The newest update of our popular YARA rule feed named VALHALLA adds new features to its web interface.
The most awaited new feature is a keyword search that allows you to query the database for certain keywords, rule names, reports, MITRE ATT&CK ids or tags.
The result page shows you if VALHALLA already has related rules in its database.
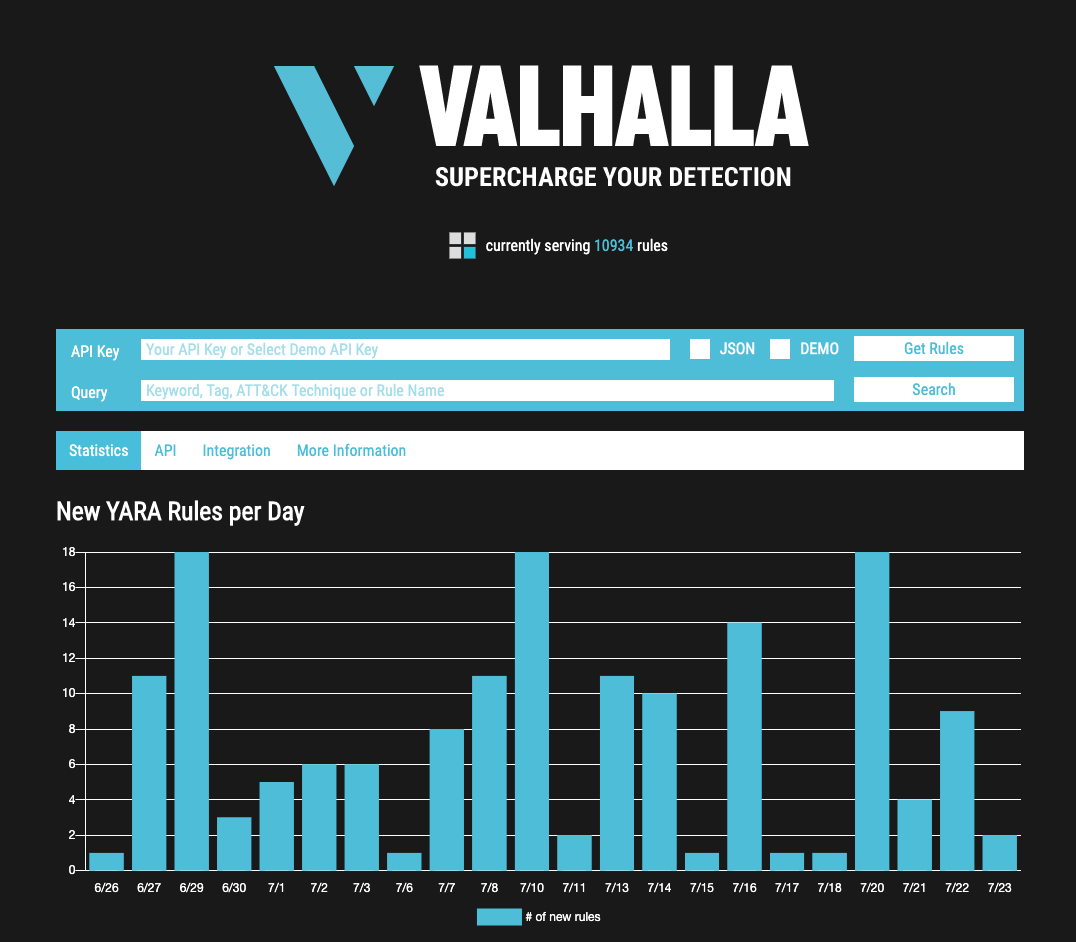
Keyword Search
The search results show all rules in our database related to the search keyword.
You can see the rule name, description, the rule date, a reference URL and a set of links.
The new search function helps you to determine if VALHALLA and THOR already contain rules for a given report or threat.
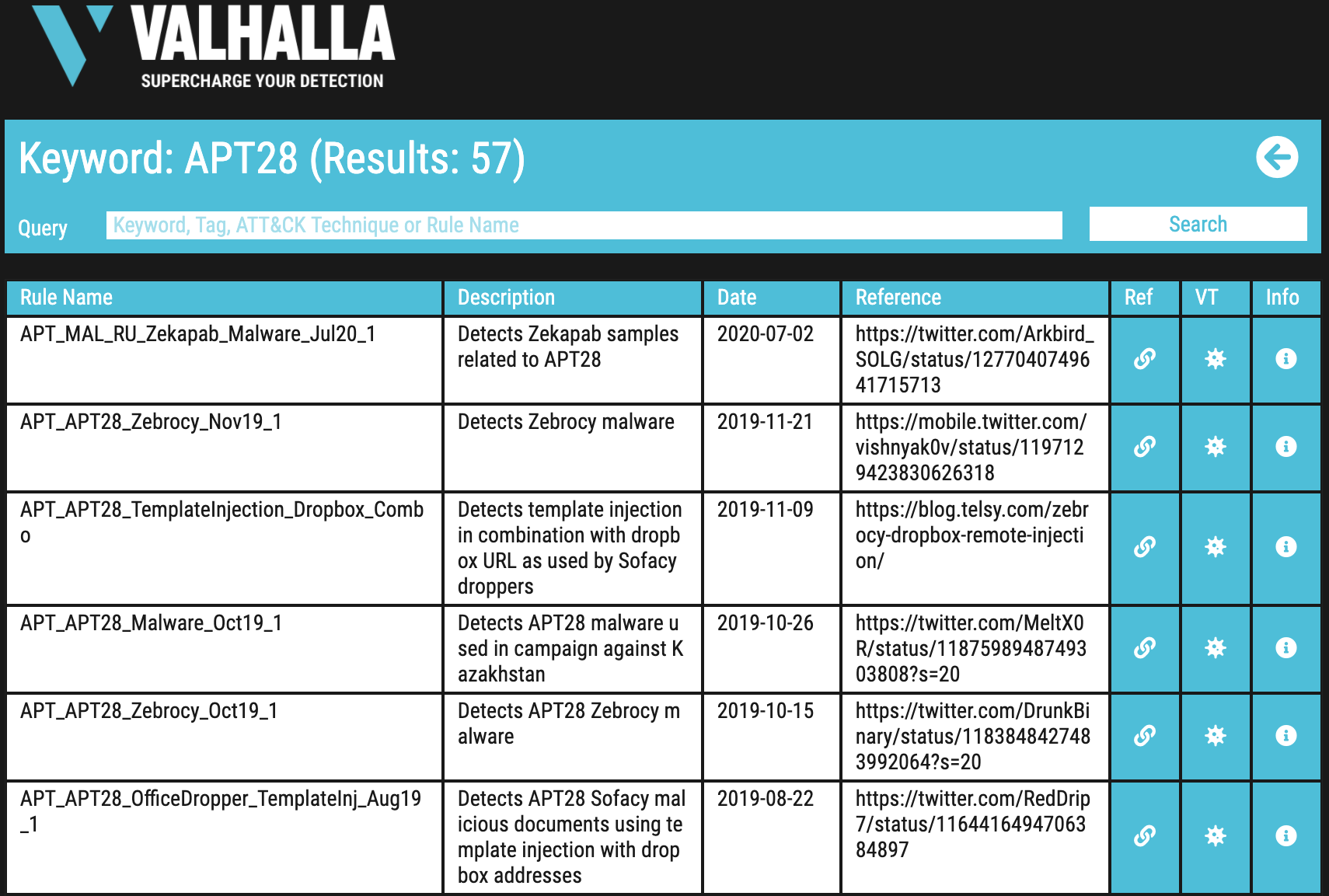
New Links
We have integrated new links that lead you to:
- the reference listed in the rule (report, source)
- a Virustotal lookup for that rule / sample
- a detailed info page for that specific rule
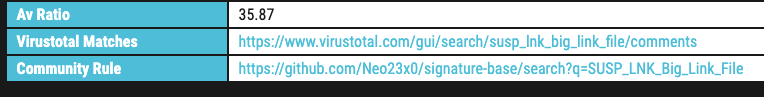
Rule Info Pages
The rule info page contains all the details to a certain rule. These include all metadata values liks score, tags, reference links, required YARA version and modules, the rule date and the average AV detection ratio.
Two additional tables include all antivirus verdicts for samples on which that rule has matched and a list of all observed samples with links to Virustotal.

Community Rule Info
We’ve also added notes on the 2400+ rules that are available as open source in the signature-base repository on github, e.g. try SUSP_LNK_Big_Link_File.
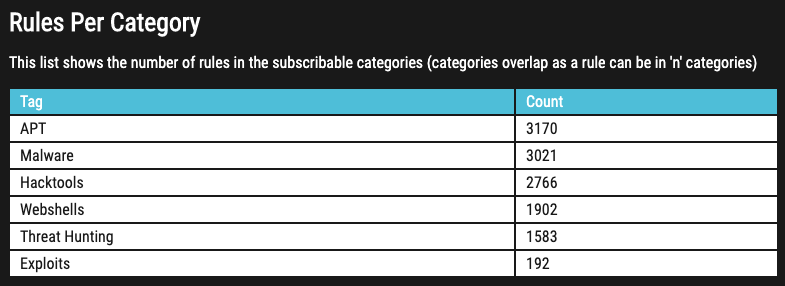
Category Counts
A new table on the start page informs users about the rules per subscribable category.
Also note that queries of any type to Valhalla are rate limited. Too many requests in a relatively short time frame will lead to complete blocks as well as a high amount of requests over a longe time period and other suspicious activity. Customers can get their source IP addresses whitelisted on request.
The new version will be deployed in the coming days.










