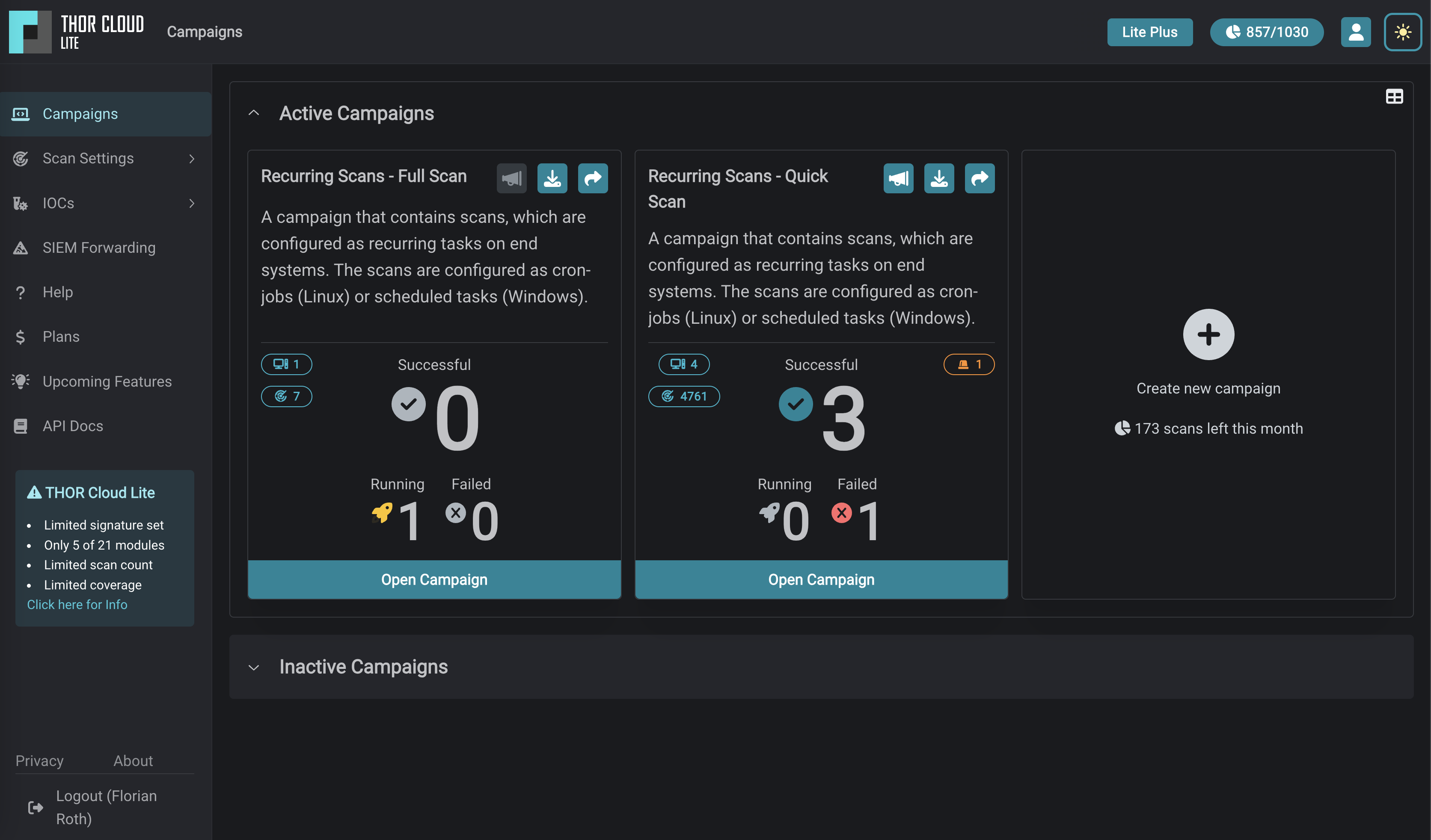
We just launched THOR-Cloud Lite our new free, lightweight and easy to deploy on-demand compromise assessment scanner. Allowing you to access your scans and reports from everywhere at any time. Licensing, scan campaigns and reports everything is conveniently managed in the new web-based user interface.
Easy Setup – Powerful Features
Previously scanning with THOR required manual setup and additional on premise systems. With THOR Cloud we completely eliminated the need for on premise systems and additional agents. The entire client setup is handled by the new THOR Cloud launcher, a single application to setup the THOR scanner on your devices.
The THOR scanner includes over 20,000 pre-built signatures designed to detect various traces of hacking activity, THOR ensures thorough analysis and the identification of potential security threats. THOR and the THOR Cloud launcher support Windows, Linux and MacOS, to ensure coverage for all kinds of environments.
Campaigns are managed through our web-based interface, allowing for easy configuration and convenient management from a centralized location. The campaign overview shows scan status, results for current and previous scans allowing for quick initial assessment. Campaigns offer a variety of options like setting up one-time or recurring scans.
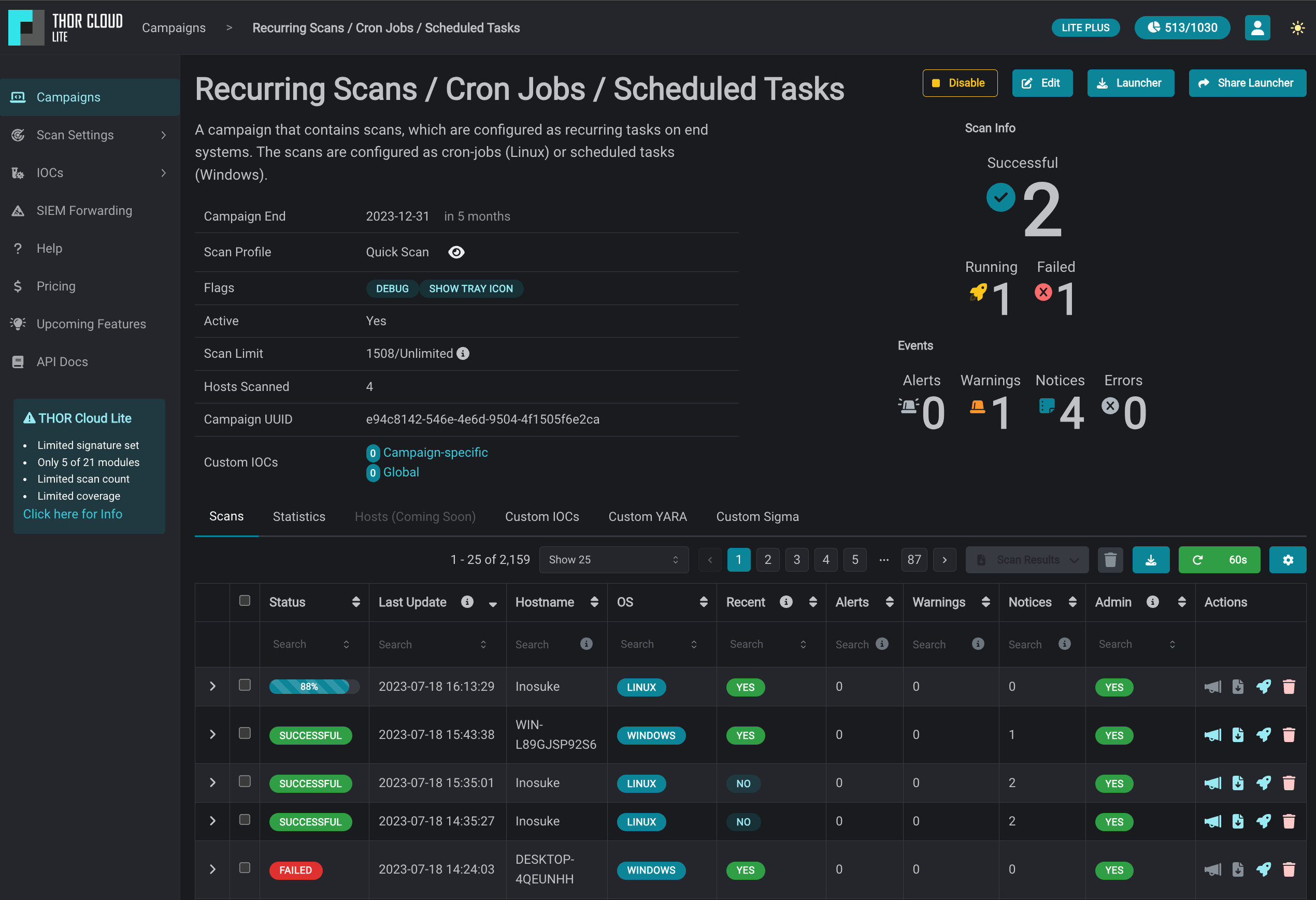
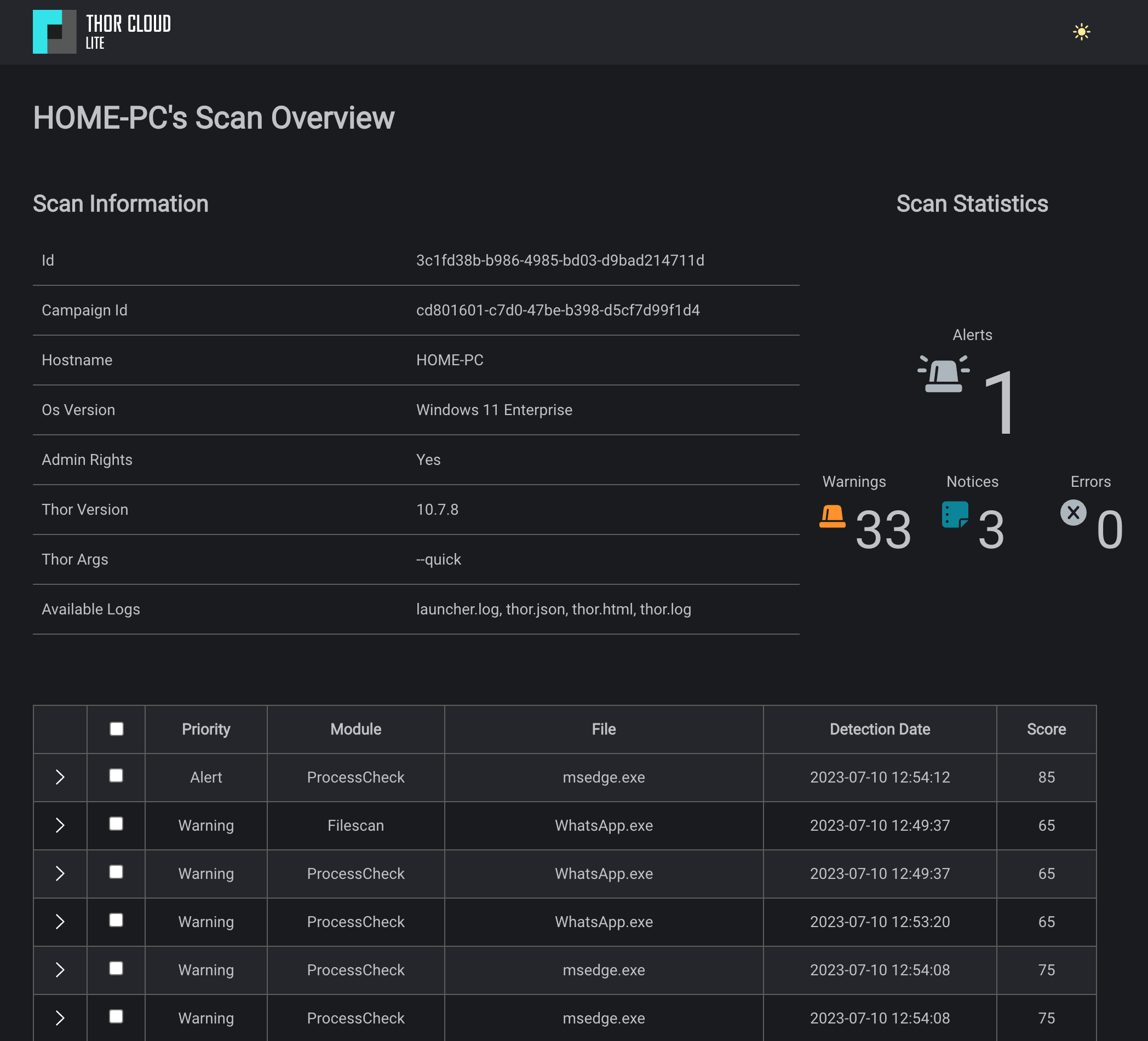
THOR Cloud’s scans offer in-depth insights, serving as a valuable second opinion on security events. Each scan generates various output files, including an HTML report that provides a prioritized view of the scan log.
This helps analysts quickly investigate and qualify security events, which can expedite analysis, reduce the need for further manual investigations, and optimize resource allocation. Thereby making it an ideal extension to support your SIEM or EDR analysts.
Easy To Use And Integrate
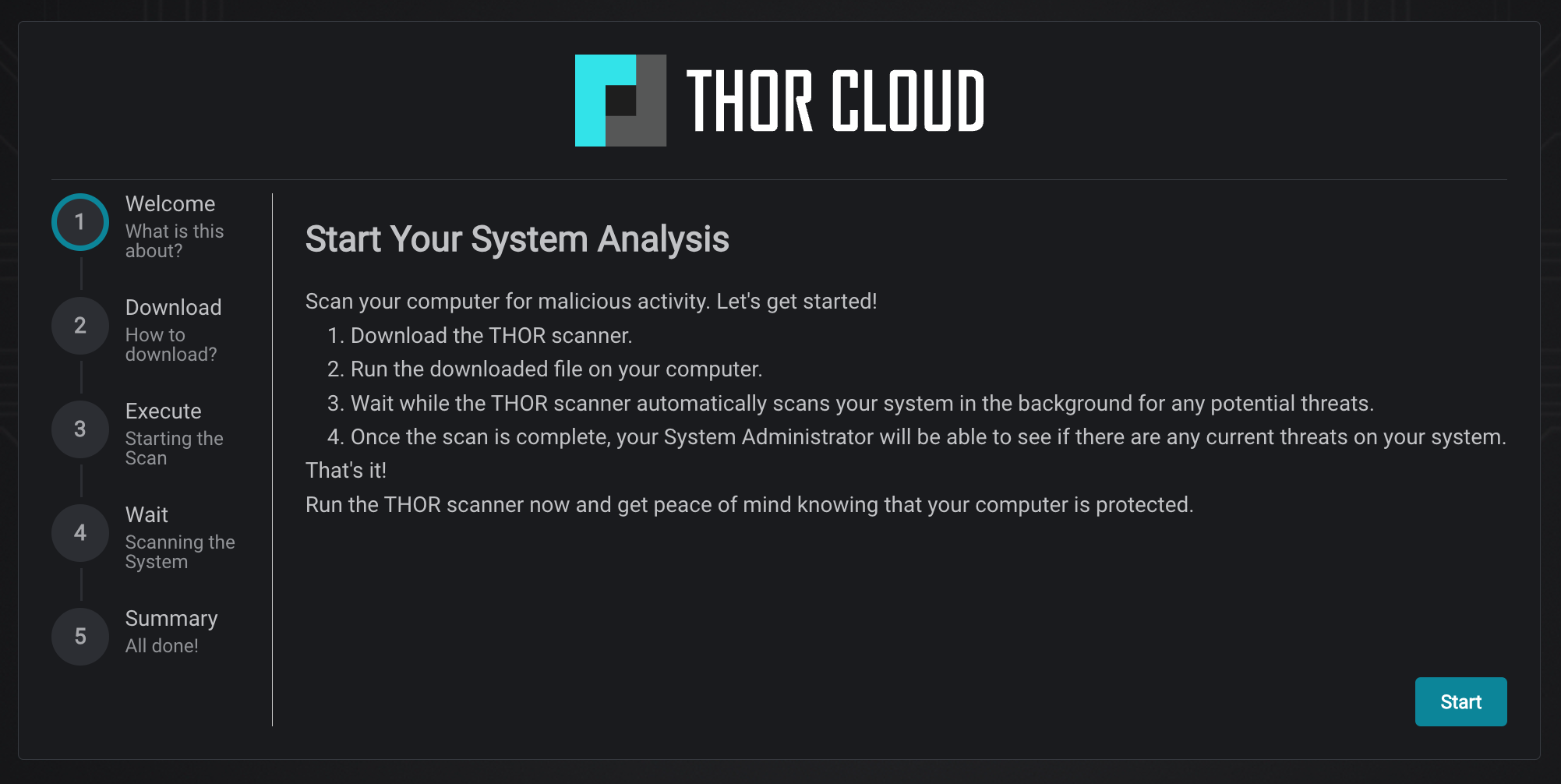
THOR Cloud is built with usability and accessibility in mind, offering step by step guides and extensive documentation for end users and developers. With the guided setup you can simply follow along to deploy THOR Cloud in your environment without any prior knowledge.
All features present in the interface are easily accessible via an API, ensuring seamless integration with your existing solutions, whether you want to automate workflows, integrate with existing systems (SIEM/EDR), or build custom applications. Everything is possible with our powerful API.
Video
In the following recorded video session, we delve into the essence of THOR Cloud and offer a concise demonstration of the platform:
(if you can’t see the embedded video, here is a direct link)
Conclusion & Get Started
In conclusion, THOR Cloud is a game-changer for on-demand security scans and compromise assessments. It offers simplicity, accuracy, and ease of integration, while reducing management and deployment efforts.
Sign up for a free THOR Cloud Lite account here.
The free version of THOR Cloud includes the THOR Lite scanner and the open source signature set. A full version including the enterprise-grade THOR scanner with our full signature set will be launching in Q1 2024.
Check out the THOR Cloud product page for more information.










