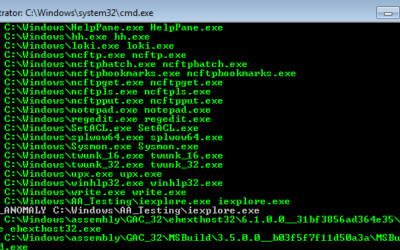
We are pleased to announce a significant enhancement for users of THOR Cloud and THOR Cloud Lite: YARA Forge rule sets are now available for integration. YARA Forge is a curated, quality-assured feed of YARA rules developed as a private project. It automates the...
Introducing THOR Cloud: Next-Level Automated Compromise Assessments
Since the launch of THOR Cloud Lite in September, our team has been dedicated to developing a more powerful version of THOR Cloud that incorporates the full scanner with its extensive suite of forensic modules and expansive detection signature database. Today, we are...
Demystifying SIGMA Log Sources
One of the main goals of Sigma as a project and Sigma rules specifically has always been to reduce the gap that existed in the detection rules space. As maintainers of the Sigma rule repository we're always striving for reducing that gap and making robust and...
Silent Scanning – Compromise Assessment with THOR Lite on a Compromised Exchange 2019 Server
The following video shows a compromise assessment with our free THOR Lite scanner on a Microsoft Exchange 2019 server detecting ProxyShell and ProxyToken exploitation. We've done no post-editing in this video. You can jump to all findings using the video chapters....
THOR Integration into Microsoft Defender ATP
Why Integrate THOR into Microsoft Defender ATP While Microsoft Defender ATP fully plays off its strength in detecting live attacks, suspicious process starts and network connections, THOR shines as a live forensic scanner that scans the local filesystem, registry,...
New Feature in THOR v10.1 – Remote Scanning
THOR v10.1 features a mode of operation that is especially helpful in incident response or compromise assessment scenarios - remote scanning. Imagine that you're in a firefighting scenario - a breach has been confirmed and management wants to have quick results on...
STIXv2 Support in SPARK
SPARK Version 1.17.0 adds extensive STIXv2 support.This allows you to easily extend SPARK's signature bases with IOCs from any sandbox, analysis or threat intel platforms that support STIXv2 export by placing the exported [cci]*.json[/cci] files in the...
How to Write Simple but Sound Yara Rules – Part 3
It has been a while since I wrote "How to Write Simple but Sound Yara Rules - Part 2". Since then I changed my rule creation method to generate more versatile rules that can also be used for in-memory detection. Furthermore new features were added to yarGen and...
How to Scan for System File Manipulations with Yara (Part 2/2)
As a follow up on my first article about inverse matching yara rules I would like to add a tutorial on how to scan for system file manipulations using Yara and Powershell. The idea of inverse matching is that we do not scan for something malicious that we already know...
Incident Response Consulting
In den vergangenen Monaten konnten wir mehrere Kunden bei der Bewältigung und Behandlung massiver Angriffe unterstützen. Zufällige Entdeckungen im Kundennetz zeigten in allen Fällen nur die "Spitze es Eisbergs" größerer und länger andauernder Attacken. Nachdem ein...
Checkpoint Firewall Support und Fehleranalyse mit dem fw.log
Die Erfahrung hat gezeigt, dass es im Umfeld von Checkpoint Firewalls immer wieder dazu kommen kann, dass Firewalls ohne ersichtlichen Grund Anzeichen einer Überlastung aufweisen, indem sie für kurze Zeit nicht mehr erreichbar sind und Verbindungen mit Timeouts...