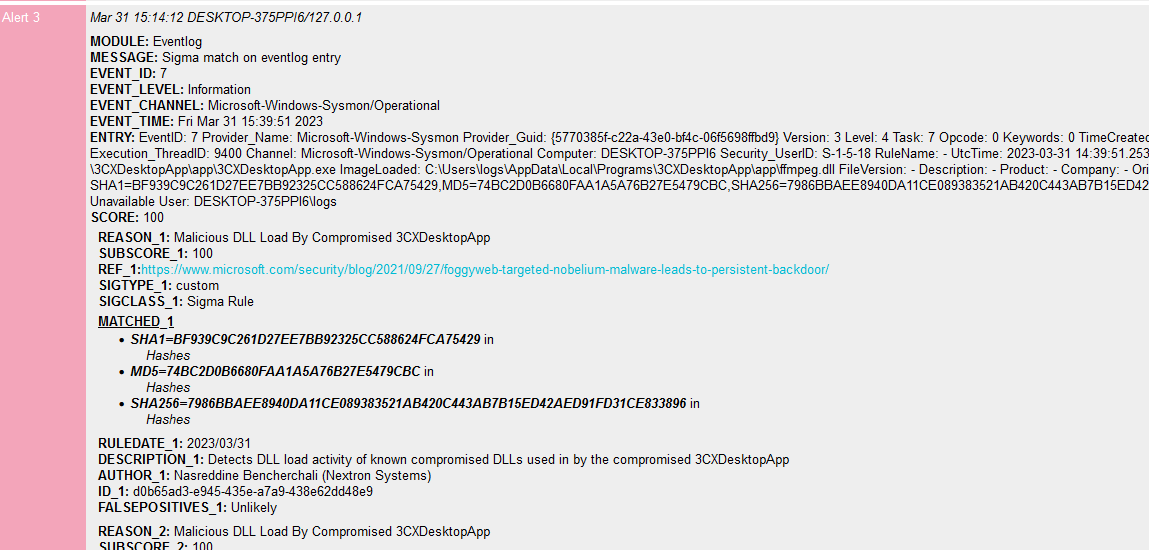
We’re also offering a special license (3cx.lic) to 3CX and their customers that will activate a special feature called “Sigma Scanning” in THOR Lite instances. This allows them to apply the Sigma rules mentioned below (and 1600+ more) on the event logs of a scanned end system.
A match with one of these Sigma rules would look like this:
You can download this special license here: (expires 30.04.2023)
Continuous Compromise Assessment: Enhancing Detection Capabilities to Mitigate High-Profile Cyber Attacks
One more time, we are all taken aback by yet another sudden high-profile compromise. Just like the Sunburst or HAFNIUM Attack, the 3CX compromise arose out of nowhere, putting companies of all kinds across the globe at risk. We may later discover that some organizations were exploited for months before the 3CX compromise was ultimately made public.
But does it truly have to come as such a surprise to everyone? Looking back at the Hafnium attack, Nextron discovered that many organizations had been breached by various attack groups, all of whom appeared to have used the proxy shell/proxy logon weakness. All attackers who expanded their breach brought their own toolset for persistence and post-exploitation. Nothing new so far.
However, what if we could automatically detect an attacker’s toolkit after it has been deployed? In this case, we could efficiently detect these breaches long before day zero simply by identifying secondary tools that appear magically on a system. Let’s assume we scan our systems weekly, searching for all kinds of Indicators of Compromise, known attacker tools, or traces of their methods. Then, even without knowing that the 3CX compromise exists, we would most likely be able to detect attacks that make use of it within a week. This would give us a heads up before bad things even begin to happen, shocking everyone.
This is precisely Nextron’s “Continuous Compromise Assessment” approach. With our orchestration platform ASGARD, we can conduct recurrent and automated compromise assessments using our full-featured Scanner THOR. Our first and initial scan represents what we call the baseline. We would analyze all events from the first scan and, starting with the next week, focus on any deviations from this baseline. In such a scenario, we would detect breaches based on secondary toolsets from one week to another. While we still would not detect the 0-day itself, the secondary toolset would show up very prominently as a deviation from the baseline.
There is not much effort required to gain a considerable amount of additional detection capabilities.
Signatures
The following listings show all the signatures we’ve made public and used in THOR Lite to detect malicious activity
YARA (public)
SIGMA (public)
Potential Compromised 3CXDesktopApp Beaconing Activity – Proxy
UUID: 3c4b3bbf-36b4-470c-b6cf-f07e8b1c7e26
Potential Compromised 3CXDesktopApp ICO C2 File Download
UUID: 76bc1601-9546-4b75-9419-06e0e8d10651
Potential Compromised 3CXDesktopApp Beaconing Activity – DNS
UUID: bd03a0dc-5d93-49eb-b2e8-2dfd268600f8
Potential Compromised 3CXDesktopApp Beaconing Activity – Netcon
UUID: 51eecf75-d069-43c7-9ea2-63f75499edd4
Potential Suspicious Child Process Of 3CXDesktopApp
UUID: 63f3605b-979f-48c2-b7cc-7f90523fed88
Malicious DLL Load By Compromised 3CXDesktopApp
UUID: d0b65ad3-e945-435e-a7a9-438e62dd48e9
Potential Compromised 3CXDesktopApp Execution
UUID: 93bbde78-dc86-4e73-9ffc-ff8a384ca89c
Potential Compromised 3CXDesktopApp Update Activity
UUID: e7581747-1e44-4d4b-85a6-0db0b4a00f2a
IOCs
C2 IOCs
c2-iocs.txt @ signature-base
Filename IOCs
filename-iocs.txt @ signature-base
Hash IOCs
hash-iocs.txt @ signature-base
Full THOR Version
Keep in mind that THOR Lite is only a demo version of our full scanner with more than 27 detection modules and more than 20,000 YARA rues compared to the 5 modules and 2,500 rules used in THOR Lite.
You can find a full feature comparison here and a blog post that explains the differences in more detail here.