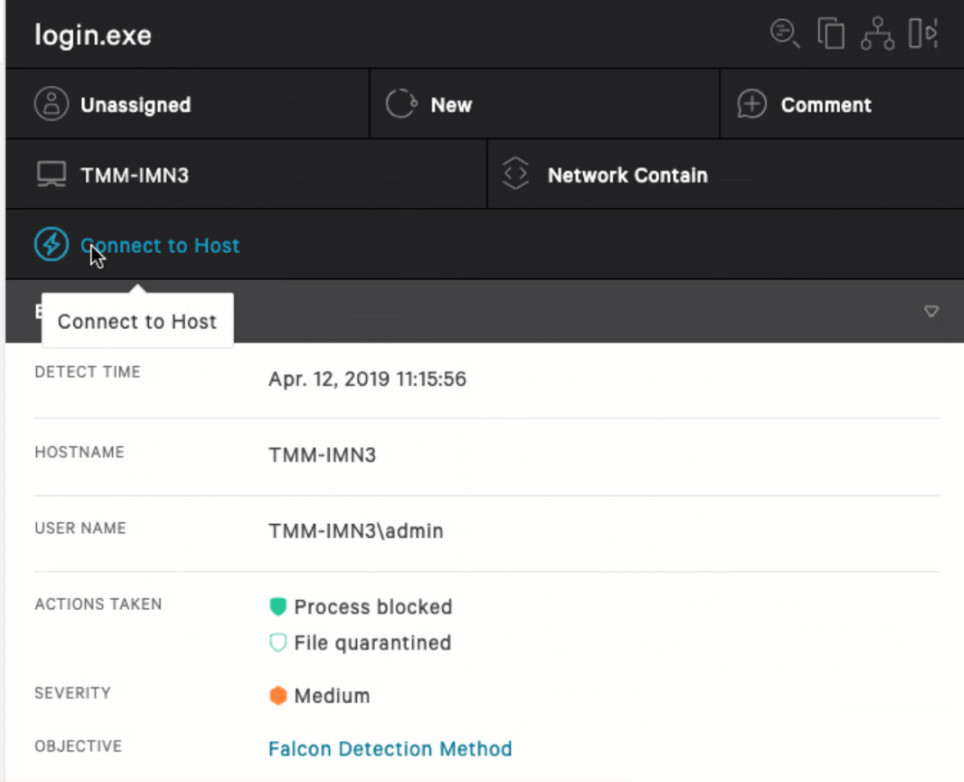
One of our customers has successfully deployed THOR using CrowdStrike’s Falcon Real Time Response.
Falcon’s Real Time Response provides a remote shell that is very similar to Microsoft Defenders ATP’s Live Response, which we’ve already combined with THOR Cloud (see this page).
The most important feature that allows us to integrate THOR is the ability to upload binaries to a remote system and execute them.
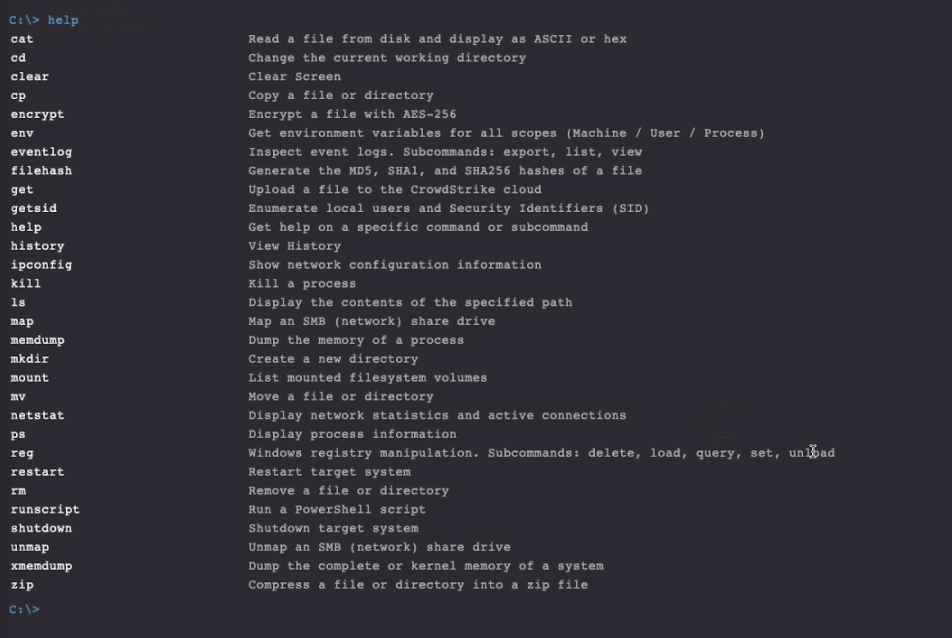
The Real Time Response shell offers a set of commands to interact with the remote system.
We used “put” and “run” to upload and run THOR and “get” to download the scan results.
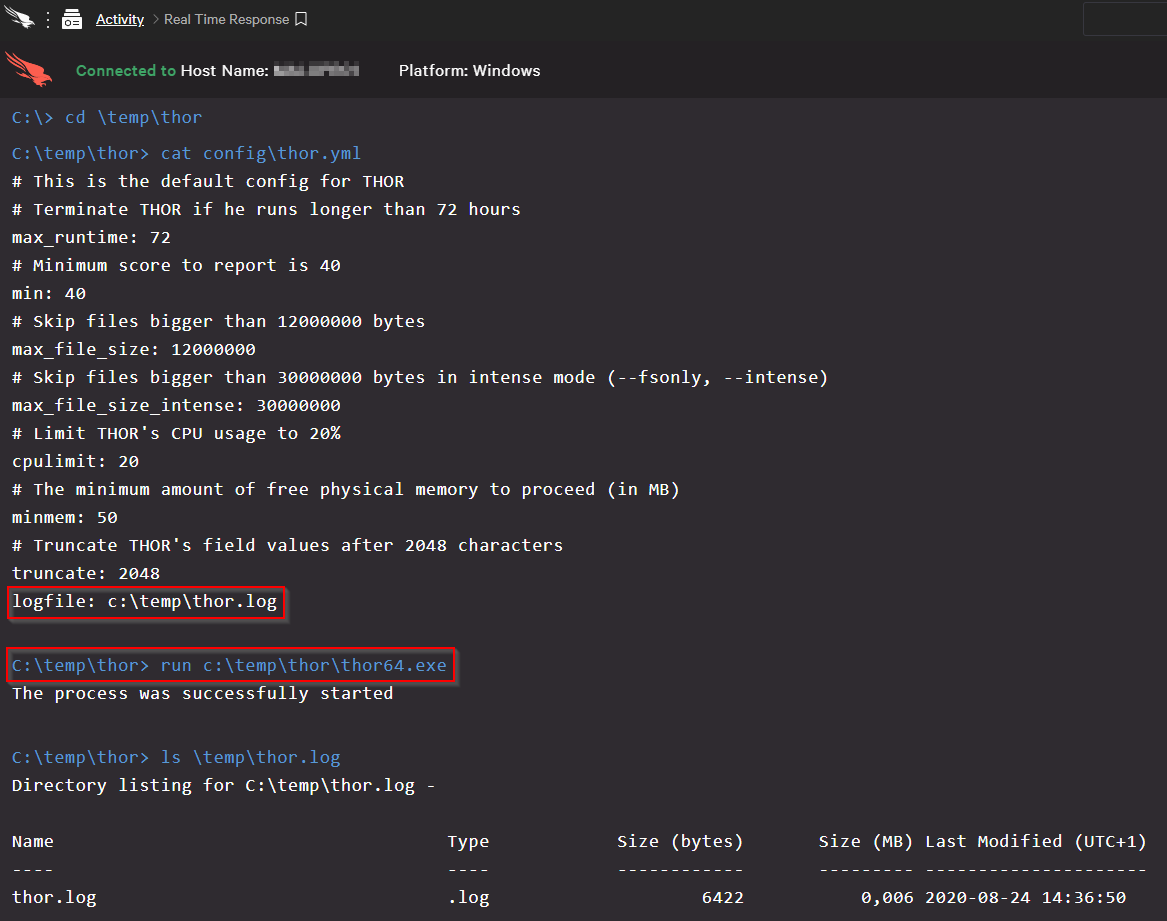
Since the “run” command doesn’t accept any command line flags, it comes in handy that THOR accepts all his command line flags with config files in YAML format.
You can simply put all command line flags that you’d like to use into `thor.yml`, which is the default config file that gets initialized automatically during startup.
You can find more information on the YAML config files in chapter 10 of THOR’s manual.

It is advisable to set a specific output path for the log file or use the “rebase-dir” flag to create all output files in a certain folder. Many users reduce THOR’s CPU load to a lower value to influence the remote system as little as possible.
... rebase-dir: C:\Temp cpulimit: 70
You can then expand the archive using “Expand-Archive thor.zip” (PowerShell) or upload a “7z.exe” on very old systems with old PowerShell versions that don’t support the “Expand-Archive” command.
\temp\thor\**\*.exe
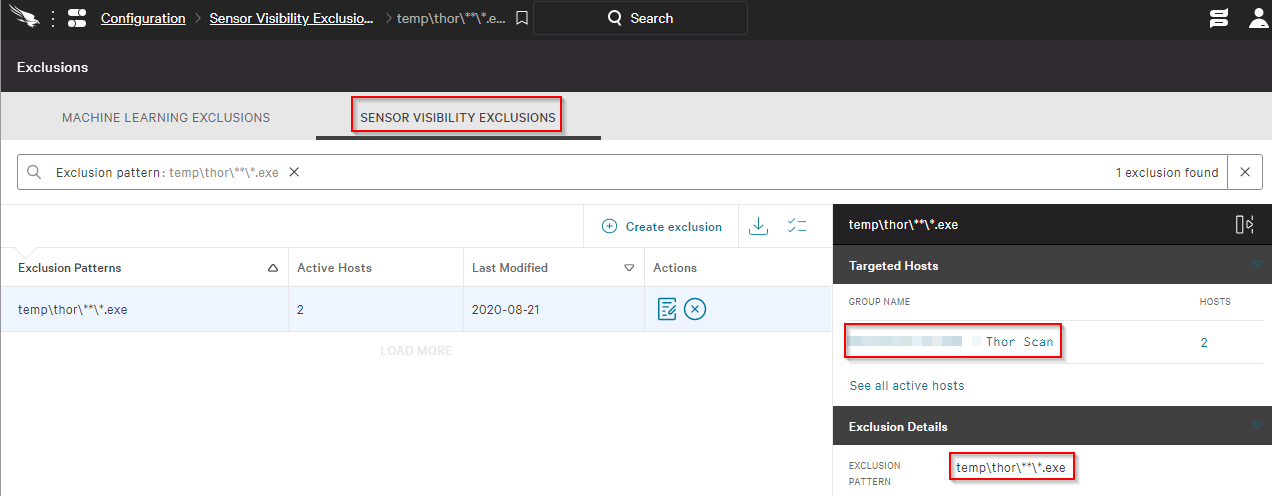
After a successful scan run, you can download the results using the “get” command and remove the exclusion.
It is possible to integrate THOR into many endpoint solutions. If you’d like to check the integration into your solution, please contact us to get a trial version of THOR. We offer special discounts for customers that help us showcase interesting integrations.