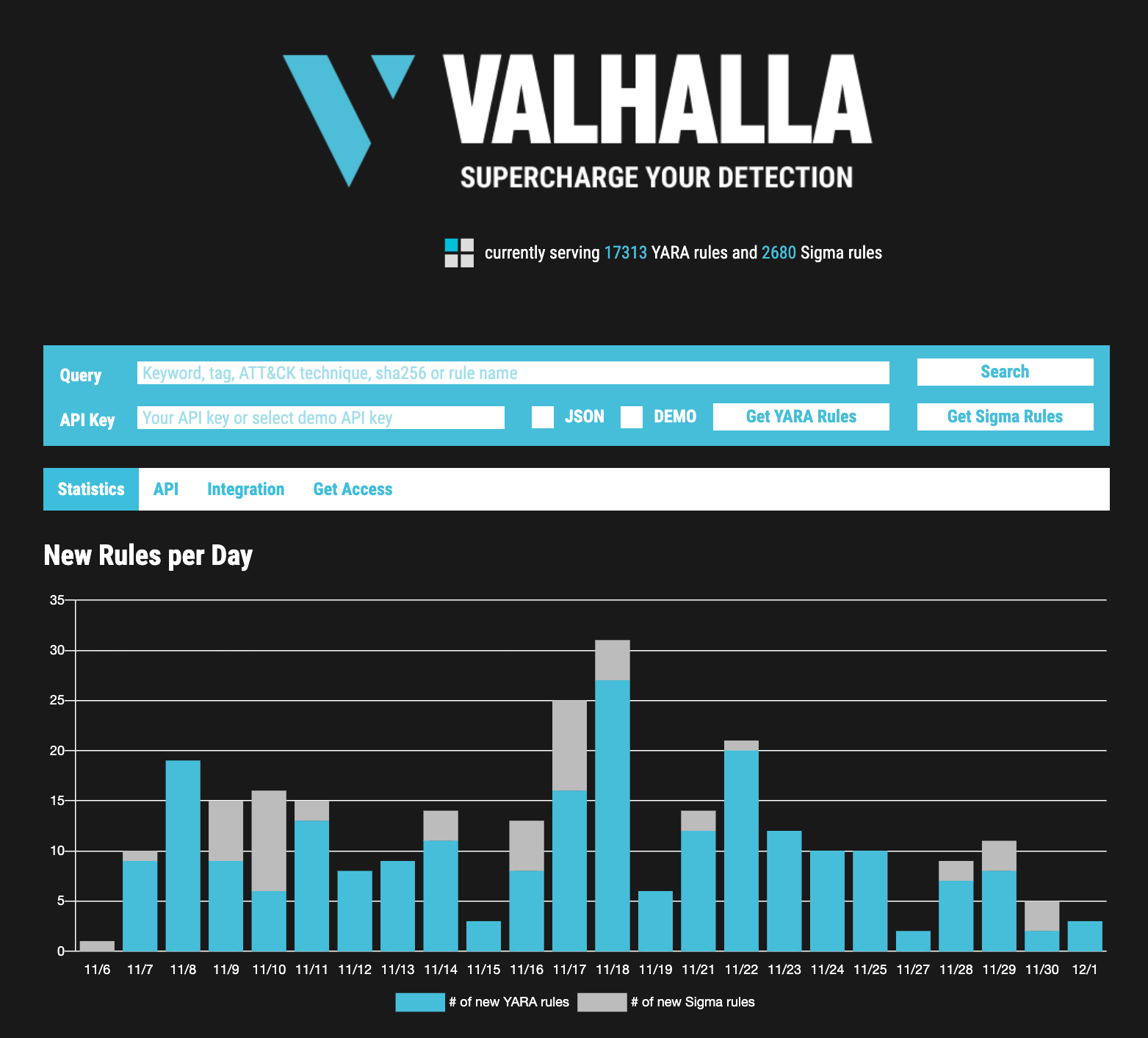
Nextron Systems has always supported the Sigma project, investing hundreds of work hours into creating and maintaining the community rules shared in the public Sigma rule repository. Apart from the community support, we’ve created a set of internal detection rules for our products, THOR and Aurora, that we kept confidential for various reasons and didn’t share publicly.
Today we are glad to announce that we’ve started feeding these rules into the Valhalla service.
Similarly to the YARA feed, we’ve integrated all types of Sigma rules, publicly shared and private rules.
Using the “demo” API key, you can retrieve all public rules in a structured form from Valhalla.
The private Sigma rule feed contains 190 Sigma rules at the date of this blog post and is expected to grow by 600 rules every year. The following table from the front page of the Valhalla web service shows the different categories and the number of rules per category.

The Sigma rules can be retrieved in plain text or JSON format.
The JSON format allows users to filter or select based on certain values without parsing the rules, e.g., “only select rules that have been modified in the last 7 days”.

Getting started
We offer the Sigma feed subscription independently of the YARA rule subscription at a much lower price. If you’re interested, please get in touch with your sales representative for pricing information or fill out this form.