We’re glad to announce a new feature that allows users to enrich events generated by THOR with information from Virustotal.
The feature is available in the full THOR v10.7 TechPreview and THOR Lite.
It can be used in any scan mode: live endpoint scanning, lab scanning, dropzone mode, or even with THOR Thunderstorm.

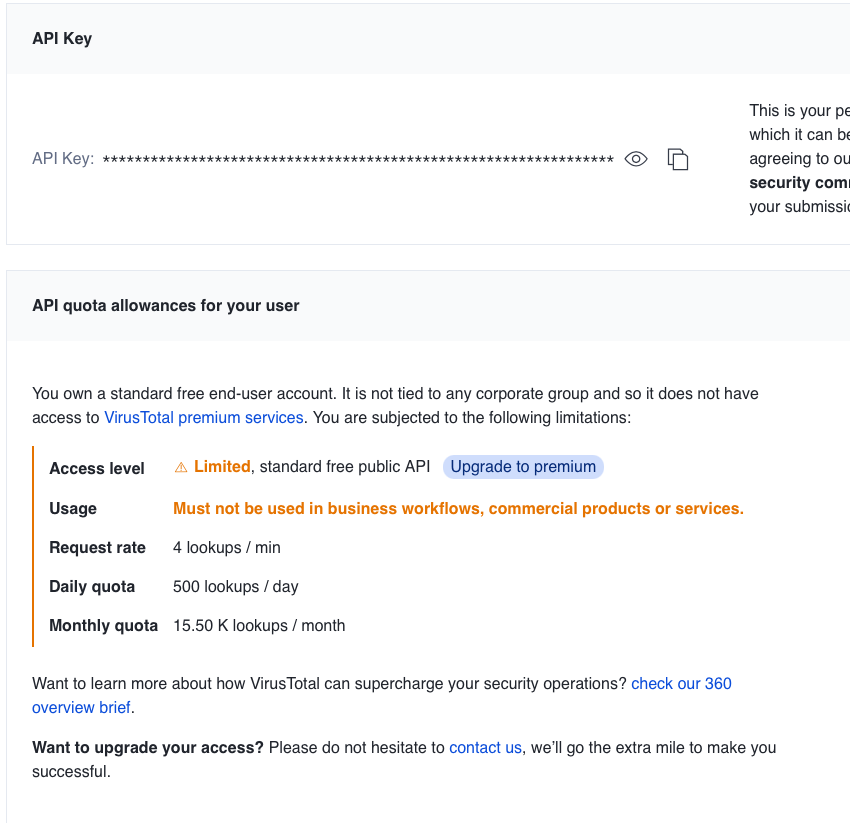
Virustotal Account
You can use it with a Virustotal Enterprise account or even a free account that requires registration.
The free account limits the number of requests per minute, but since THOR only checks findings with a particular score, only a few files are checked.
By default THOR skips the enrichment when the quota is exhausted. The flag “–vtwaitforquota” can be used to make him wait for more quota.
Command Line Flags
The following command line flags are available:
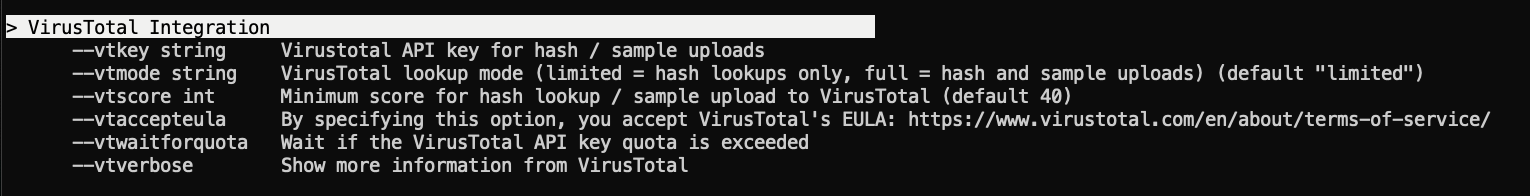
Two lookup modes are available:
- Limited = hash lookups only (default)
- Full = hash lookup or sample upload (if hash is unknown)
A typical command line using the new feature would look like this:
thor64.exe --vtaccepteula --vtkey fb2c3babb1796f97dcd0a877e05207294110bea8a9b93a933b...
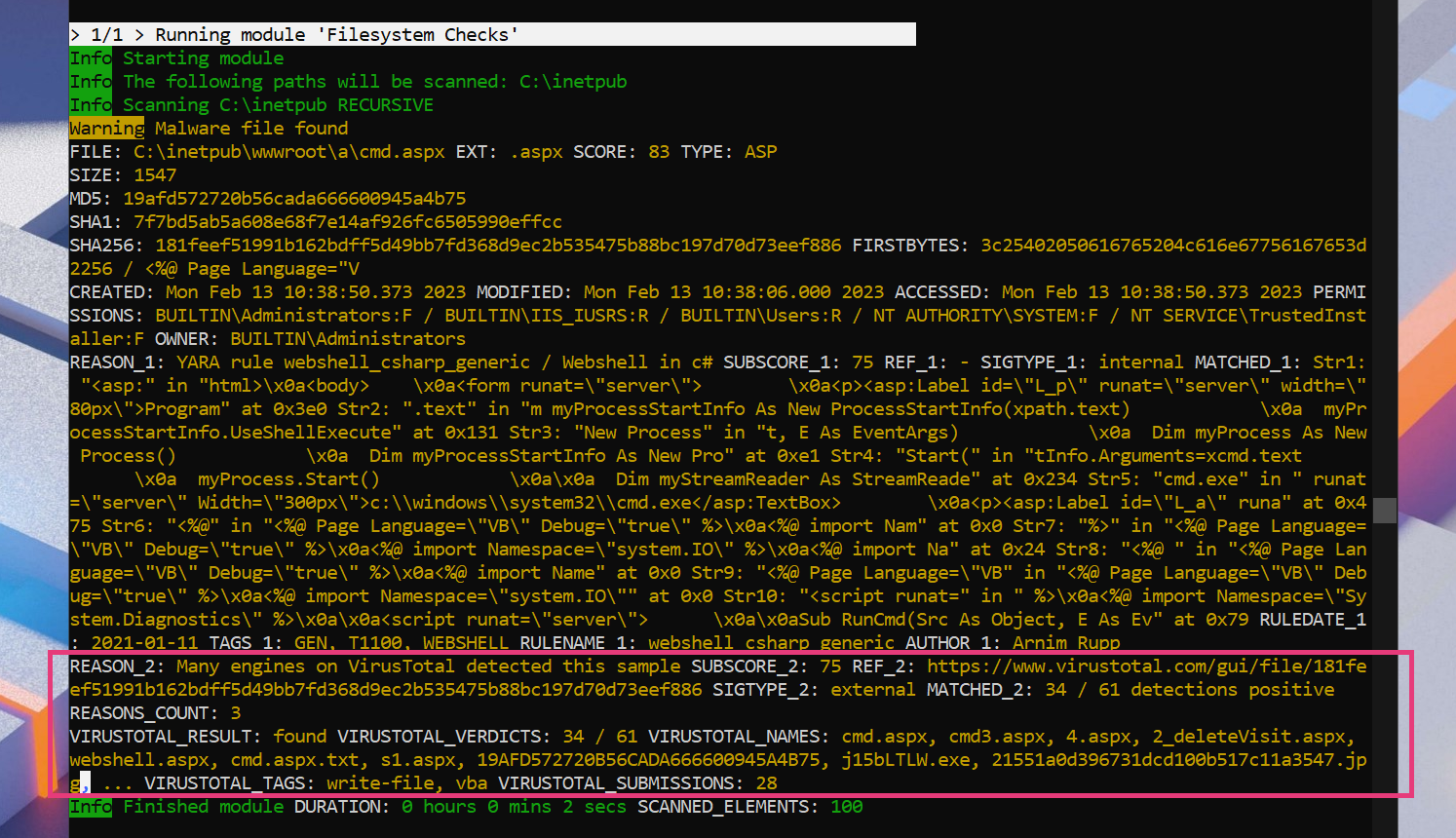
Example Match with Virustotal Information
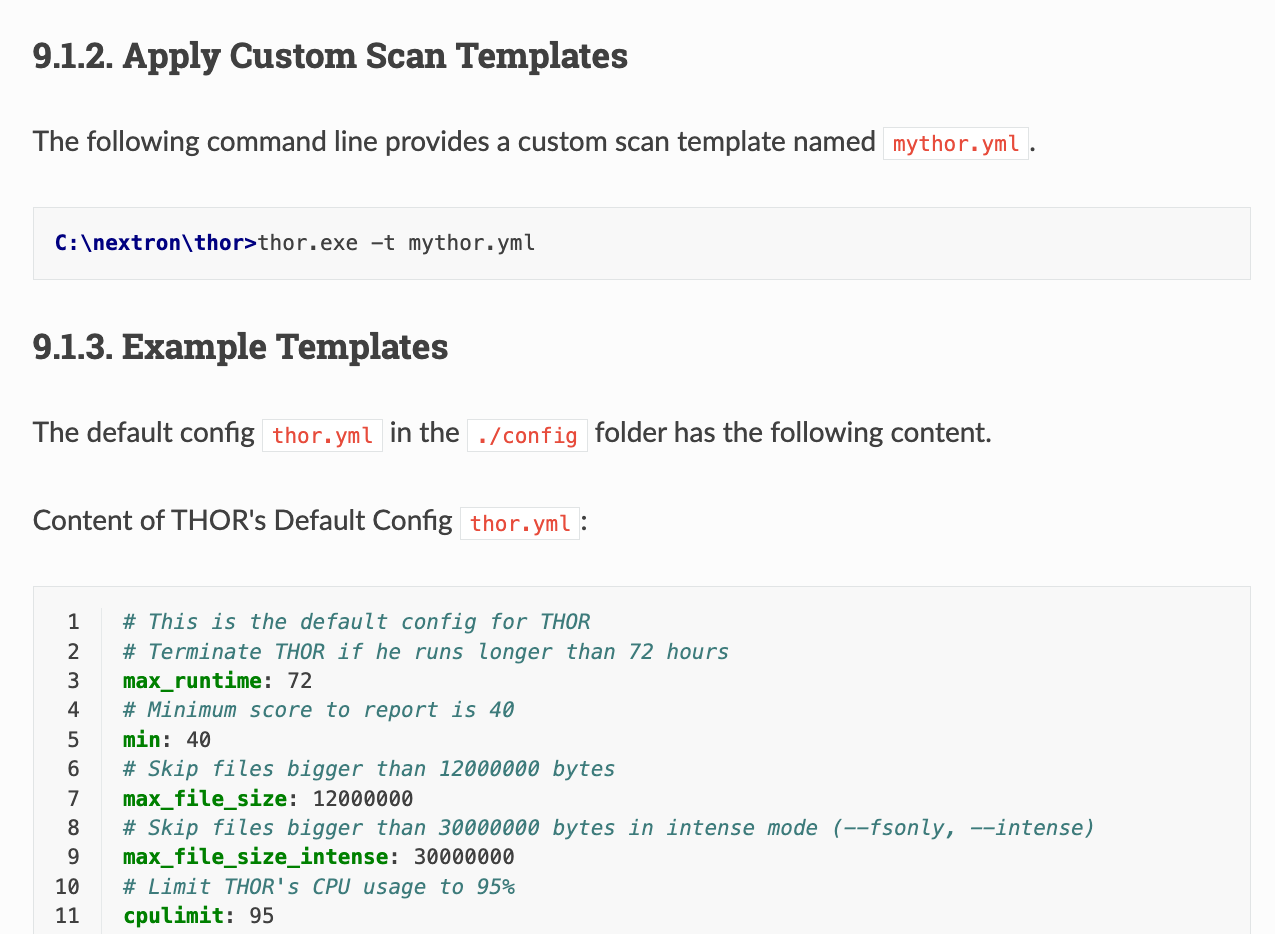
Use API key in Scan Templates
Remember that you can make use of scan templates to avoid exposing your secret API key in command line flags.
Extending Coverage
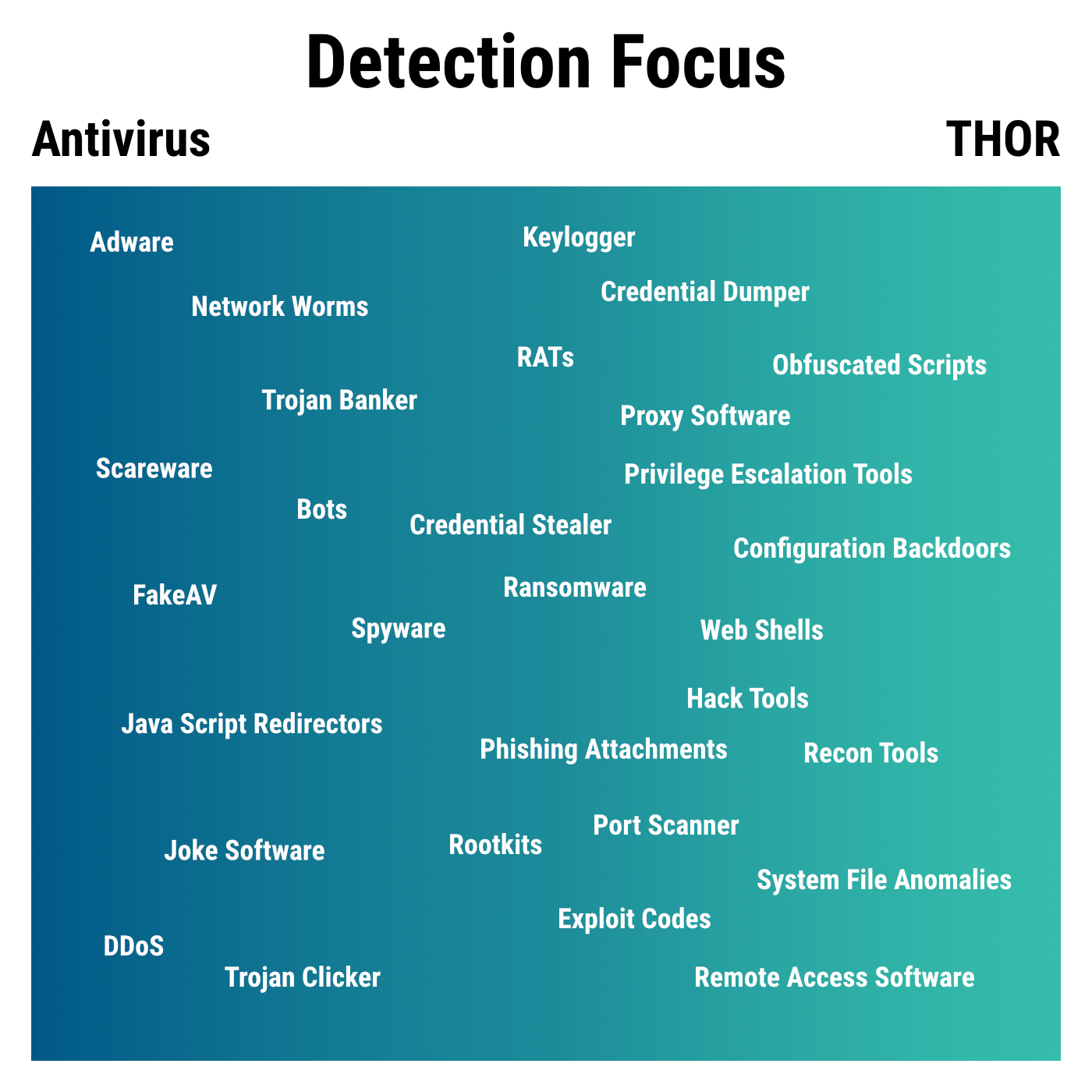
You may already know that THOR focuses on different types of threats and handles findings differently than Antivirus software.
The additional Virustotal lookups allow us to:
- increase the level of a finding that THOR would otherwise have mentioned only as ‘noteworthy’ or not at all
- enrich the existing alert message with information found on Virustotal to confirm the finding
Inspiration
The new lookup feature allows for some exciting detection ideas, which combine YARA rule matching and Virustotal lookups.
YARA as Preselector for Uploads
This idea could be helpful in the case in which you know that an actor makes use of compiled Go (Golang) binaries. You could write a YARA rule that detects all compiled Go binaries for the Windows platform, set a score of 40 (noteworthy) to let the new feature pick them up, and submit them to Virustotal for analysis. (remember that you can use the –customonly flag to only apply your custom YARA rules if needed)
Check New Files with Virustotal
Imagine that you want to check all new .aspx files dropped on an MS Exchange server. You could write a YARA rule that looks for certain contents or the file extensions .aspx and give that rule a score of 40. You could then run a THOR scan on MS Exchange server setting the –lookback flag with the number of days you want to include and instructing it to scan only the C:\inetpub folder. If you schedule this scan to run daily, you will let THOR find all .aspx files changed during the last 24 hours, scan them with its own rules and check them on Virustotal for a verdict of 60+ scan engines. It’s hard to imagine better coverage for web shells than this.
The full command line would look like this:
thor64.exe --vtaccepteula --vtkey fb2c3babb1796f97dcd0a877e05207294110bea8a9b93a933b... --lookback 1 -p C:\inetpub
FAQs
Does a low Antivirus detection rate reduce the score of the THOR matches?
No, that wouldn’t be smart, as THOR focuses on other types of threats that Antivirus software often is unable to detect. However, positive Antivirus matches increase the score for a scanned file depending on the number of Antivirus engines with matches.
THOR adds the following sub-scores based on the lookup result:
- more than 5 engines with matches > score 40
- more than 10 engines with matches > score 60
- more than 20 engines with matches > score 75
What happens when the quota for lookups per minute exceeds?
THOR will not add additional information to the printed event. By default, the lookups will not slow down the scan significantly. If you see too many notice or warning level messages in your environment, adjust the --vtscore value or filter out some known false positives using the false_positive_filters.cfg file.
Can I use this feature with the free THOR Lite version and a free Virustotal account?
Yes.
Which THOR modules trigger a Virustotal lookup?
Basically, only the ‘FileScan’ module uses the lookups. But since THOR also triggers a file scan on the image file during ‘ProcessCheck’, other modules also benefit.
Where can I register a Virustotal account?
Visit this link to register a free account.
How can I get THOR Lite?
You can download THOR Lite here.
Get the full THOR version
Apart from the usual advantages of the full THOR version over THOR Lite, there are a few more reasons to use the full version in this scenario:
- Much bigger number of so-called “threat hunting” rules with low scores that would trigger a Virustotal Lookup
- Multi-threaded scanning significantly reduces the scan duration
If you’re interested in the full version, contact us using the “Get Started” button in the upper right corner.









