We are proud to announce the integration of our private Sigma rule set in Valhalla. This rule set is used in our scanner THOR and endpoint agent Aurora.
The rule set currently contains more than 250 quality-tested and generic rules written by Nextron’s detection engineering team.

Valhalla Front Page Now Shows Sigma Rule Information
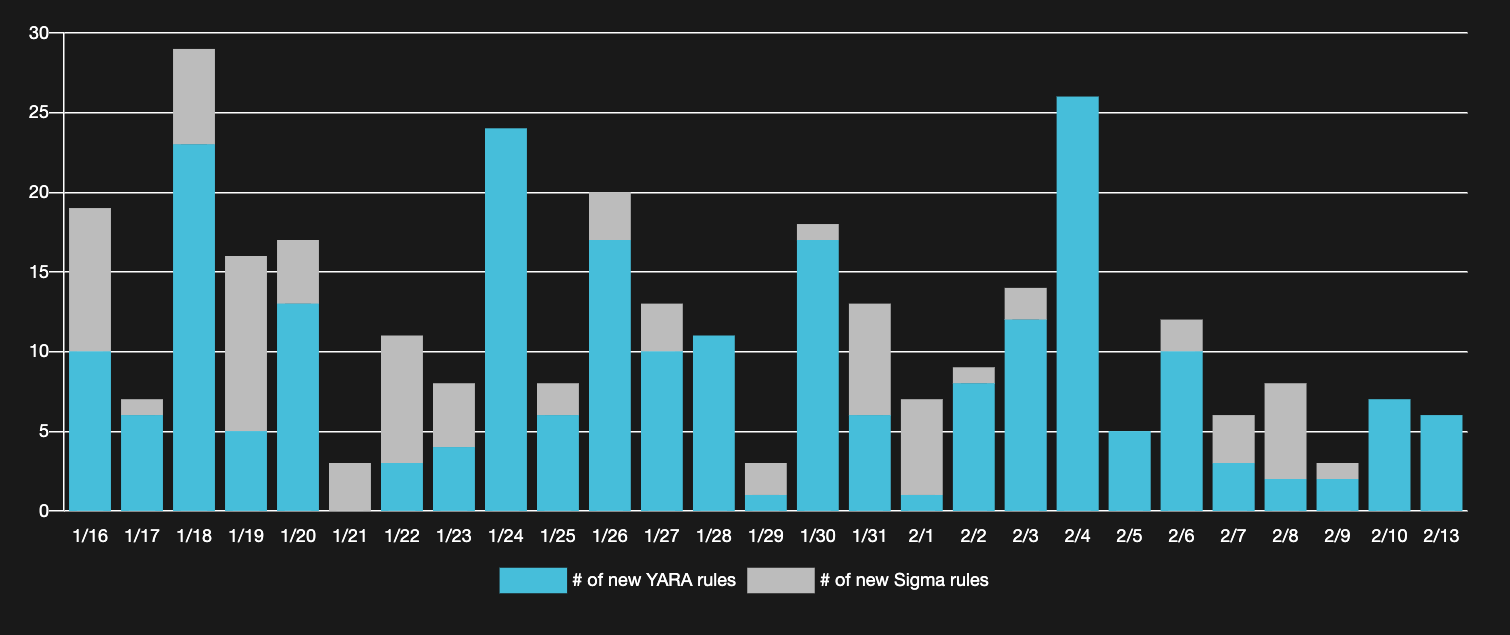
The Valhalla front page already shows Sigma rule information. The grey bars show the number of new Sigma rules created per day.
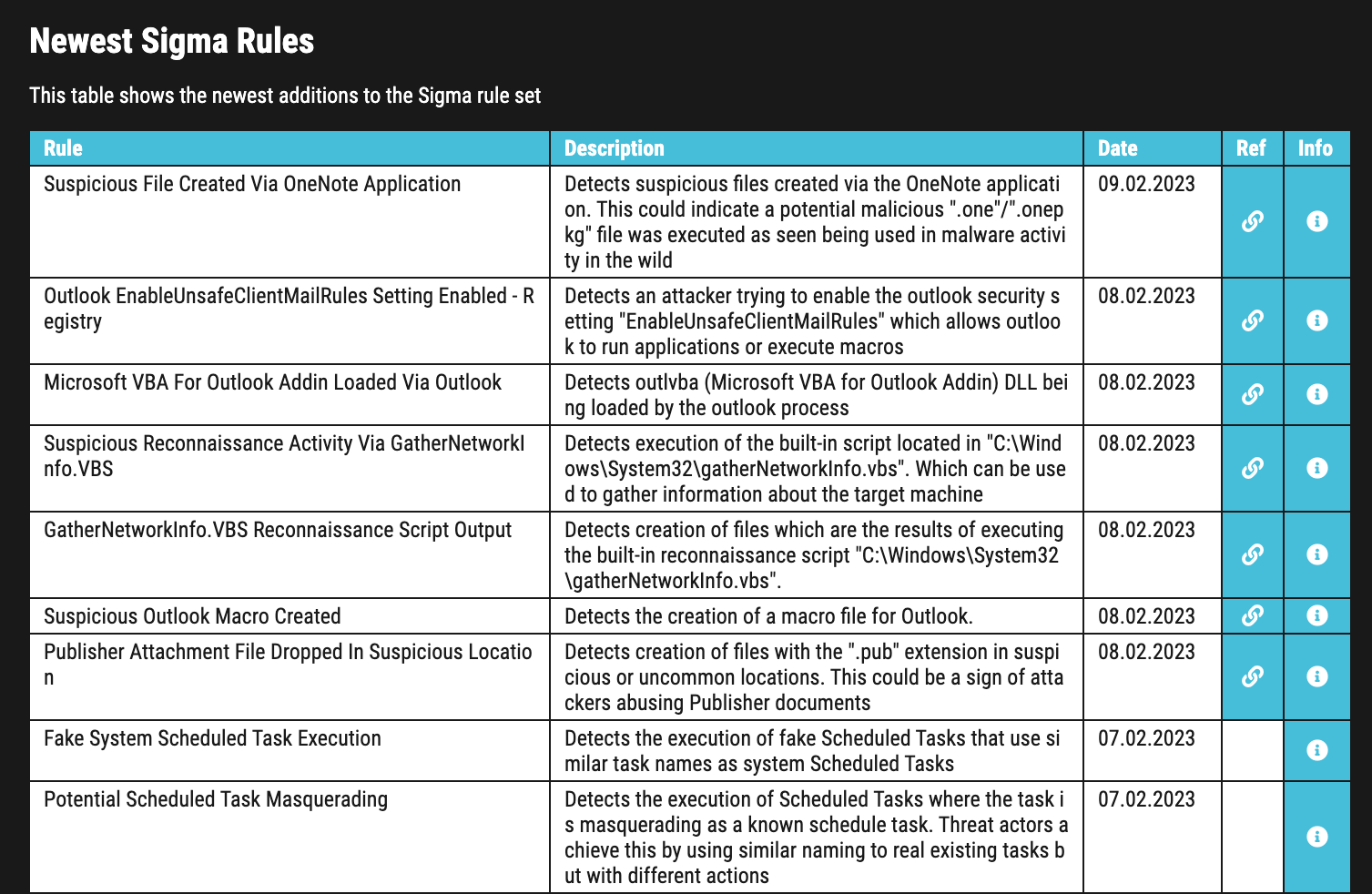
Two new tables on the front page list new Sigma rules and the rule categories. The first table contains new rules with rule title, description, creation date, a reference link and an info page.
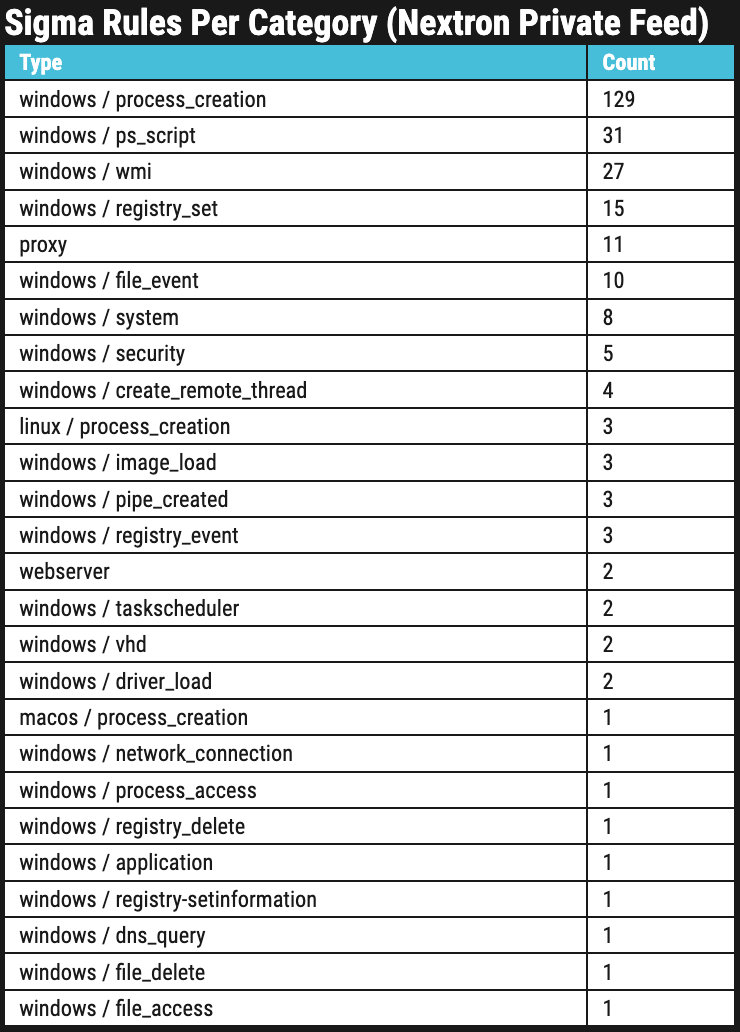
The second table on the front page shows for which type of log source the rules have been written for.
This can help you decide if the contents of the feed align with the log data your organisation collects.
Feed Characteristics
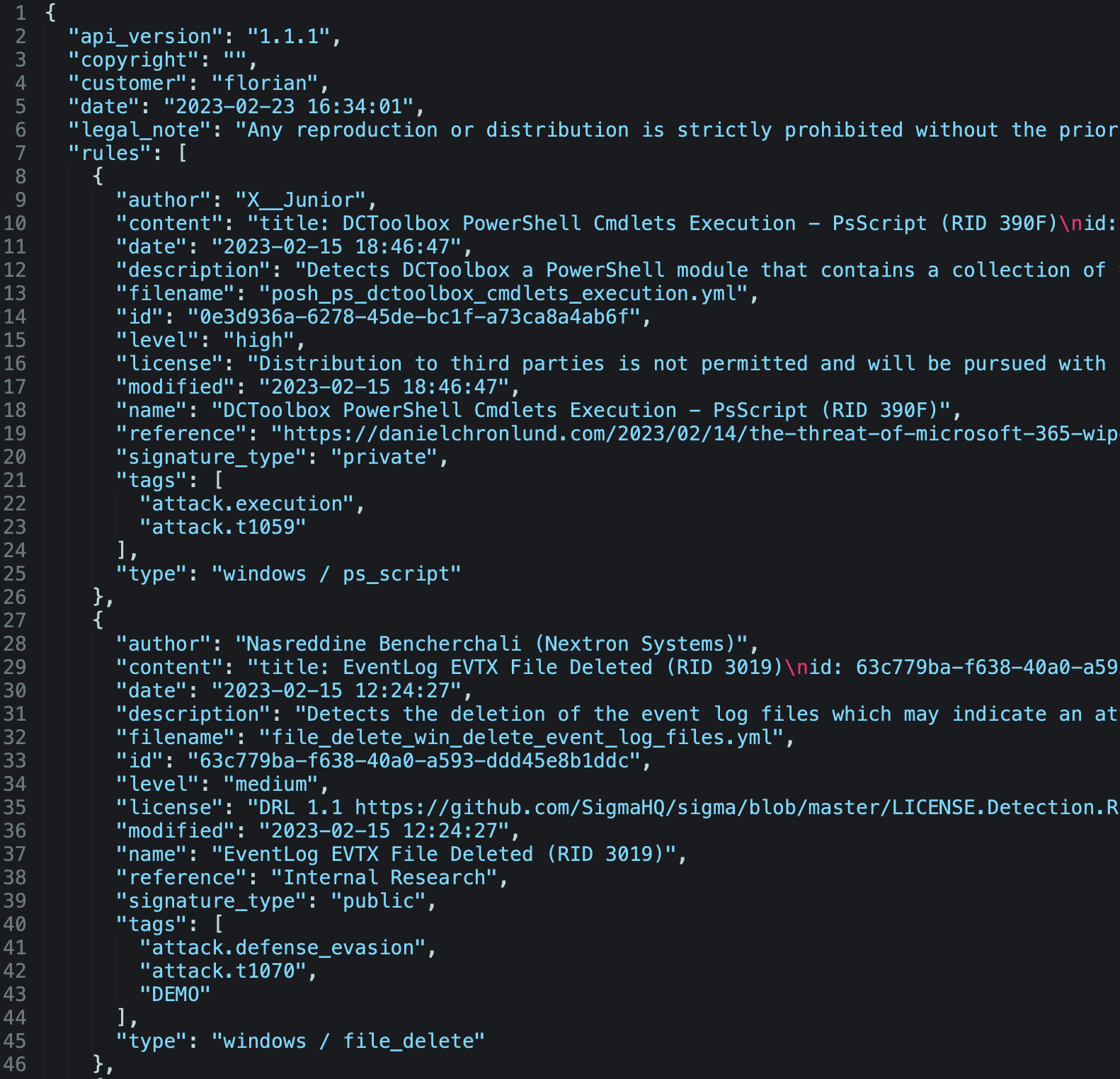
The feed can be requested as a ZIP archive, which contains all rules in separate files or in form of one big a JSON file.
The rules included in the feed share the following features:
- Each rules went through several stages of internal quality testing
- Each rule is tagged with the current MITRE ATT&CK® techniques
- Most of the rules use a more or less generic detection logic focussing on methods and not on tools
The feed is offered in a form that facilitates filtering of the rules based on levels, type or keywords.
Future versions of the feed will include usage and false positive statistics based on anonymised data collected through Nextron Systems’ MSP partners.

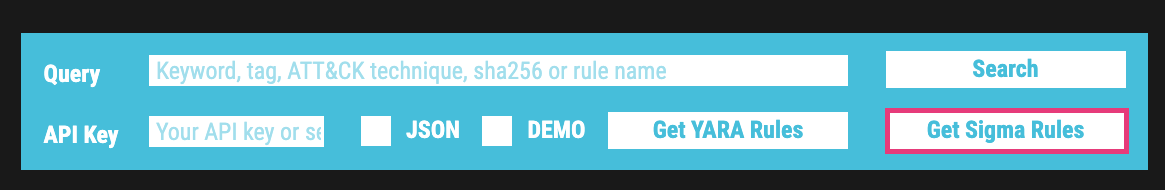
Web Access and API
The feed can be retrieved from the web page using the respective form on the Valhalla front page. Using the “demo” key, you can get the rules maintained in the public sigma repository in the streamlined form in which we offer all our rules.
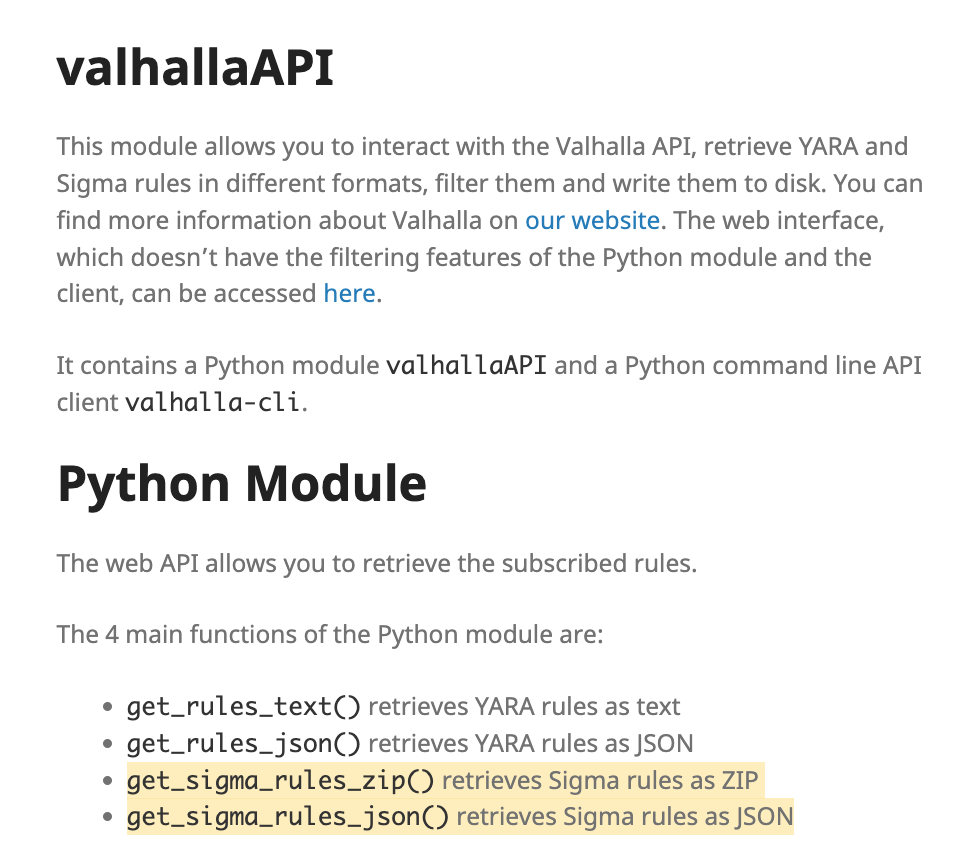
The Python module “valhallaAPI” has been updated to support the new Sigma rule feed.
Partnership with SOC Prime
We are also excited to announce that we have entered into a partnership with SOC Prime, a renowned threat intelligence and cybersecurity content platform.
As part of this collaboration, Nextron’s detection rules will be made available in SOC Prime’s threat detection rule marketplace, providing SOC Prime’s customers with access to a wider variety of rules for identifying potential security threats. Nextron will be the first B2B partner to participate in this program, with their feed accessible to SOC Prime’s customers after a subscription update.
We believe that this partnership will provide significant value to both Nextron and SOC Prime’s customers by enhancing their ability to detect and respond to cyber threats.