Our compromise assessment scanner THOR is able to apply Sigma rules during the local Eventlog analysis. This can help any customer that has no central SIEM system or performs a live forensic analysis on a system group that does not report to central monitoring.
By running THOR on these systems with activated Sigma feature, THOR becomes a kind of a distributed and portable SIEM.
Since the Sigma scan module isn’t active by default, we thought it a good idea to explain how to activate an use it in the best possible way.
Open Source Rule Set
By default THOR uses the open-source Sigma rule set with more than 500+ rules provided by the Sigma project on their Github page.
Since our head of research is also one of the project maintainers, it was reasonable to combine the detection capabilities of Sigma with THOR’s scanning functionality on the endpoint.
We comply with Sigma’s DRL (Detection Rule License) by including the rule authors in the event data produced by these rules.
Custom Sigma Rules
You can easily add you own Sigma rules by placing them in the “./custom-signatures/sigma” sub folder.
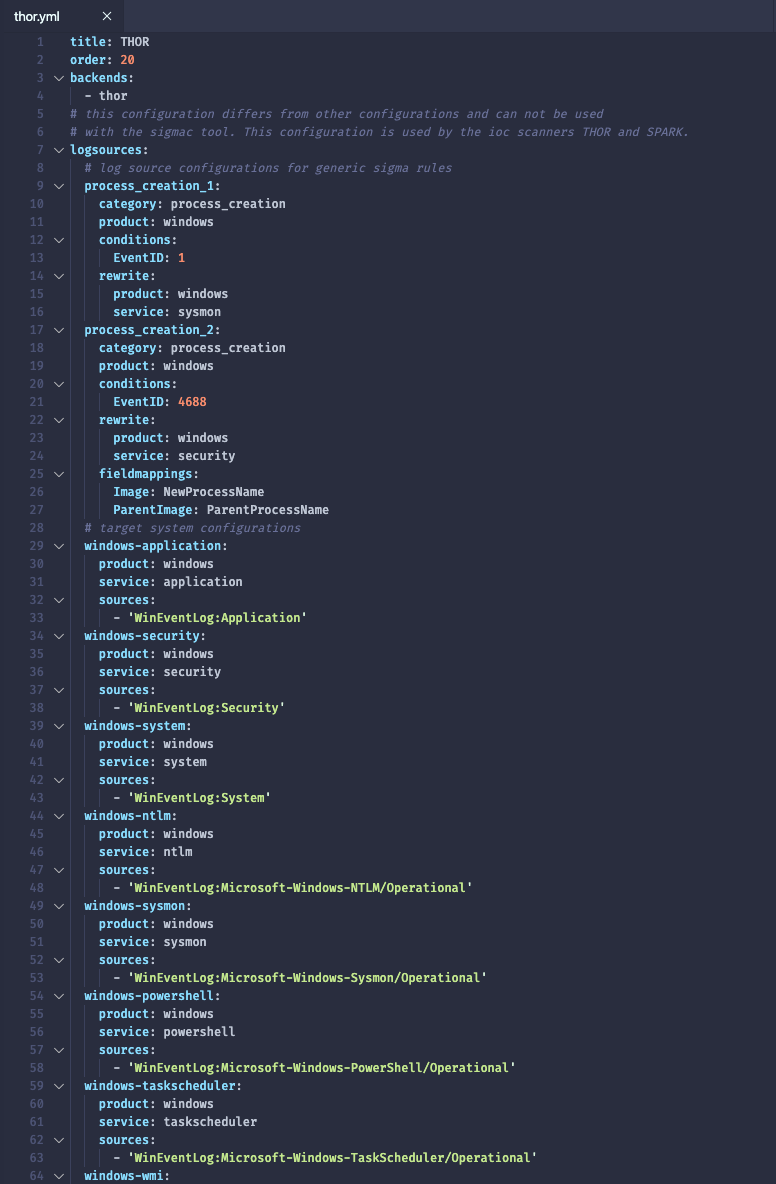
THOR’s Sigma Config
The THOR default configuration for Sigma can be found in the Sigma repository.
This configuration shows you, which Windows Eventlogs and Linux/Unix log files get analyzed by the Sigma module in THOR.
Sigma Scanning
To activate the Sigma module simply use the “–sigma” flag (or “sigma: True” in a YML config file).
You can start a THOR scan that analyzes the local Eventlog and activates the Sigma feature with:
thor64.exe -a Eventlog --sigma
To run a Sigma scan on a single Eventlog e.g. Sysmon’s log, use the “-n” flag.
thor64.exe -a Eventlog --sigma -n "Microsoft-Windows-Sysmon/Operational"
To include the Sigma feature in a standard THOR scan and check only the last 3 days of the Windows Eventlogs to reduce the scan duration, use:
thor64.exe --sigma -lookback 3
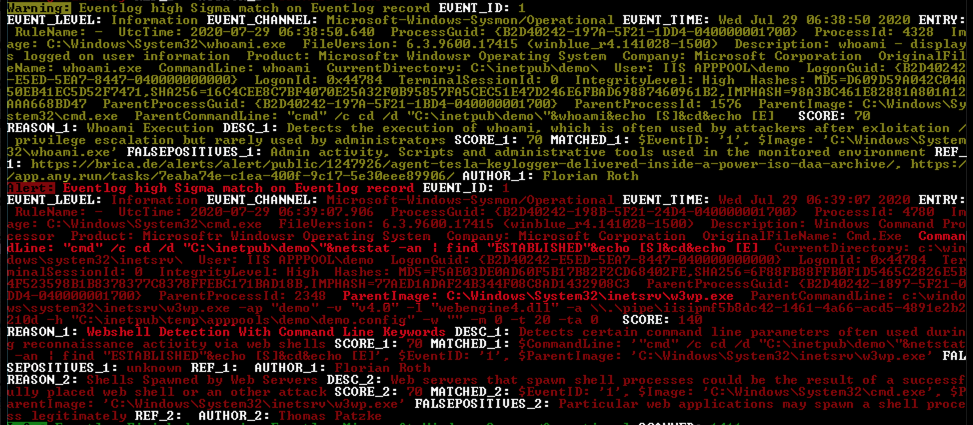
Sigma Matches
Once a Sigma rule matches on a log entry, you’ll see it listed in one of the REASON’s that lead to the classification of an event.
The following example shows the detection of a China Chopper (Caidao) ASP web shell. That web shell has been detected by multiple Sigma rules.
Getting Started
Since this feature isn’t available in THOR Lite, please contact us via the “Get Started” button in the upper right corner and get a free trial voucher. Most customers that use THOR with Sigma choose one of our THOR license packs, especially the SOC Toolkit Pack, which was geared to the needs of today’s SOC teams.










