In a report published on the 20th of December CrowdStrike published a report of a new technique exploiting the Microsoft Exchange vulnerability called ProxyNotShell. The called the new technique OWASSRF as it uses Outlook Web Access, CVE-2022-41080 and CVE-2022-41082 to achieve remote code execution (RCE).
PaolAlto Networks’ Unit42 released their report one day later.
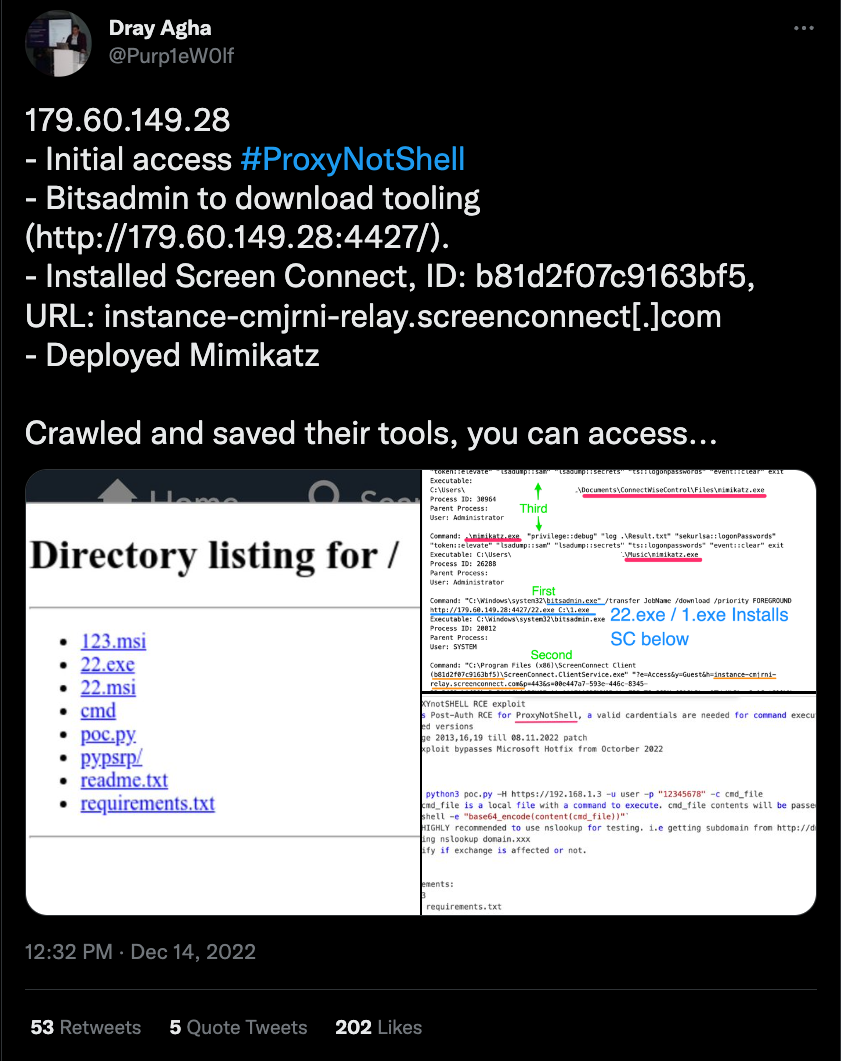
Dray Agha's Tweet
The security researcher Dray Agha noticed the proof-of-concept (POC) in an unprotected open directory used by an unknown threat actor
CrowdStrike's Report on OWASSRF
The report contains information on the exploitation, log patterns and a script to detects possible exploitation attempts
Unit42's report on OWASSRF
PaloAlto Networks Unit42 also published a report that also contains information on observed TTPs and information on a PowerShell backdoor called SilverArrow
Signatures That Detect This Attack
Exploitation
YARA (public)
SIGMA (public)
Potential OWASSRF Exploitation Attempt – Proxy
UUID: 1ddf4596-1908-43c9-add2-1d2c2fcc4797
Potential OWASSRF Exploitation Attempt – Webserver
UUID: 181f49fa-0b21-4665-a98c-a57025ebb8c7
Post-Exploitation
SIGMA (Private)
Microsoft Exchange ProxyNotShell Exploit
UUID: df23d4fb-b12b-4425-a340-8d59e2460c43
Webshell Detection Suspicious Children
UUID: 9a8e8057-32a7-432d-bf80-197dacf1a77f
Shells Spawned by Web Servers in Process Tree
UUID: 6dc0f4e1-7a11-429f-b240-d9f852cea8b3
SIGMA (Public)
Suspicious File Drop by Exchange
UUID: 6b269392-9eba-40b5-acb6-55c882b20ba6
Shells Spawned by Web Servers
UUID: 8202070f-edeb-4d31-a010-a26c72ac5600