The Log4Shell vulnerability (CVE-2021-44228) in log4j is actively exploited in-the-wild and highly critical. This blog posts lists some important web resources and the signatures that detect exploitation attempts.
Explanation of the Vulnerability
LunaSec reported first on the vulnerability.
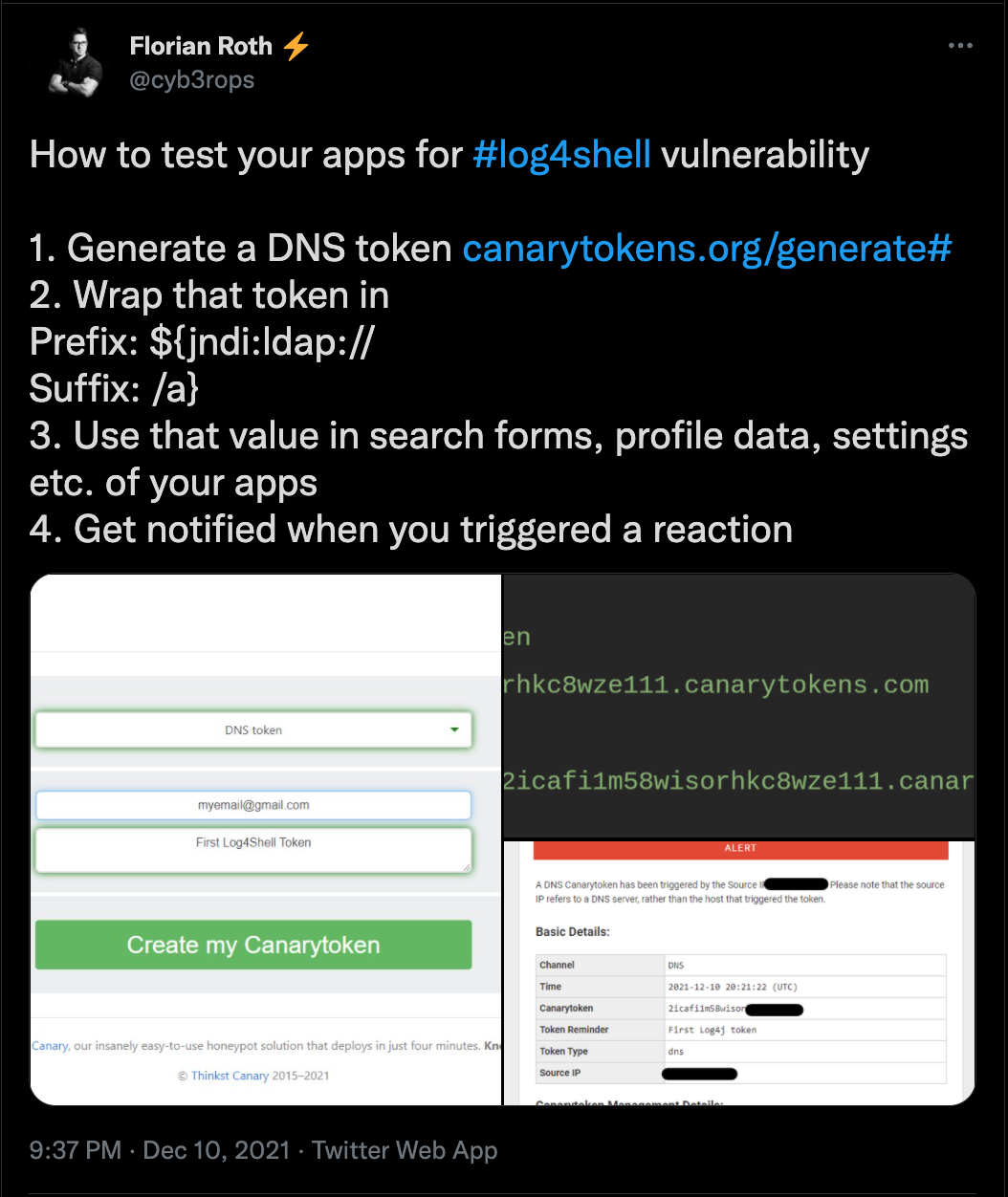
Canary-based Vulnerability Detection
Use this method to detect vulnerable applications and services in your organisation.
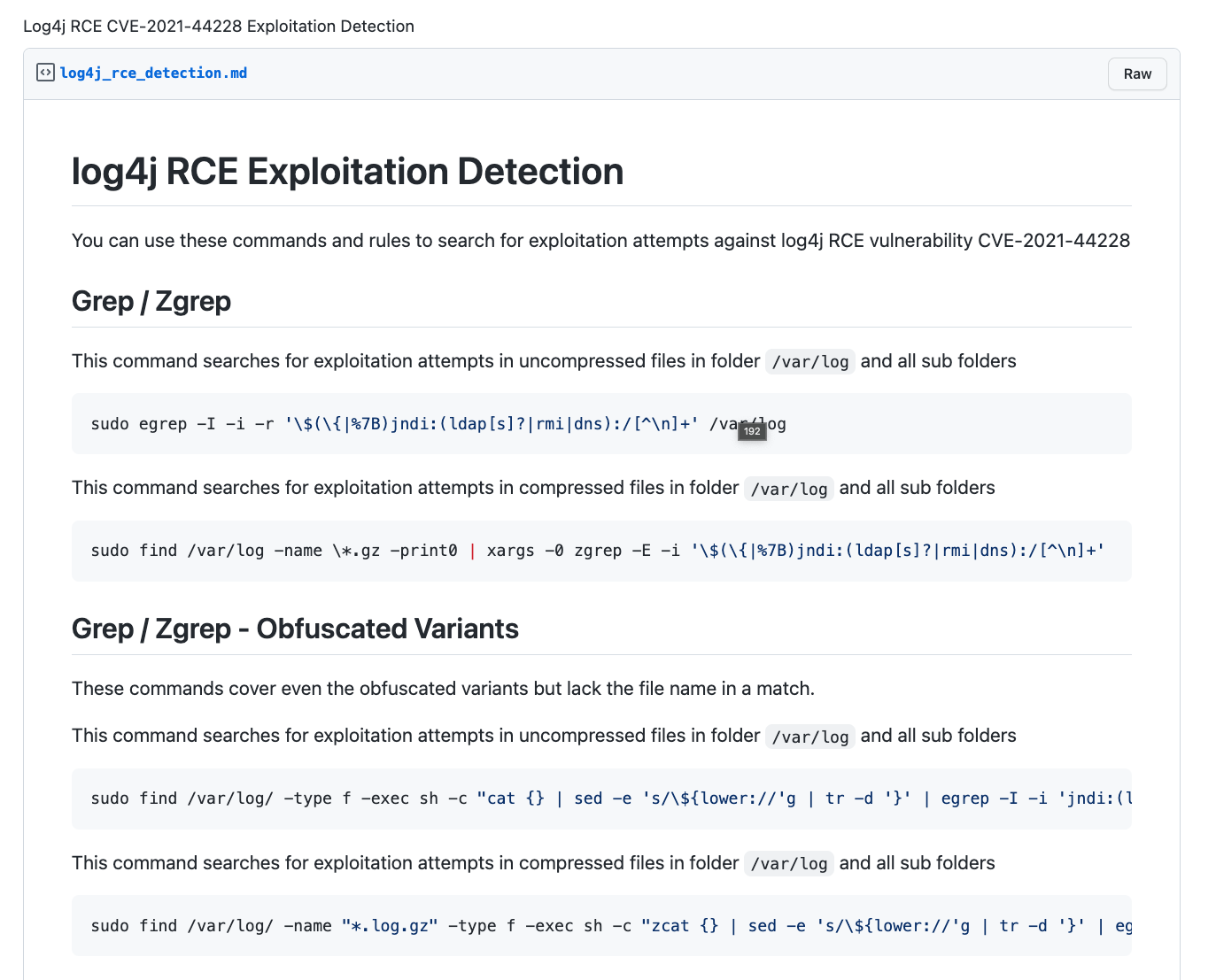
Grep / ZGrep Detection Ideas
Different detection patterns and idea to detect exploitation attempts in log files using grep and zgrep.
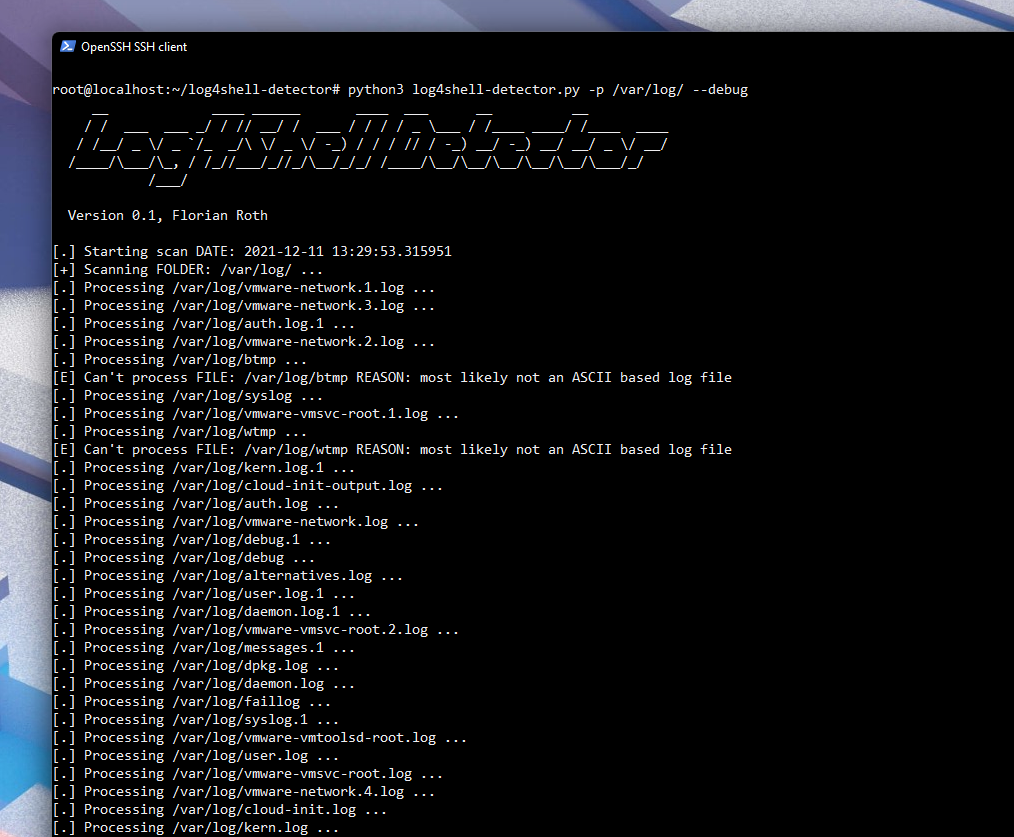
Log4Shell Detector Python Script
A python script that can be used to detect even the most obfuscated versions of the malicious payload.
List of Advisories by Vendors
Big collection of advisories and statements by different vendors that use JAVA and log4j.
List of Vulnerable Software with PoCs
Incomplete list of software products that have proven to be vulnerable.
Log4Shell Vulnerability Scanner (Local Files)
Scans the file system of application servers for vulnerable versions of the log4j module.
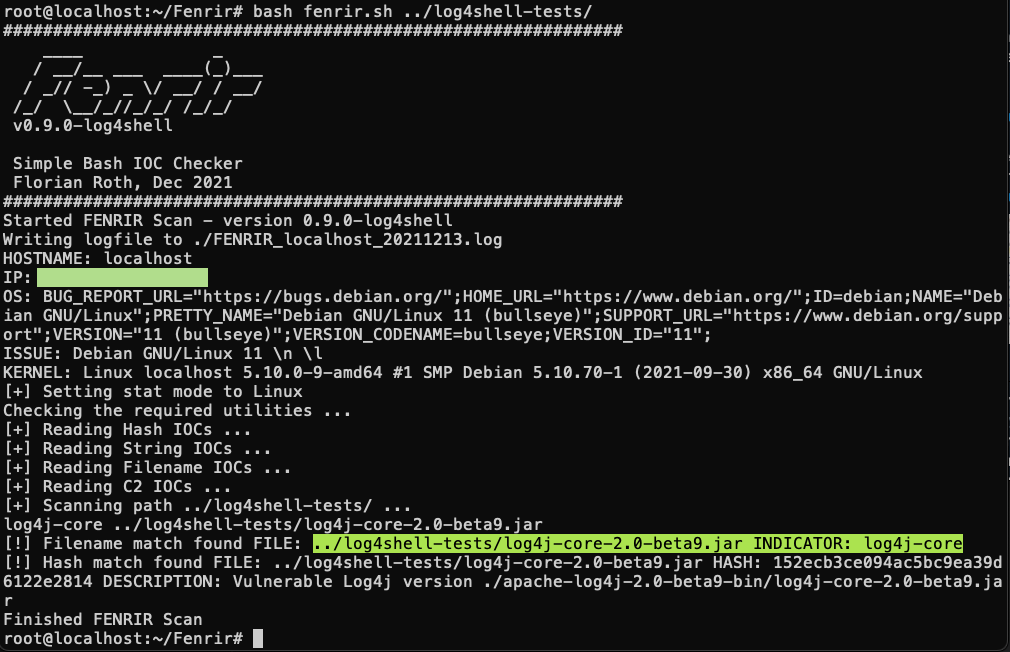
Fenrir Log4Shell Release
A bash based IOC scanner that can be used on any Linux/Unix system to detect traces of the attack and vulnerable log4j versions.
Signatures Detecting Log4Shell Attacks
Check for matches with the following rules:
Exploitation
YARA
- EXPL_Log4j_CVE_2021_44228_Dec21_Soft
- EXPL_Log4j_CVE_2021_44228_Dec21_Hard
- EXPL_Log4j_CVE_2021_44228_JAVA_Exception_Dec21_1
- SUSP_Base64_Encoded_Exploit_Indicators_Dec21
- SUSP_JDNIExploit_Indicators_Dec21
- SUSP_EXPL_OBFUSC_Dec21_1
- EXPL_Log4j_CallBackDomain_IOCs_Dec21_1
- SUSP_EXPL_JAVA_Class_Dec21_1
Sigma
- Log4j RCE CVE-2021-44228 in Fields
UUID: 9be472ed-893c-4ec0-94da-312d2765f654) - Log4j RCE CVE-2021-44228 Generic
(UUID: 5ea8faa8-db8b-45be-89b0-151b84c82702) - JNDIExploit Kit Pattern
(UUID: 412d55bc-7737-4d25-9542-5b396867ce55)
Post-Exploitation
Look for matches with the following rules that trigger on activity observer in-the-wild.
YARA
- SUSP_LNX_SH_Cron_Wget_Apr21_1
- SUSP_LNX_Crontab_Wget_Oct21_1
- SUSP_ShellCommands_Oct19
- Pentest_FullShell_Commands
Sigma
- Suspicious Activity in Shell Commands
(UUID: 2aa1440c-9ae9-4d92-84a7-a9e5f5e31695)
ASGARD Users
It takes us few days to release new rules. The rules that we wrote over the weekend may not be available on Monday 13th of December. ASGARD users that want to use the signatures that are still in our QS, can activate the option for these signatures in “Settings > Advanced > Show Signature SigDev Option”.
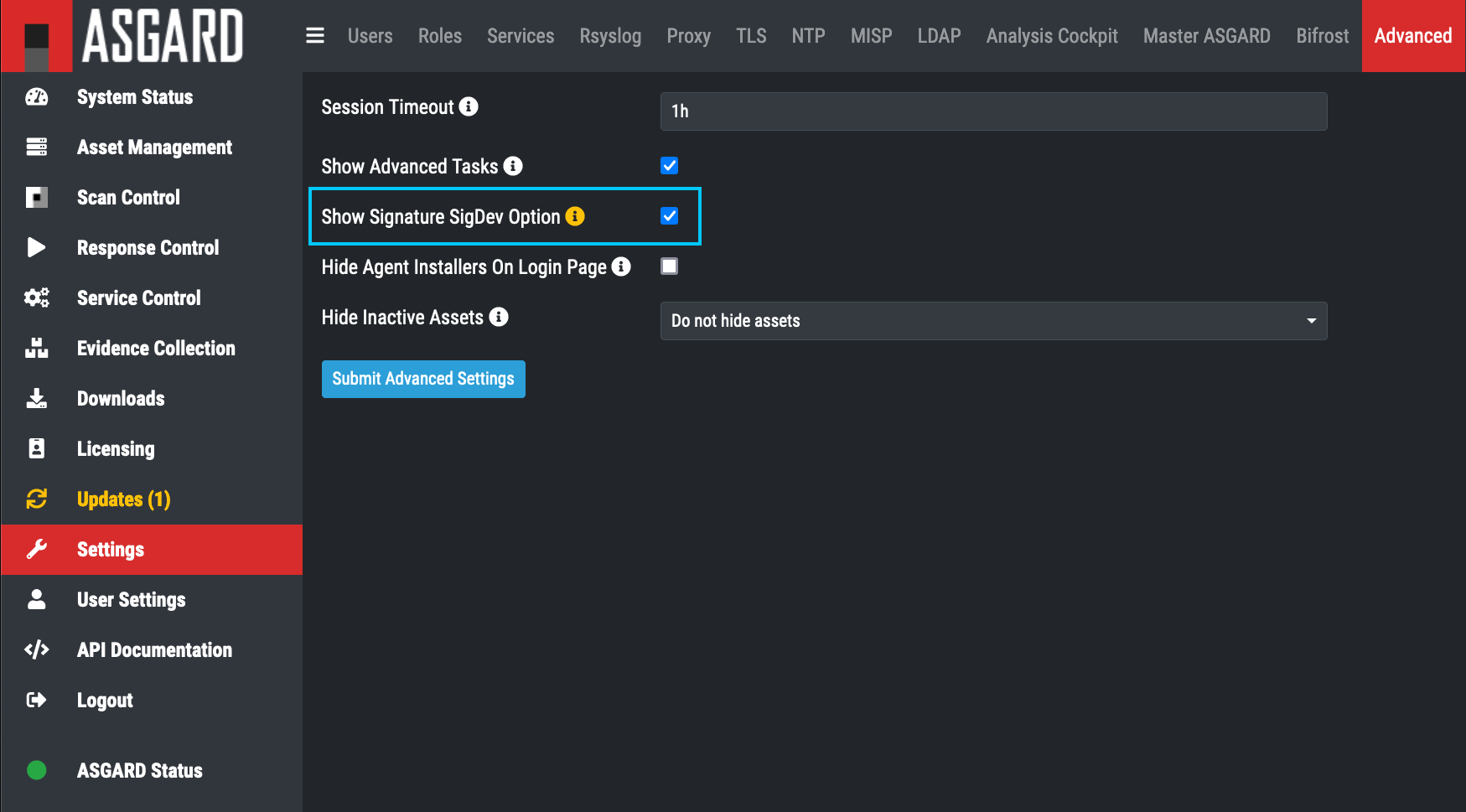
After changing the setting, new scans show an additional option in the dropdown menu.
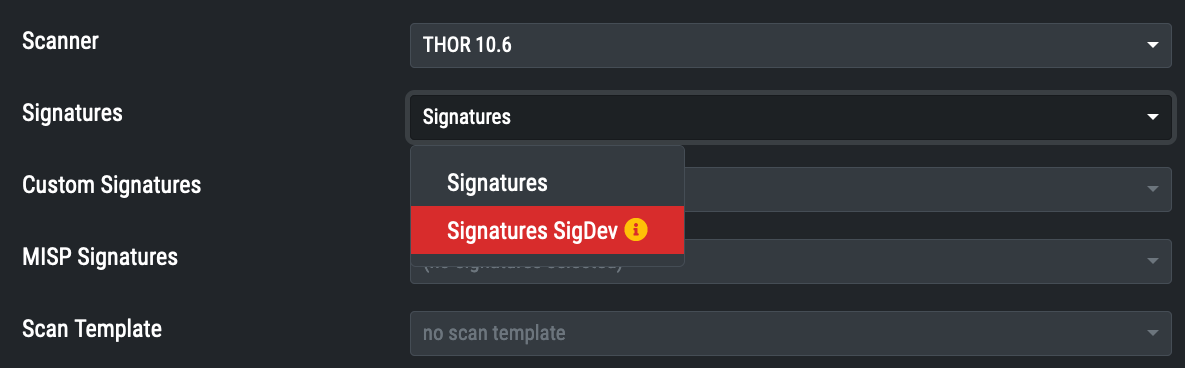
Please contact our support in case of any questions.
THOR Users
Users of our scanner THOR also need to use the signature version that’s in development to get the newest signatures that detect log4j exploitation.
Retrieve that signature pack with:
thor-util.exe update –sigdev