THOR version 10.6, which is currently available as TechPreview, introduces several new features that facilitates the use of THOR in a digital forensics lab. Since not all of the features provided with the “Forensic Lab” license type are well-known, we would like to introduce all features that are unique to that special license type in this blog post.
Forensic Lab License Features
- Multi-threaded scanning (improves scan speed significantly on multi-core systems)
- Multi-instance scanning (run multiple THOR processes on a single machine)
- Memory dump scanning (use the so-called DeepDive on dumped data, e.g. memory images)
- Dropzone mode (monitor folder for new files, scan them and generate events)
- Hostname replacement (replace hostname in log messages with a given string)
- Virtual drive mapping (Map a mounted drive e.g. S: to a virtual drive e.g. C: to allow lookups for files mentioned in analyzed entries; more info here)
Multi-Threaded Scanning
Multi-threaded scanning allows users on forensic workstations to make full use of the system’s CPU cores. Multi-threading isn’t available in all modules but the ones with the biggest run time:
- File Scan
- Registry Scan
- Eventlog Scan
It is also available in DropZone mode, which means that dropping dropping 12 files in the monitored folder would create 12 threads scanning these files in parallel.
We plan to refactor the following modules to support multi-threading:
- DeepDive
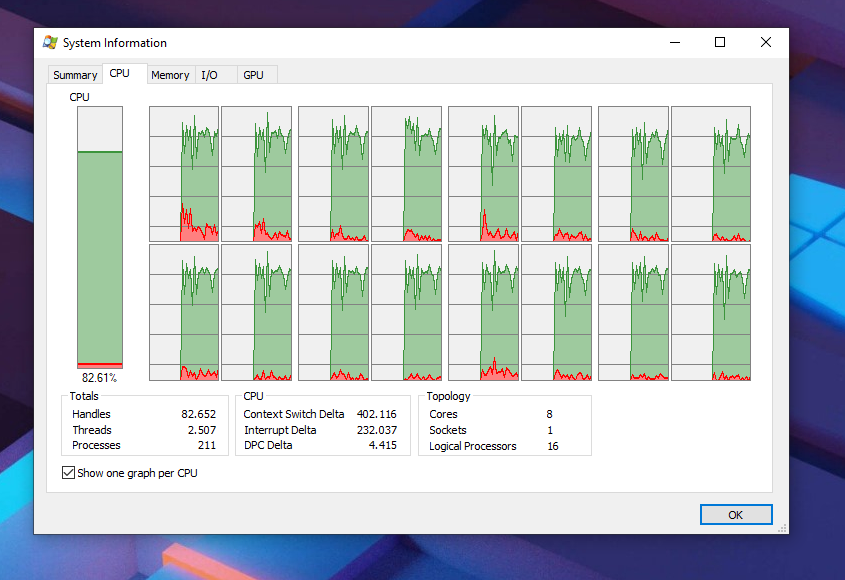
Multi-Instance Scanning
Multi-instance scanning means that you can start multiple executables of THOR on a single workstation.
This is often needed in lab environments to process mounted disk images in parallel and create separate reports for these two cases.
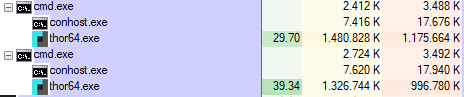
Memory Image Scanning
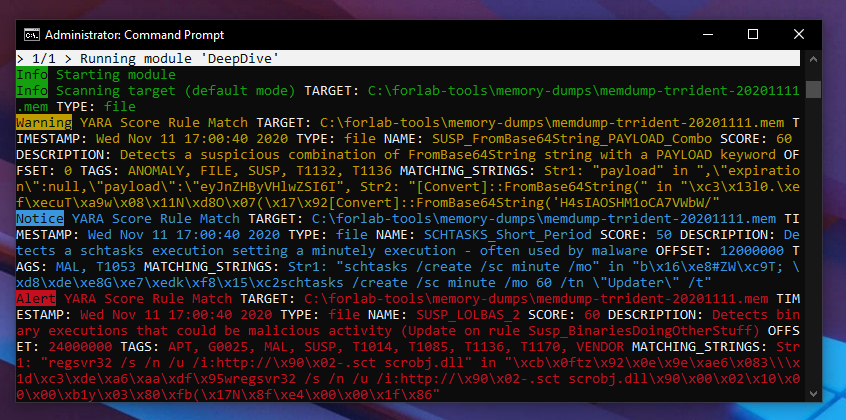
We provide a module named “DeepDive” that analyzes files of any size by reading big chunks of data and applying YARA rules to the chunks of data, showing YARA matches within that data with offset and matching strings / bytes.
It is not meant for the analysis of disk images but memory dumps, crash dumps or even PCAP files.

Dropzone Mode
The drop zone mode allows you to monitor a given folder for new files. All files dropped to that folder will be scanned and then deleted. Customers use text and syslog output to report back findings.
The drop zone mode helps you to integrate THOR in a bigger analysis environment. We recommend dropping files in their original form with the correct filename and extension, since some of the rules make use of these meta data values.
Side note: If you like the idea of a drop zone, you’ll love THOR Thunderstorm.
Other Comfort Features
Other features relate to command line parameters that help you with different aspects of disk image scanning your forensic lab. We’ve added these features over the years based on a lot for feedback from DFIR specialists and BETA program users.










