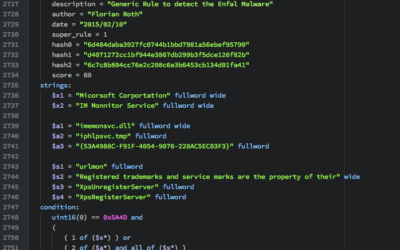
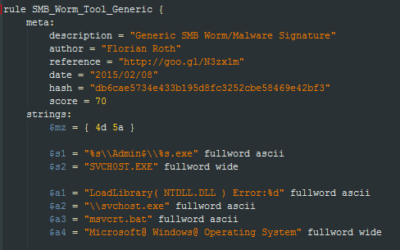
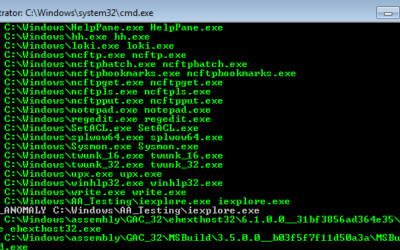
Download the Antivirus Event Analysis Cheat Sheet version 1.8.1 here.
Web Proxy Event Analysis Cheat Sheet
The "Web Proxy Event Analysis Cheat Sheet" can help SOCs and security analysts classify proxy events (blocks, alerts) and is based on my ideas and many ideas from experts that helped me collect detection ideas for this document. You can download version 1.0 here. We...
How to Fall Victim to Advanced Persistent Threats
During the last four years, I was engaged on incident response teams for several large advanced persistent threat (APT) cases involving different German corporations. In this time, we have developed methods and tools to detect compromised systems, while also planning...
How to Write Simple but Sound Yara Rules – Part 3
It has been a while since I wrote "How to Write Simple but Sound Yara Rules - Part 2". Since then I changed my rule creation method to generate more versatile rules that can also be used for in-memory detection. Furthermore new features were added to yarGen and...
YARA Rules to Detect Uncommon System File Sizes
YARA is an awesome tool especially for incident responders and forensic investigators. In my scanners I use YARA for anomaly detection on files. I already created some articles on "Detecting System File Anomalies with YARA" which focus on the expected contents of...
How to Write Simple but Sound Yara Rules – Part 2
Months ago I wrote a blog article on "How to write simple but sound Yara rules". Since then the mentioned techniques and tools have improved. I'd like to give you a brief update on certain Yara features that I frequently use and tools that I use to generate and test...
Splunk Threat Intel IOC Integration via Lookups
Today most security teams have access to a lot of different information sources. On the one hand they collect log data from different sources and try to correlate them in a useful way in so-called SIEM systems. On the other hand they receive threat information from...
Detect System File Manipulations with SysInternals Sysmon
SysInternals Sysmon is a powerful tool especially when it comes to anomaly detection. I recently developed a method to detect system file manipulations, which I would like to share with you. We know how to track processes with the standard Windows audit policy option...
APT Detection is About Metadata
People often ask me, why we changed the name of our scanner from "IOC" to "APT" scanner and if we did that only for marketing reasons. But don't worry, this blog post is just as little a sales pitch as it is an attempt to create a new product class. I'll show you why...
How to Write Simple but Sound Yara Rules
During the last 2 years I wrote approximately 2000 Yara rules based on samples found during our incident response investigations. A lot of security professionals noticed that Yara provides an easy and effective way to write custom rules based on strings or byte...
Bash Schwachstelle CVE-2014-6271 Shell Shock erkennen
Dieser Artikel enthält Information dazu, wie Sie die bash Schwachstelle CVE-2014-6271 Shell Shock erkennen und behandeln können. Betroffene Systeme Grundsätzlich sind alle Systeme betroffen, die eine “bash” einsetzen, also Linux Unix AIX Solaris HPUX D.h. auch viele...
Check Point Remote Access Client Auto Deployment
Setting up a client-to-site VPN using the Check Point (CP) Remote Access Client is a common scenario in CP infrastructures. As the central gateway is set up the Remote Access Client is started, connected to the gateway using valid user credentials, the gateway...
How to Scan for System File Manipulations with Yara (Part 2/2)
As a follow up on my first article about inverse matching yara rules I would like to add a tutorial on how to scan for system file manipulations using Yara and Powershell. The idea of inverse matching is that we do not scan for something malicious that we already know...
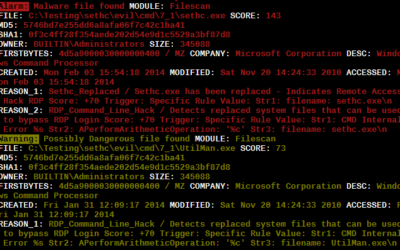
Inverse Yara Signature Matching (Part 1/2)
During our investigations we encountered situations in which attackers replaced valid system files with other system files to achieve persistence and establish a backdoor on the systems. The most frequently used method was the replacement of the "sethc.exe" with the...
Howto detect Ebury SSH Backdoor
Die folgende Yara Signatur kann für die Erkennung der Ebury SSH Backdoor verwendet werden. rule Ebury_SSHD_Malware_Linux { meta: description = "Ebury Malware" author = "Florian Roth" hash = "4a332ea231df95ba813a5914660979a2" strings: $s0 = "keyctl_set_reqkey_keyring"...