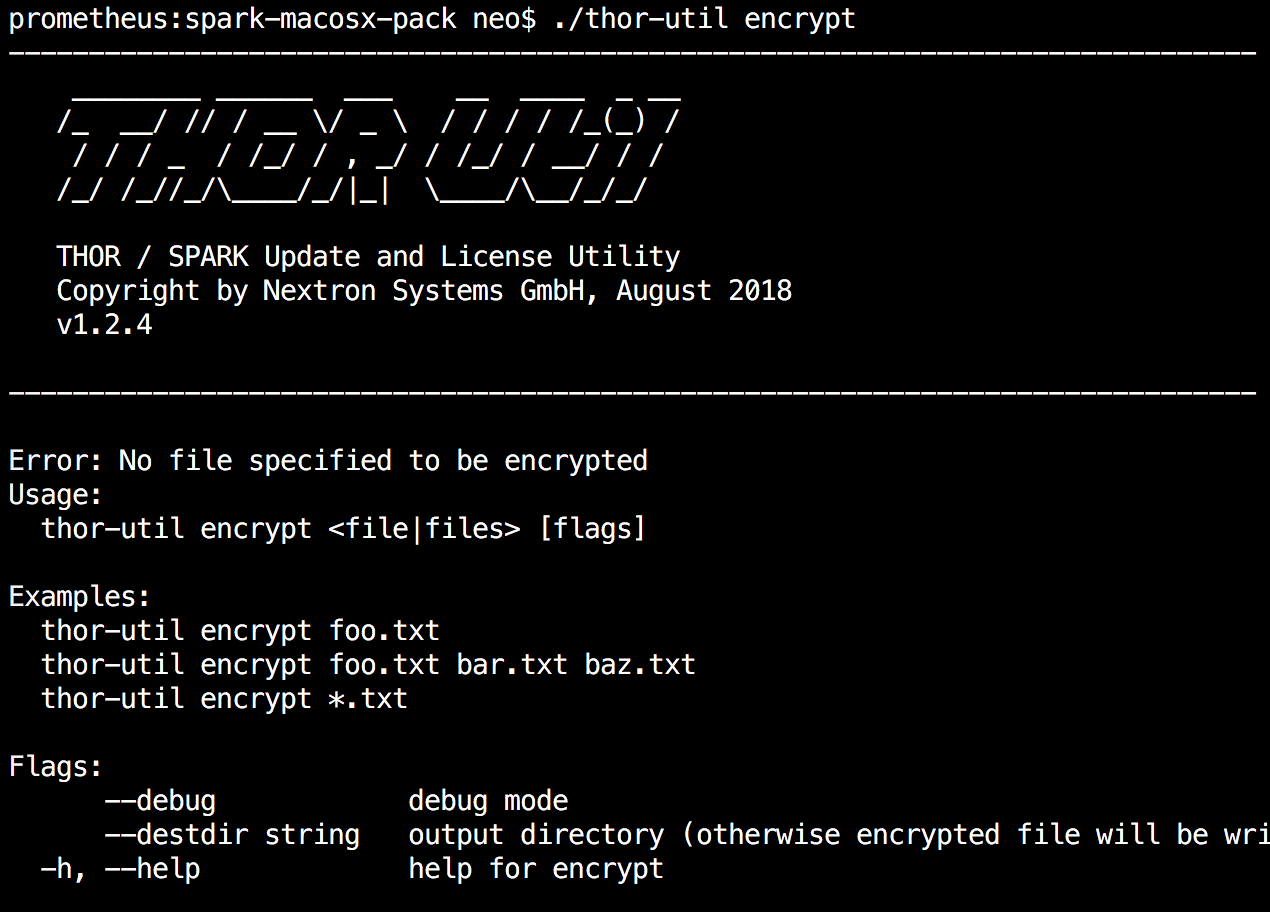
We use a public key in the utilities to encrypt the files for our scanners so that admins, Antivirus engines and attackers won’t be able to read the contents of the files.
After encryption, place the encrypted IOC files in the “./custom-signatures” directory and the encrypted YARA rules in the “./custom-signatures/yara” directory.
- IOC Files: .txt > .dat
- YARA Rules: .yar > .yas
- Sigma Rules: .yml > .yms
Examples:
thor-util.exe encrypt case44.yar thor-util.exe encrypt case44-hashes.txt thor-util.exe encrypt case44-hashes.txt case44.yar thor-util.exe encrypt case44.*
You can use the “upgrade” feature in both tools to get the newest version of the utility.
thor-util upgrade